Posted by Virus Bulletin on Sep 2, 2013
Files in Prefetch directory supposedly show malware infections.
Support scammers usually claim to call on behalf of Microsoft, or just some IT company with a nice-sounding name, and then use social engineering to make the victim believe their Windows PC is infected with malware. The victim is then talked into paying to have their machine cleaned up.
Although the scammers require access to the PC through a remote-access tool, there is no evidence that they install malware on it. Rather, for a hefty fee, they run some free security tools.
The call I received came from 'PC Wizards', the same company that called me earlier this year - and the fact that they had the same phoney name as I have used in the past in their system, indicates that they used a database of past 'victims', rather than a simple list of residents.
The scam used the Windows Event Viewer to try to convince me there was a problem with my PC. This is a tactic I have seen used many times before: the errors in the Event Viewer, which are usually harmless, are supposedly indications of malware infections.
Once they had been given access to my (virtual) PC, the scammers used two more social engineering tricks that I had not seen before:
They opened the 'Prefetch' folder and told me that the files within it were all pieces of malware. After I pretended to be convinced of the fact that Windows has a special directory in which malware is stored, they took one such file and ran a Google search for its name. The results showed that a file with this name is sometimes used by malware.
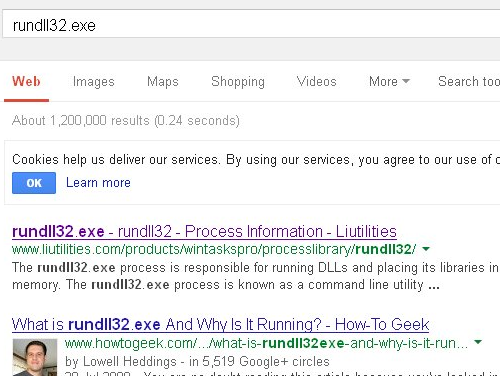
I thought this could easily convince a non-technical user. However, I was less impressed by another trick, which was supposed to prove that the warranty on my machine had expired.
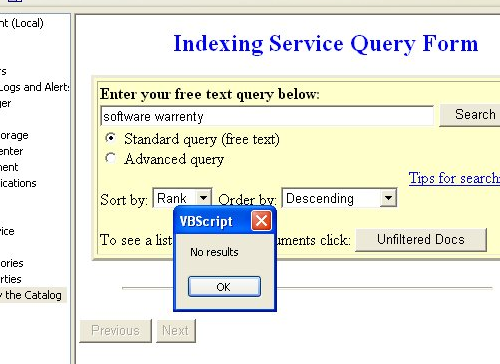
The scammers used the 'Indexing Service' to search for the 'software warrenty' and the fact that it couldn't be found was supposed to prove that my machine was out of warranty. Perhaps this would have been more convincing had they spelled 'warranty' correctly.
When informed about the various payment options, I was told that the one-year plan would be the most suitable for me. This surprised me as, despite costing well over 100 pounds, it was the cheapest of their plans. But perhaps the other plans were merely present to make this one appear inexpensive.
Of course, I politely declined the offer and then, less politely, told them to stop performing such tricks. I doubt they will listen.
A more effective way to help stop the scams is to report them to the police. The scam has been targeting a large number of countries, but those in the UK can report it as 'Computer Software Service fraud' on the Action Fraud website.
Posted on 2 September 2013 by Martijn Grooten