Posted by Martijn Grooten on Feb 9, 2018
 An article by security researcher Collin Anderson reopens the debate on whether publishing threat analyses is always in the public interest.
An article by security researcher Collin Anderson reopens the debate on whether publishing threat analyses is always in the public interest.
Posted by Martijn Grooten on Feb 8, 2018
 Users of the popular WordPress content management system are urged to manually update their installation to version 4.9.4, as a bug in the previous version broke the ability to automatically install updates.
Users of the popular WordPress content management system are urged to manually update their installation to version 4.9.4, as a bug in the previous version broke the ability to automatically install updates.
Posted by Martijn Grooten on Feb 7, 2018
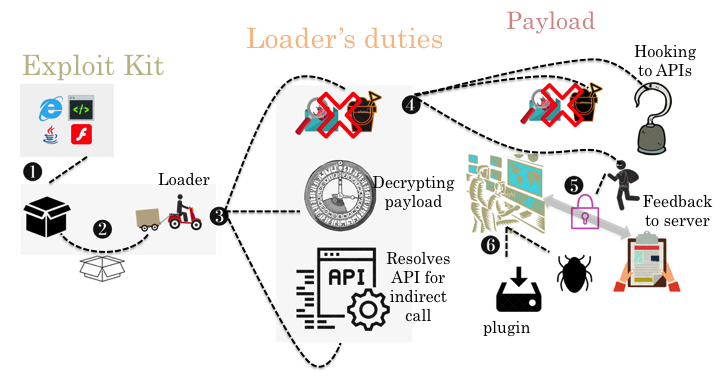 The Andromeda botnet (aka Gamarue or Wauchos) has plagued Internet users for more than half a decade but, following a takedown effort and the arrest of the suspected botnet owner in December 2017, it is likely we have seen the end of it. In a new paper by Fortinet researchers Bahare Sabouri and He Xu, we look back at the evolution of Andromeda from version 2.06 to 2.10 and demonstrate both how it improved its loader to evade automatic analysis/detection and how the payload varied among the different versions.
The Andromeda botnet (aka Gamarue or Wauchos) has plagued Internet users for more than half a decade but, following a takedown effort and the arrest of the suspected botnet owner in December 2017, it is likely we have seen the end of it. In a new paper by Fortinet researchers Bahare Sabouri and He Xu, we look back at the evolution of Andromeda from version 2.06 to 2.10 and demonstrate both how it improved its loader to evade automatic analysis/detection and how the payload varied among the different versions.
Posted by Martijn Grooten on Feb 2, 2018
 Reports of malware using the Meltdown or Spectre attacks are likely based on proof-of-concept code rather than files written for a malicious purpose.
Reports of malware using the Meltdown or Spectre attacks are likely based on proof-of-concept code rather than files written for a malicious purpose.
Posted by Martijn Grooten on Feb 1, 2018
 This Throwback Thursday, we republish the VB2012 paper by Microsoft researcher Amir Fouda, one of the earliest papers to look at malware targeting Bitcoin.
This Throwback Thursday, we republish the VB2012 paper by Microsoft researcher Amir Fouda, one of the earliest papers to look at malware targeting Bitcoin.
Posted by Martijn Grooten on Jan 31, 2018
 We especially encourage those less experienced in speaking in public to submit to the call for papers for VB2018, where we aim to provide a friendly and welcoming environment in which people can both present their own research and learn from what others have been working on.
We especially encourage those less experienced in speaking in public to submit to the call for papers for VB2018, where we aim to provide a friendly and welcoming environment in which people can both present their own research and learn from what others have been working on.
Posted by Martijn Grooten on Jan 25, 2018
 At VB2017 in Madrid, security researcher Randy Abrams presented an overview of the VirusTotal service and then went on to bust several of the persistent myths that surround it. Today we publish both Randy's paper and the recording of his presentation.
At VB2017 in Madrid, security researcher Randy Abrams presented an overview of the VirusTotal service and then went on to bust several of the persistent myths that surround it. Today we publish both Randy's paper and the recording of his presentation.
Posted by Martijn Grooten on Jan 24, 2018
 A new computer emergency response team has been launched in the Netherlands to provide guidance specifically tailored to the healthcare sector. Martijn Grooten welcomes the development.
A new computer emergency response team has been launched in the Netherlands to provide guidance specifically tailored to the healthcare sector. Martijn Grooten welcomes the development.
Posted by Martijn Grooten on Jan 23, 2018
 Have you analysed a new online threat? Do you know a new way to defend against such threats? Are you tasked with securing systems and fending off attacks? The call for papers for VB2018 is now open and we want to hear from you!
Have you analysed a new online threat? Do you know a new way to defend against such threats? Are you tasked with securing systems and fending off attacks? The call for papers for VB2018 is now open and we want to hear from you!
Posted by Martijn Grooten on Jan 22, 2018
 VB Editor Martijn Grooten recommends Jean-Philippe Aumasson's 'Serious Cryptography' as a very solid but practically focused introduction to cryptography.
VB Editor Martijn Grooten recommends Jean-Philippe Aumasson's 'Serious Cryptography' as a very solid but practically focused introduction to cryptography.