Posted by Martijn Grooten on Dec 6, 2018
Until recently IoT botnets mostly consisted of Mirai and its many descendants. However, during 2018 we have seen an increase in the variety of botnets living on the Internet of Things.
One prime example is Hide'N'Seek, discovered by Bitdefender in January, which is notable for its use of peer-to-peer for command-and-control communication.
Though the botnet's purpose remains a bit of a mystery, it continues to update itself. This week, Avast published a blog post sharing details of how the botnet continues to infect new devices, and also published information on a tracker the company has built to measure the size and global distribution of the botnet.
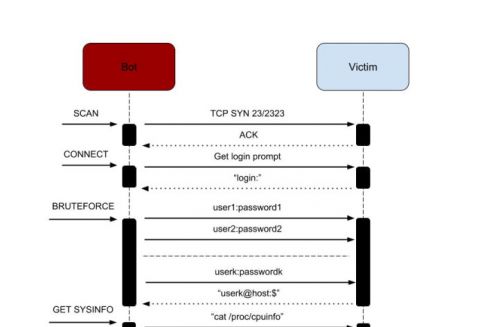
Hide'N'Seek infection.
Today, we publish the VB2018 paper on Hide'N'Seek by Bitdefender researchers Adrian Șendroiu and Vladimir Diaconescu, who discovered the botnet. You can read the paper in both HTML and PDF format. We have also uploaded the video of their presentation to our YouTube channel.