Posted by Virus Bulletin on Jan 24, 2014
Unsophisticated scam shows the high level of commoditization of today's cybercrime.
A case of browser-based ransomware, that is currently using social engineering tactics in an attempt to extort money from its victims, shows how even the least sophisticated cases of cybercrime make use of services available on the black market.
Given all the talk about Cryptolocker, one could almost forget that there are other kinds of ransomware plaguing Internet users. Rather than strong encryption, they use social engineering to hold the user's computer to ransom: they claim that a fine needs to be paid for illegal activity before the computer can be used again.
Last night I stumbled upon one such case which, as seems quite typical for 'police ransomware' these days, ran entirely inside the browser.
As malicious activity goes, it is rather unsophisticated. Still, I found it interesting that such a simple scam still used various tricks to improve the stealthiness and success rate of the campaign. I think it unlikely that all of this activity, from hijacking Twitter accounts to hijacking DNS, was performed by the scammers themselves. Rather, I believe that this is an example of the high level of commoditization of cybercrime, where access to any kind of compromised account can be bought on the black market.
The scam was spreading on Twitter, through links posted by legitimate accounts. Various similarities between the tweets led me to believe that the accounts were compromised rather than their owners having been socially engineered into tweeting the links.
The links pointed to a subdomain of appspot.com, which is used by Google App Engine. Among other things, this service lets users register their own subdomain for free.
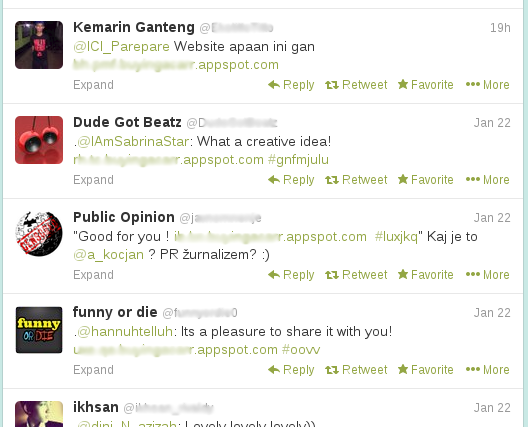
This link then redirected to a second URL, which used a free DNS service and pointed to a server in Turkey. As if to show how popular free DNS services are among cybercriminals, this link redirected to yet another URL, again using free DNS, and pointing to the same server.
From here the user was redirected to the landing page where the ransomware was shown. To make this page look slightly more legitimate, and to avoid detection by domain-based blacklists, the scammers had managed to register the subdomain alert-police for a number of legitimate domains. All the domains I found were registered at the UK-based registrar 123-Reg.
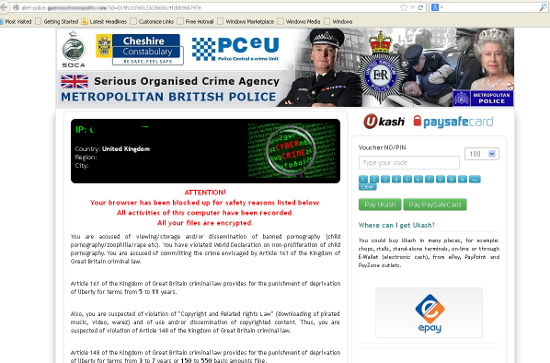
The message displayed in the browser will be familiar to anyone who has been following these scams: the user has supposedly engaged in illegal activity (such as viewing child pornography or zoophilia), which carries a heavy penalty. However, by paying a relatively small fine the user can apparently prove that the activity was 'unintended' and thus avoid prosecution.
As is typical for this kind of malware, the message is displayed in the language and using the logo of the police force of the country in which the user is based. Lack of sophistication on the side of the scammers allowed me to grab the various logos used, which I posted here.
These are the same logos as were posted by security researcher Kafeine last year. Kafeine, who has been closely following police ransomware for several years, told me that this scam is operated by the group behind 'Reveton'.
However, unlike Reveton itself, this ransomware operates entirely inside the browser. This could help evade detection by anti-virus software that only looks at changes on the file system. At the same time, it means the ransomware relies entirely on social engineering, although a hundred iframes are used give the impression that the site cannot be closed.
We reported the compromised domain names to 123-Reg, who took quick action and removed the relevant DNS records. The provider where the ransomware is hosted has also been contacted.
Posted on 24 January 2014 by Martijn Grooten