Posted by Virus Bulletin on Mar 4, 2015
Golden keys from the (first) crypto wars have come back to haunt us.
When a web client makes a secure connection to a web server (using HTTPS), it starts by sending a 'Hello' message in which it announces which cipher suites it supports. The web server then chooses one, presumably the one that offers the best security, and this will be used to encrypt the traffic.
A downgrade attack occurs when an attacker situated between client and server convinces them to use a weaker cipher suite. In itself this shouldn't be problem: even the weaker suites are supposed to provide ample security, but it can be used to facilitate the exploit of a vulnerability in a weaker cipher suite, similar to attacks that force the connection to use the older SSL 3.0 protocol to exploit POODLE.
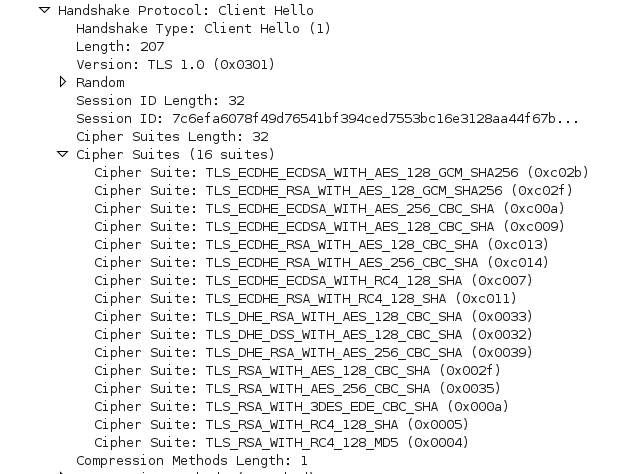
But researchers have discovered a new vulnerability, called FREAK, that shows it is sometimes possible to downgrade the cipher suite to one that is, in fact, weak by design.
Such suites, called 'export cipher suites', date back to the 'crypto wars' in the 1990s when the US government tried to prevent the export of strong encryption technology. Some ciphers, such as 512-bit RSA, were deemed strong enough for everyday use, yet allowed the US government to break them.
Researchers found that more than a third of the sites serving trusted certificates are vulnerable to such a downgrade attack. Moreover, many SSL clients will accept an export-grade suite, even if it isn't mentioned in the Hello message. An attacker with a man-of-the-middle position can thus change the Hello request to ask for 'export RSA'; the server will gladly use such a key and the client will not complain about the fact that it is using a suite that it never asked for.
To make matters worse — or orders of magnitude better, from an attacker's point of view — for performance reasons, web servers usually only generate a single export-grade RSA key and will continue to use this key until the next restart. Web servers are rarely restarted.
This means the attacker could crack the RSA key once and then read all traffic between the server and all clients whose traffic it can intercept and that are vulnerable to FREAK.
On his blog, Johns Hopkins crypto professor Matthew Green explains how it cost a group of researchers around $100 to crack an export-grade RSA key used by the NSA for its website. They were thus able to inject content into the site, even though it didn't give them access to the NSA's network itself.
$100 is very cheap for a crypto attack, though of course the attacker also needs to be able to get a man-in-the-middle position. This makes the attack not particularly suited for run-of-the-mill cybercriminals. However, for nation state sponsored attackers, interested in intelligence rather than quick financial gain, FREAK would be a very useful and cheap tool.
Thankfully, patches are being rolled out to clients and servers alike. A website has been set up to check if your client is vulnerable. It also contains a list of servers that are vulnerable and advice on how to patch.
What makes the vulnerability rather timely is that, much to the frustration of security experts and civil liberties activists, government officials in the US have been calling for 'golden keys', which would give law enforcement and intelligence agencies a backdoor into encrypted data and traffic. Now a previous generation of golden keys have come back to haunt us.
Virus Bulletin has updated the SSL configuration of its website and removed support for export-grade cipher suites.
Posted on 04 March 2015 by Martijn Grooten