Posted by Martijn Grooten on Mar 30, 2016
The rise of bug bounties in recent years has created an incentive for hackers to hunt for vulnerabilities in a lot of software and services. But what about those software projects that can't pay bounties, because they are developed by volunteers?
Thankfully, some researchers are devoting their time to such projects and to helping them find vulnerabilities before those with malign intents abuse them.

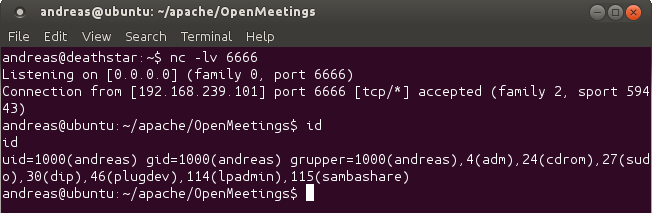
Today, we publish a paper (also available as PDF) by Andreas Lindh, a security researcher for Recurity Labs, who found a remote code execution vulnerability in Apache OpenMeetings, an open source software project for various kinds of collaborations.
Andreas disclosed the vulnerability responsibly to the OpenMeetings developers, who swiftly patched the flaw, before the research was published. Hopefully others will learn from the mistakes made.
This article was previously published on Andreas's blog, where he has also published other responsibly disclosed vulnerabilities in open source projects, including one in Apache Jetspeed earlier this month.