Posted by Virus Bulletin on Aug 13, 2014
Fabio Assolini to speak about malware targeting boletos.
In the weeks running up to VB2014, we will look at some of the research that will be presented at the conference. In the first of this series, we look at the paper 'P0wned by a barcode: stealing money from offline users', from Kaspersky researcher Fabio Assolini.
Cybercrime is a global phenomenon. In fact, it is its very global nature that makes it so hard to fight, as cybercriminals can easily hide behind proxies and legislations to stay out of the hands of law enforcement.
But this doesn't mean that cybercrime doesn't take local or regional forms. Those outside Brazil will probably not have heard of the 'Boleto bancáo' ('boleto' for short), a very popular payment method in the Latin American country. Unsurprisingly, online crooks have discovered this too.
Boletos can be paid at ATMs, as well as at banks and in many shops. Each boleto is uniquely identified by a barcode printed on it - it is this barcode that makes sure the funds go to the intended recipient. This way, bills and even online shopping can be paid for without the need of a credit card or even a bank account.
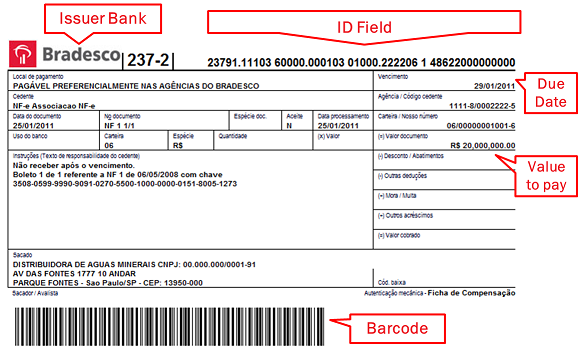
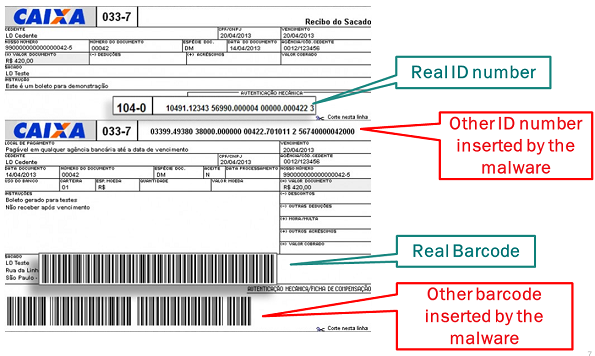
Of course, if you somehow ended up printing an incorrect barcode, the funds would go somewhere else - which is exactly what criminals have discovered. In his paper, Fabio looks at how malware is used to intercept and modify boletos as they are downloaded from the Internet. The barcode and its ID number are changed to point to an account owned or controlled by the criminals, and when the boleto is paid, the funds end up in their hands.
Other researchers have also recently looked at the underground economy's interest in boletos. Last month, security firm RSA claimed that through malware targeting boletos, crooks have netted the equivalent of billions of dollars in the past two years - though others have disputed that figure.
Malware targeting boletos continues to evolve. In a post on Kaspersky's Securelist blog, Fabio looks at the use of encrypted malware payloads XOR'ed with a 32-bit key and compressed using the ZLIB algorithm. This is a technique previously used by the GameOver Zeus botnet, and Fabio says he has evidence that Brazilian criminals are working together with European gangs.
To see a taster of Fabio's presentation and to get an idea of the Brazilian online underground, here is the video Fabio's VB2013 paper on malicious PAC files.
You can now register for VB2014. And if you have some research that you want to share with the security community, why not submit an abstract to fill one of the seven remaining 'last-minute' presentation slots?
Posted on 13 August 2014 by Martijn Grooten