2006-09-01
Abstract
John Hawes takes an indepth look at Kaspersky's current home-user offering.
Copyright © 2006 Virus Bulletin
Kaspersky's current home-user offering goes under the functional title of Kaspersky Internet Security 6, hereinafter referred to as KIS6. Aiming for the all-in-one, covering-all-the-bases, eggs-in-one-basket end of the market, KIS6 is a fairly complete package, combining standard on-demand and on-access virus checking with web and email filtering, a firewall, anti-spyware and anti-spam functionality, intrusion protection, and more besides.
Since I began playing with KIS6 for the purposes of this review, the product has been repackaged and given away, with some limitations on functionality, by the web giant AOL. What the future of this channel will be is unsure, but it seems likely to bring Kaspersky's brand increasingly to the fore in the home market. To see how the product fared in the world of the everyday user, I put on my ordinary Joe hat, tried not to think too hard, and charged straight in.
The user guide supplied with the product is also available as a PDF download, but is not included in electronic form on the rather empty distribution CD. It opens with a fairly lengthy introduction on the general subject of computer security, malware and best practice, followed by clear and thorough instructions for the setup and use of the product. My only quibble with this in-depth document is that, at some point, the section referred to in the guide as 'Program Tools' has been renamed 'Service' in the product itself – which caused some confusion until I figured out what had happened. This sort of change cropped up in a few other places too, and was particularly noticeable in the online help, when a link marked with one title would lead to a page with a different one (e.g. 'General' linked to 'Settings').
Kaspersky's web presence is based at www.kaspersky.com. The home page displays the green packaging of KIS6 and the slogan 'Red for threats Green for you'. The rest of the page is fairly clean and simple, with the exception of the rapidly animated online scanner area in one corner (this offering is given prominence on most pages). A knowledgebase of support information is easily found, with a section dedicated to KIS6 where many likely product-related queries are answered plainly. Among the information provided are details as to why the full product is superior to the pared-down version offered free by AOL (web-scanning, heuristics, intrusion defence and restore tools are all mentioned, along with the many fine-tuning options, as being good reasons to opt for the full, paid-up version).
More malware-specific issues are dealt with at www.viruslist.com, which claims to be 'the largest encyclopedia of malware'. It certainly has a wealth of entries, most of which have at the very least a list of the aliases applied by different vendors, but many have little further information available, and as a malware information resource it lags behind a few other vendor sites.
Once information from the online databases has been exhausted, troubled users are pointed to the company's 24/7/365 tech support service, which is available in four languages and included in the annual licence fee. I dropped a few email queries to my local offices, and generally got a friendly and reasonably helpful response within about 10 minutes.
I ran the installer from the CD – although it is also available as a download in English, French, German, Dutch and, of course, Russian; the download size is about 13MB.
The EULA, at a quick glance, contained nothing too frightening, and after selection of the root folder I was offered a choice of installation types. 'Complete' (for 'integrated protection of your computer') installs all available software, while at the other end of the spectrum, 'Anti-virus features' covers virus protection only, leaving out all the other bells and whistles. In between is a 'Custom' option, which is recommended for advanced users.
Having virtually no previous experience of Kaspersky products, I jumped straight into the custom mode, and found myself faced with a tree under the title 'KIS6'. Beneath the lonely 'Virus Scan' branch was a second, entitled 'Protection Components' and marked with a promising '+'. Although not a great fan of the particular flavour of Windows-installer menu system used, I quickly figured out that the virus scanner itself is compulsory, while just about any combination of the other components is possible. (Checking back, I found that the 'Anti-virus features' option covered the scanner as well as on-access virus blocking, including web and mail filtering.) I left everything selected, and looked forward to being protected from viruses in files, on the web and via email, along with 'Proactive Defense', 'Anti-Spam', 'Anti-Spy' and 'Anti-Hacker' modules to play with.
After a very zippy first install came a series of set-up choices, all of which were highly configurable. The licence can be applied using the non-standard approach of pointing it to a file on a local disk, which was useful in my test lab due to the lack of Internet access. The default, however, is to enter an activation code found on the CD sleeve, following which a key is drawn from the ether. When I later tried this method on a machine connected to the web, it had some trouble connecting to the site from which it needed to download the file.
The update settings range from fully manual to fully automatic, with a fine-tuneable time period selection in between, and also allow for updates from a wide range of non-standard sources. On the lab machines, ignoring the update prompt left a sombre red warning lurking around most GUI pages, to make sure I didn’t forget that my signatures were out of date. When I installed to a web-connected machine, downloading the several months' worth of updates released since the product came out took around half an hour, following which a reboot was required.
