Posted by on Aug 25, 2020
While many kinds of economic activity have decreased during the pandemic, that is not the case for online threats: they have been as prolific as ever and continue to evolve. Following a long tradition, we reserved some spots on the Virus Bulletin Conference programme for some hot last-minute research.
This year, of course, the VB Conference will be held virtually. VB2020 localhost will have a live part, which takes place in a single track on each of the three conference days (30 September to 2 October), and an on-demand programme of talks that will become available as soon as the conference opens.
And perhaps most importantly, the conference will be completely FREE to attend (register now if you haven't done so already!).
We are excited to announce the addition of nine last-minute talks to the live programme.
Targeted ransomware attacks continue to be a plague and are probably the threat that organizations are most concerned about today. Sophos researcher and regular VB Conference speaker Gabor Szappanos will discuss toolsets used by ransomware crews, in particular during the initial infection phase.
Malware on macOS isn’t particularly new anymore, as VB regulars will know from previous conference talks by Jamf’s Patrick Wardle. This year, Patrick will be back to talk about EvilQuest, a rather insidious piece of macOS malware that has some viral capabilities, showing that even pedants aren’t correct when they claim that 'Macs don’t get viruses'.
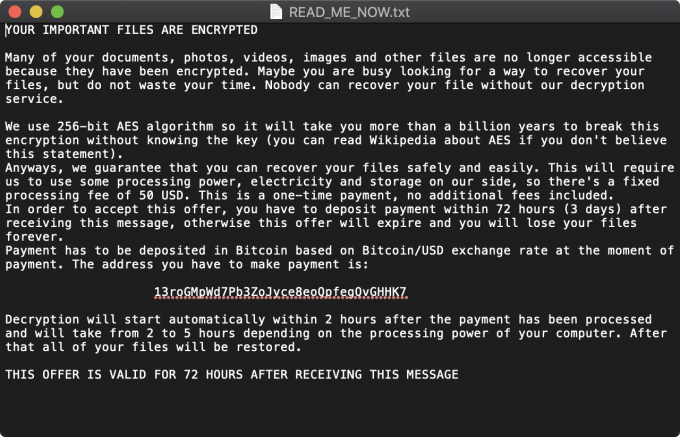 Once all the files in the list of target files have been encrypted, the EvilQuest malware writes a file named READ_ME_NOW.txt. Source: objective-see.com.
Once all the files in the list of target files have been encrypted, the EvilQuest malware writes a file named READ_ME_NOW.txt. Source: objective-see.com.
Another regular feature at recent VB conferences is malware linked to North Korea. Sveva Vittoria Scenarelli from PwC will offer a comprehensive overview of the TTPs and strategic goals of the Black Banshee threat actor, also known as Kimsuky. Threats linked to North Korea’s northern neighbour aren’t new to the VB Conference either. At VB2020 localhost, Malwarebytes researchers Hossein Jazi and Jérôme Segura will discuss the ‘Evasive Panda’ APT group that was recently found targeting Hong Kong and India.
Attribution, however, remains a contentious subject. Cisco Talos researchers Paul Rascagnères and Vitor Ventura will discuss the attribution process when it comes to cyber threats and will in particular look at the recent linking of APT29 with WellMess by a number of Western intelligence agencies.
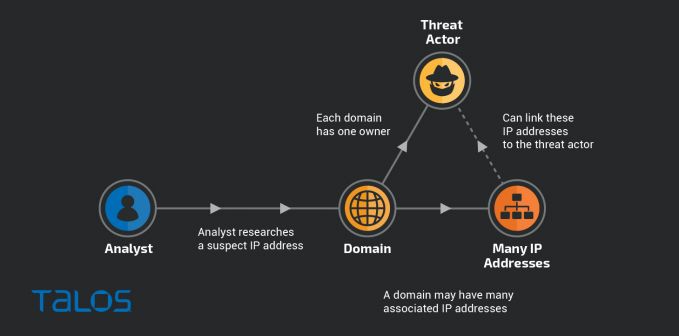 A common technique for linking separate campaigns is by pivoting on common infrastructure. This technique can be used to investigate malicious IP addresses and domains. Source: Talos.
A common technique for linking separate campaigns is by pivoting on common infrastructure. This technique can be used to investigate malicious IP addresses and domains. Source: Talos.
ESET’s Zuzana Hromcová, who also spoke at VB2019 in London, will be preset at this year’s virtual event to dive deeply into the InvisiMole threat actor, which is noteworthy due to its use of external vulnerable tools to exploit and then to deliver malware onto targets’ systems.
Tan Kean Siong of The Honeynet Project will speak about how he selectively spread supposedly $100,000 worth of Bitcoin wallets on the Internet and what that taught him about the ‘thieves’. Meanwhile, McAfee’s Christiaan Beek will dive deep into the OOXML standard and explain how its details matter to malicious actors and thus to threat analysts.
Finally, VB wouldn’t be VB without some talk on security products: Zoltan Balazs (CUJO AI) and Hyrum Anderson (Microsoft) will present details of the competition they ran in which participants were tasked to bypass machine learning-based malware detection.
But that’s not all! We have also added more than a dozen new talks to the on-demand programme.
Among them is is Hiroshi Takeuchi of Macnica Networks, who will speak about the LODEINFO RAT and its use in APT attacks in Asia. Tejas Girme of Qualys will discuss the strategies employed by adversaries to establish and strengthen their foothold inside Docker containers.
Alexander Adamov of NioGuard Security Lab will talk about the WastedLocker ransomware, while another popular ransomware, Netwalker, will be the subject of a presentation by McAfee’s Thibault Seret. ESET researcher Ignacio Sanmillan will present his research on Ramsay, a cyber-espionage toolkit tailored for air-gapped networks.
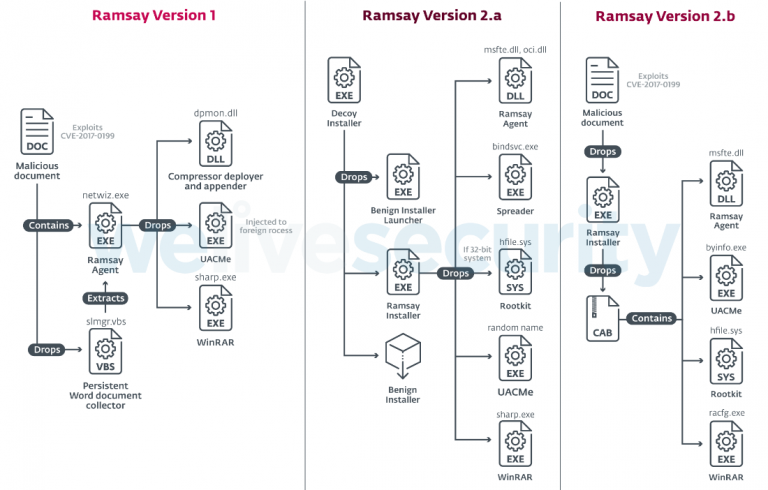 Overview of discovered Ramsay versions. Source: WeLiveSecurity.
Overview of discovered Ramsay versions. Source: WeLiveSecurity.
There are many more talks on the programme, including those added during the first CFP phase back in spring, as well as eight presentations that form part of the Threat Intelligence Practitioners' Summit (TIPS). For details of all the presentations the event has to offer, check out the full programme!
And alongside the presentations VB localhost will be running a dedicated Discord server, through which you can chat with other participants, contact event partners and speakers and even set up 1:1 or small group meetings via text, audio or video.
Don’t forget registration for VB2020 localhost is completely free, and we won’t even pass on your details to our sponsors. We look forward to seeing you there!