Posted by Martijn Grooten on May 10, 2017
In his VB2014 paper, Bromium researcher Vadim Kotov sketched the possibilities for malicious actors to use web ads to spread exploit kits. Unsurprisingly, malicious actors also spotted those possibilities, and the advertisement ecosystem has become such a big attack surface that many security experts advise the running of ad-blockers to enhance security.
Today, we publish a paper (HTML and PDF) presented at VB2016 in Denver by Malwarebytes researchers Jérôme Segura and Chris Boyd, in which they look at this ecosystem, how it is used, and at what techniques are being utilised to spread malware. (Unfortunately, due to a technical error we are unable to publish the video of their presentation.)
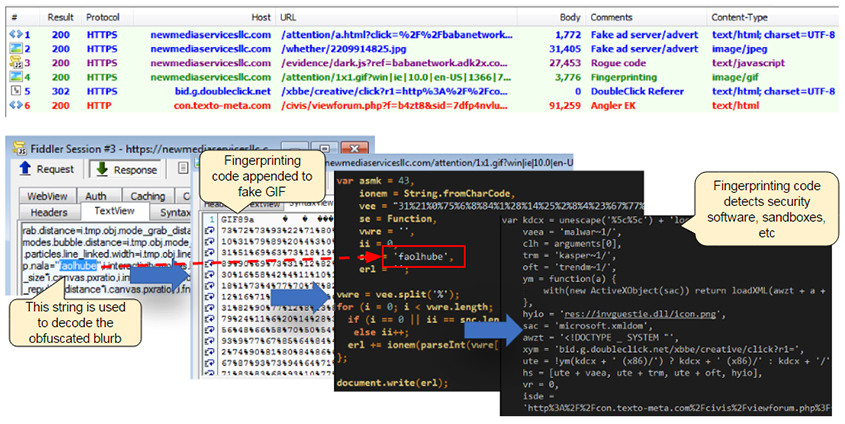
Those who want to keep up with trends in exploit kits in general, and malvertising in particular, are advised to read Jérôme's posts on the Malwarebytes blog, while those who are interested in the subject of 'advergaming', mentioned in the paper as a possible future trend, should come to VB2017 to see Chris present a paper on this very subject.
Registration for VB2017 is now open - register before 30 June 2017 to qualify for the early bird rate!