Posted by Virus Bulletin on Sep 9, 2013
Short campaign could have had desired effect.
Pump-and-dump spam is almost as old as spam itself: emails are sent out promoting worthless 'penny stocks', which have been purchased by the scammers before the start of the campaign. The hope is that the hype contained in the emails will encourage others to invest in the stock, thus driving in an increase in stock price and a resulting in a profit for the scammers.
Like any kind of spam, pump-and-dump spam clogs up inboxes and mail servers, while as an unwanted side-effect of spam filters trying to block them, legitimate emails mentioning the stock market may be blocked.
After having been all but absent for years, this type of spam has made a comeback in 2013, causing some to wonder if this could be a sign of economic recovery.
In a new campaign seen over the weekend, pump-and-dump spam took a slightly disturbing twist. To "enrich themselves by means of war", recipients are tipped to buy stocks in a company that trades in mining claims - apparently, their prices will go up once oil prices increase following the dropping of bombs.
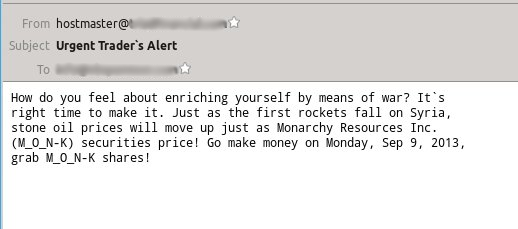
I'm not an economist and I wouldn't know if rising oil prices will result in a rise in stock prices for a company that's in the business of mining precious metals, but I found it a little worrying that, with the opening of the New York Stock Exchange this morning, the value of the advertised stocks had almost doubled, after which it fell almost immediately. This may not be the result of the spam campaign, but it would be exactly what one would expect to see if the campaign had been successful.
The current events in Syria are disturbingly popular among spammers, from fake CNN emails that link to an exploit kit, to targeted campaigns containing a backdoor.
There is good reason to be concerned about what is happening in the country - something which puts the fight against the Internet's bad actors into perspective - but users should be extra cautious before clicking links, or taking action based on things they read in emails.
Posted on 9 September 2013 by Martijn Grooten