Posted by Virus Bulletin on Oct 8, 2014
Malware switched to more effective Perl installer.
One of the most prominent discussion topics during VB2014 was the 'Shellshock' vulnerability (CVE-2014-6271) in the popular Bash shell for *nix, which was publicly disclosed while the conference was going on in Seattle.
Considered at least as serious as Heartbleed, Shellshock affects millions of servers. A successful exploit allows an attacker to execute arbitrary code by making use of the fact that many processes set environment variables in Bash and, under certain circumstances, Bash execute commands concatenated to the end of such variables.
Although exploiting the vulnerability isn't as straightforward as it is for Heartbleed, the potential attack surface is much larger and a lucky attacker might even be able to exploit the vulnerability on a server that is not exposed to the Internet. I wouldn't be surprised if, for some time to come, we learn of attacks using Shellshock for lateral movement or to escalate privileges in an advanced attack.
Cybercriminals are already exploiting Shellshock through the most obvious attack vector: vulnerable web servers. On its blog, ZScaler has an overview of various such attacks seen in the wild.
One attack that I found particularly interesting was the use of Shellshock by the 'Mayhem' malware to spread further - something which Malware Must Die! wrote about yesterday.
Earlier this year, we published a paper on Mayhem by three researchers from Yandex in Russia. Mayhem is a piece of malware that runs on *nix servers and is noteworthy because it can act under restricted privileges. It uses various plug-ins to look for and infect other servers.
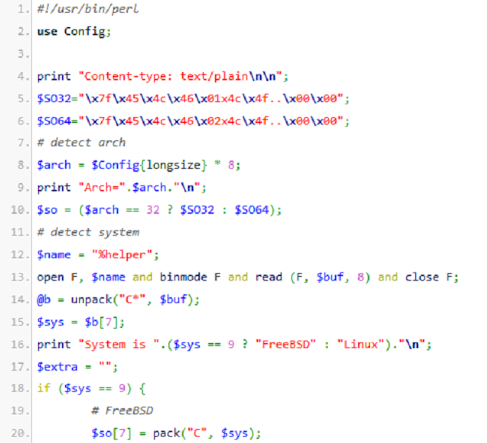
When Mayhem exploits Shellshock, it uses it to upload and run an installer written in Perl, thus replacing the original PHP-based installer.
I spoke to Evgeny Sidorov, one of the paper's authors, who said he wasn't surprised that Mayhem's owners are using Shellshock to infect more machines. The malware's flexible architecture made it easy for them to do so and using Shellshock is easier and more effective than brute-forcing WordPress credentials, which had hitherto been used. He also pointed out that using a Perl installer makes sense, given that Perl is installed on almost all *nix servers by default, while PHP is usually only an optional extra.
The good news if you're running Bash - and if you're running anything Linux- or Unix-based, you almost certainly are - is that patching is easy and that doing so is very unlikely to break other software. There is no excuse not to patch.
Posted on 08 October 2014 by Martijn Grooten