Posted by Virus Bulletin on Aug 25, 2015
Several conference papers to deal with targeted attacks.
There was a time when analyses of malware and viruses at the Virus Bulletin conference used the number of infections as a measure of the harm done. And while there are still many talks on what is now referred to as 'opportunistic malware', targeted attacks, or APTs, have become a prominent feature of recent conference programmes. VB2015 is no exception.
Those who think that cyber-espionage attacks are the domain of the global superpowers should attend the talk by Check Point researchers Yaniv Balmas, Shahar Tal and Ron Davidson. They will present a paper analysing a custom-made trojan called 'Explosive', which was used by the Volatile Cedar campaign (which we blogged about in April). This campaign has been traced to an actor operating out of Lebanon.
Malware attribution is notoriously hard, but sometimes researchers get help from unexpected sources. Thanks to documents leaked by Edward Snowden, we know that Canadian intelligence is 'moderately certain' that the 'SNOWGLOBE' campaign was conducted by French intelligence. Cyphort researcher Marion Marschalek will present a paper in which she analyses four malware families linked to this campaign: NBOT, Bunny, Babar and Caspar, three of which share names with well-known French cartoon characters.
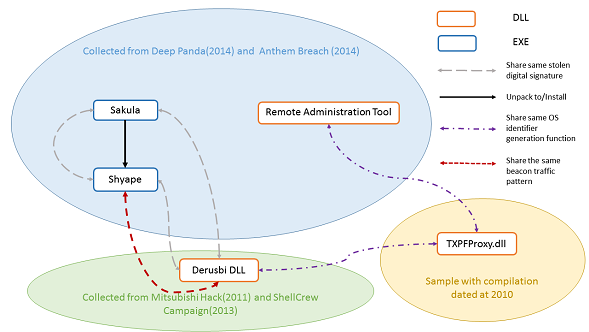
The 'Derusbi' malware family may not be too familiar a name, but it dates back to at least 2008 and has been used in a number of prominent attacks, from the breach at Mitsubishi Heavy Industries in 2011 to the high-profile Anthem breach from the beginning of this year. Fortinet researchers Micky Pun, Eric Leung and Neo Tan will present a paper in which they look at the malware, its evolution and its use in state-sponsored attacks.
The 'Skeleton Key' malware, which was discovered by Dell SecureWorks at the beginning of 2015, can rightly be called an advanced persistent threat. Targeting domain controllers, it can perform any number of actions and even after successful removal can still leave compromised authentication in place. A paper analysing this malware will be presented by Dell's Stewart McIntyre together with Microsoft researchers Chun Feng and Tal Be'ery.
Much as state-sponsored malware is the same, only (usually) slightly more advanced, dealing with such malware involves many aspects that traditionally haven't been part of a researcher's job description. Kaspersky Lab researcher Juan Andrés Guerrero-Saade will present a thought-provoking paper on what the shift from malware research to intelligence brokerage means for security researchers and their employers.
And of course, the rise of APTs has led to various companies and products that claim to provide protection against such attacks. Which then leads to the question: how can we test these products' efficacy? Three researchers from different backgrounds — Simon Edwards of Dennis Technology Labs, Richard Ford of the Florida Institute of Technology, and Gabor Szappanos of Sophos — present a paper in which they look at how to effectively test anti-APT technology.
Of course, several other VB2015 talks will deal either directly or indirectly with various aspects of targeted attacks. This includes the closing keynote from Kaspersky Lab researcher Costin Raiu, who has played a major role in the analysis of various APT attacks, from Stuxnet and Duqu to Regin and Equation.
And there are also the last-minute papers — the call for papers for which remains open for another nine days — these would be an excellent opportunity to present your APT-research to an international audience.
