Posted by Martijn Grooten on Nov 16, 2017
FireEye is well known within the security community, both for its advanced protection products and for its regular research reports. Recently, the company launched a new version of its Endpoint Security product and, to demonstrate its commitment to being tested publicly, asked Virus Bulletin to run a short test on it.
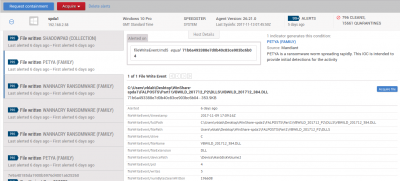
A public web server is used to download an installer for the product, which makes the process of installing an agent on a new endpoint rather smooth. The same web server also serves as the central management system and can be used both to amend various settings as well as to analyse blocked threats. Given how many enterprises have internal CERTs that analyse new threats, the ability to view information on blocked malware, and safely download the file if needed, is an important feature. As no security product is perfect, the management interface also allows for a file to be released from quarantine, should it have been blocked erroneously.
 |
 |
To measure the product's performance, we had two versions of the product scan the most recent version of the well-vetted WildList and were pleased to note that it did not miss a single sample. We also tasked the product with scanning a large set of widely used legitimate software, and found that it did not erroneously block any of the files contained therein.
In addition, we had the product scan a more diverse and less well-vetted set of malicious files. Of these, the product blocked 92.1% of the older files (which were 6-10 days old when the test was run), and 83.4% of the newer files (1-5 days old). Though the malware landscape (and thus product performance) is notoriously volatile, these percentages are on a par with those we see when testing other endpoint solutions.
Finally, we ran a proactive test where the product was disconnected from the Internet for ten days, after which, with the Internet connection still disabled, it was asked to scan files seen in the intervening period. While not a very common scenario, this allowed us to measure the product's proactive detection, as well as its performance in more esoteric environments where regular updates may not be possible. Here, the product detected 75.1% of the malware seen 1-5 days after disconnection, and 60.1% of the malware seen 6-10 days after disconnection. These figures are, again, on a par with those seen in other products.
Based on these tests, we are confident that FireEye Endpoint more than satisfies the minimum requirements for an endpoint security product.
The test we ran took place in the first week of November 2017 and followed the same methodology as our regular VB100 tests, but was shorter in length. For that reason, no VB100 certification rights are possible, based on this test. We tested the product on both Windows 7 and Windows 10; the reported percentages combine the scores for both platforms. The product also offers agents for both Linux and Mac OS X, which weren't tested. The latest version of the agent (26.21.0) was used in all tests, apart from the proactive test where time constraints forced us to use an older version (26.18.0); we believe the detection of both versions should be similar.
This test was paid for by FireEye and conducted by Virus Bulletin. FireEye was not given editorial rights over the content of this blog post.