Posted by Martijn Grooten on Jun 12, 2017
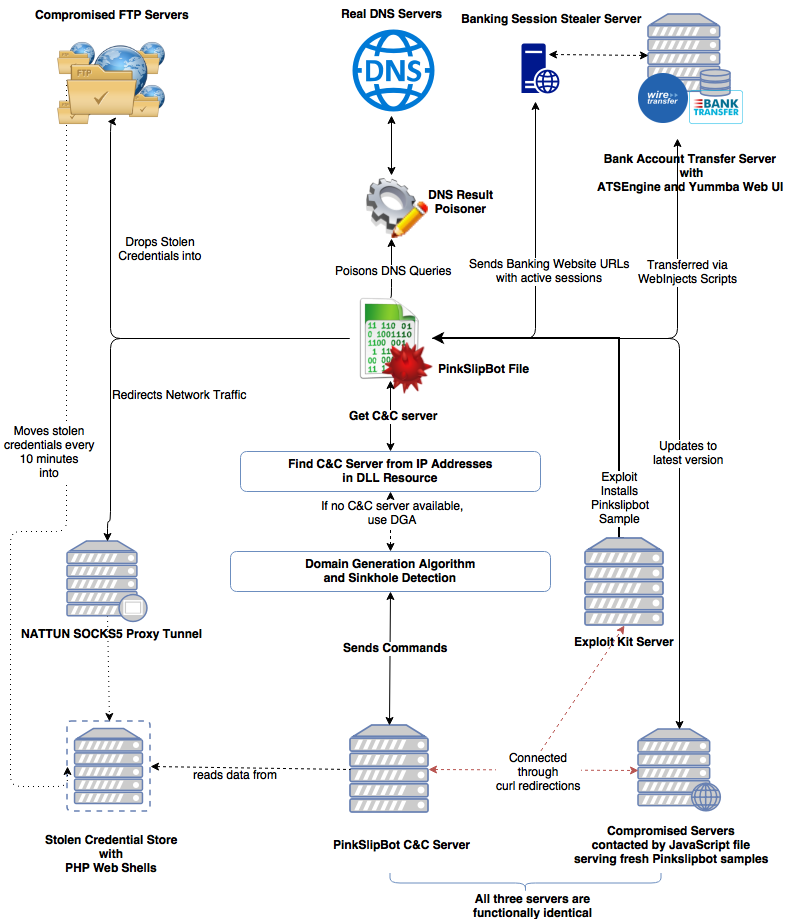
Pinkslipbot, also known as Qakbot or Qbot, is a banking trojan that makes the news every once in a while, yet never seems to get the attention of the world's Zbots and Dridexes. I looked at the malware myself three years ago, but since then it has been updated several times, the most recent update having been written about in an IBM blog post, which focused on the malware causing Active Directory lockouts in many organizations.
Pinkslipbot was also the subject of a VB2016 paper by McAfee (then Intel Security) researchers Sanchit Karve, Guilherme Venere and Mark Olea, who not only looked at the malware's then latest campaign, but also provided a detailed overview of its inner workings and its C&C infrastructure. The fact that it had infected around 100,000 devices (mostly within organizations in North America) underlines that it is important for the security industry not to overlook this malware.
Following the recent renewed interest in the malware, we have published Sanchit, Guilherme and Mark's full paper (HTML and PDF). Unfortunately, no video of their presentation is available.
At this year's VB conference (VB2017), several of the presentations on the programme deal with the issue of banking malware, including one on the prominent Dridex trojan and one that looks at how browsers are being abused by today's banking trojans.
VB2017 takes place 4-6 October in Madrid, Spain. Registration is now open - register before 30 June for a 10% Early Bird discount!