Posted by Martijn Grooten on Oct 31, 2018
Researchers at Kryptos Logic have discovered that the Emotet banking trojan is exfiltrating entire email bodies as opposed to merely email addresses.
Emotet was first discovered in 2014 as a banking trojan but has since evolved to become mostly a distributor of other malware. A typical Emotet infection starts with an email attachment, which downloads Emotet, which then downloads the final payload.
However, Emotet itself also has the capacity to steal data from the infected devices, among them email addresses in the contact list. In this, the malware is hardly unique: such harvested lists are then re-used or sold on for the purpose of sending spam that appears to come from a known address, and thus may seem more credible.
Now, however, the malware has added a module that steals the email body, subject and various metadata of all emails sent or received in the past 180 days, by using the Outlook Messaging API (MAPI). The data is then base64-encoded, stored in a temporary file and eventually uploaded to the malware's command-and-control server.
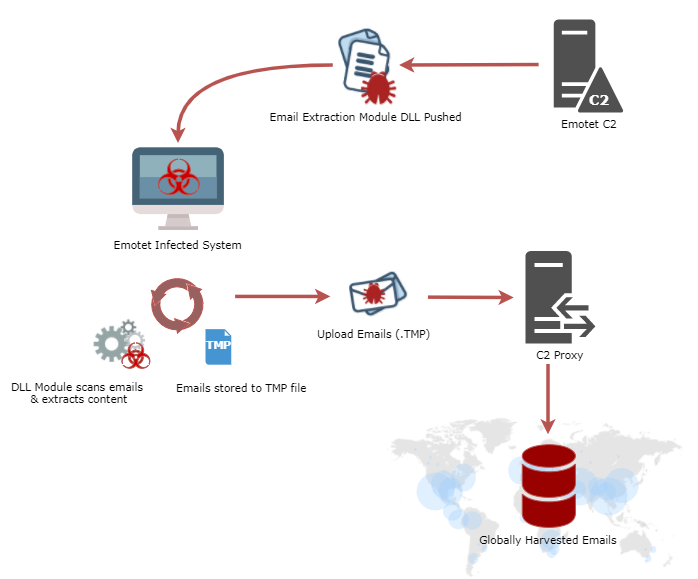 Workflow showing how Emotet actors harvest emails (source: Kryptos Logic).
Workflow showing how Emotet actors harvest emails (source: Kryptos Logic).
Using previously sent/received emails as a template for spam emails could result in spam messages that appear more credible, where the same email is resent with a link or attachment replaced. Though this won't change the fact that bypassing spam filters at scale is hard and the gains in delivery rates would likely be minimal, if emails do get delivered, it would make them appear very legitimate. I certainly wouldn't always notice that an email had been sent before.
More worryingly, the stolen emails could also be used in more targeted attacks, to perform some very credible social engineering. Though Emotet itself isn't a particular targeted threat, it has been known to download more targeted malware in the final stage, as a North Carolina water and sewage authority learned the hard way recently. It is not hard to imagine how the stolen data could be mined for more interesting and valuable targets.
And those targets will probably be easy to find: Emotet regularly infects US- and UK-based government organisations and enterprises.