Posted by Virus Bulletin on Aug 22, 2014
James Wyke looks at four difference decoy methods.
In the weeks running up to VB2014 (the 24th Virus Bulletin International Conference), we will look at some of the research that will be presented at the event. Today, we look at the paper 'Duping the machine - malware strategies, post sandbox detection', from Sophos researcher James Wyke.
As anyone familiar with malware research knows, a good way to study malware is to run a sample in a virtual machine or sandbox. But as anyone who has ever done this in practice will attest, very often the malware will detect it is running in a virtual environment and simply terminate execution.
In his paper, James looks at four malware families that take this one step further: they employ various kinds of decoy behaviour to frustrate and confuse both manual and automatic analysis.
The Andromeda downloader, for instance, when detecting a virtual environment, performs benign behaviour to conceal the malware's C&C addresses, while the Vundo (or Ponmocup) adware installer achieves this by using a decoy C&C address.
The Simda backdoor trojan, on the other hand, always sends data to the real C&C server, but when it detects it is running in a virtual environment, this data is used to add the IP address to a 'blacklist' of analysts' networks.
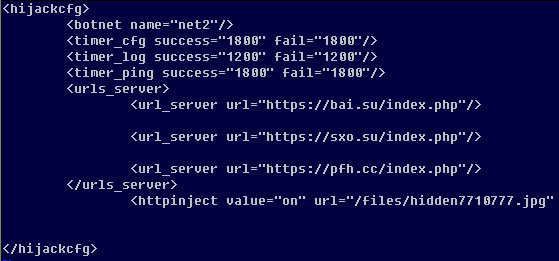
The Shylock banking trojan also connects to the real C&C server, but in case it is running in a virtual environment, fake configuration data is returned - the data looks genuine enough to pass casual inspection and thus could frustrate researchers.
Analysis of malware samples has moved beyond the realm of anti-virus companies and is performed every day by many researchers and security experts at a wide range of organisations. Understanding the decoy methods used by malware is very important to correctly identify malicious samples and the servers with which they communicate.
At the same time, running executables in a sandbox is an increasingly common method used to detect zero-day malware. As James's paper shows, simply trusting the output of such a solution may have undesirable consequences.
This won't be James's VB conference debut: last year he spoke about the ZeroAccess botnet and its C&C communications. We uploaded a video of his presentation to our YouTube channel:
You can now register for VB2014. And if you have some research that you want to share with the security community, why not submit an abstract to fill one of the seven remaining 'last-minute' presentation slots? (Deadline 28th August 2014.)
Posted on 22 August 2014 by Martijn Grooten