On the next page, scans can be set up of 'Startup objects', 'Critical Areas' and the full machine. These can be adjusted in terms of time but not content. Next up is the option to password-protect your settings, again with the option to protect only certain actions. I went first for the full-on coverage to see how much it would hamper my tinkering, but used a rather skimpy password, which was not remarked upon. There followed a moment of file copying before we got into some more technical setup options for the 'Anti-Hacker' module (a combination of firewall and intrusion detection). Networks are divided into zones and given security ratings; the Windows Firewall is detected if present, and there is a choice of shutting it down and replacing it with Kaspersky's firewall, or leaving it on and installing the new one in an inactive state.
Next, some network applications are grouped together and have rules applied to them. These rules are configurable, and it is recommended to disable DNS caching. 'Interactive protection' offers to provide a warning when dangerous or suspicious things happen – dangerous only for the novice, while the more experienced user is offered the tweakable 'suspicious' option featuring a 'training mode'. With the full set of options selected, a reboot is required, and we're done.
At every point during the installation things were reasonably clear and well laid out, with sensible default settings explained in a way which might occasionally daunt the average untrained home user a little, but which would be unlikely to be truly terrifying. For the more adventurous, a button marked ‘Options’ or ‘Advanced’ is never far away, leading to a playground of fine-tuning tools. So far, the only choice I felt was missing was the ability to customize the selection of items scanned on start-up. The process was also fairly slick and speedy – I suspect that, had I selected all the defaults on a machine with a good reboot time, the whole thing could probably have been zipped through in under a minute.
On initial boot, after some popups informed me that the product might be out of date, and that a full scan of my machine had yet to be carried out, I was asked for my password before I could activate the product properly, and was offered the option to save the password for the current session.
A red-and-black 'K' sat in my system tray. Right-clicking it gave me options to scan my computer or run a scan (which opens the KIS6 GUI at the scan page), update, check a network monitor (which shows me tables of connections, open ports and traffic), or view the settings (which opens the clear and admirably thorough configuration page). There was also the bold 'Open KIS6' (the default for the button, leading obviously to the main product interface), 'Pause protection' (which stops on-access scanning, giving a choice of time periods before reactivating, ranging from one minute to never), and finally 'Exit', which shuts the whole thing down quickly and efficiently, accompanied by appropriately worried popups from the Security Centre.
The main GUI itself is simple and clear, with menus and warning boxes down the left and a summary screen on the right, adorned with simple cartoon-style logos: a green umbrella for 'Protection', a magnifying glass for 'Scanning' and a globe for 'Services'. Reassuring green check marks informed me that protection services were running and that no threats had been detected, while a more sombre red '!' warned me again that I really should update my signatures.
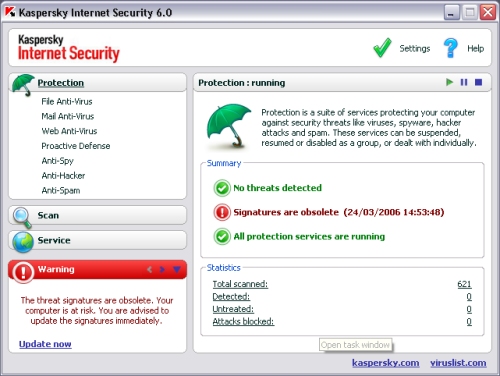
Each pane, representing a different facet of the product, provides a nice clear overview of the protection provided, with status and statistical information and remarkably fast-acting stop/go/pause buttons. The large 'Settings' button in the top corner of the screen brings up the configuration page for each module, with some simple controls and numerous 'Settings' and 'Customize' buttons to allow for tweaking. The clarity was as welcome as the depth of configurability.
A few brief scans over the VB test sets were easily configured, and trundled along at a fair speed with little difficulty. I found the unearthly scream that accompanied a virus detection a little disturbing, especially as I had set the warning level to 'Alert me at the end of the scan' and was expecting it to run silently. Without intervention, the yelps came along approximately every 15 seconds during a scan of the full infected collection – about one for every 100 viruses found. This was one of the only pieces of functionality that I couldn't figure out how to switch off, and I was forced to leave the room for a while to get away from the noise. On my return, having resolved to dig deeper, I did manage to find out how to deactivate the sounds, thanks to a help page which featured some misleading terminology (telling me to visit the non-existent 'Tools' page) but also a useful link to the right place, where I found copious options to configure the squealing, along with email alerts, popup balloons and so on.
At one point I managed to upset the scanner by foolishly clicking the 'neutralize all' button halfway through the scan. This left me staring at an hourglass for over a minute while the product got round to changing its balloon from a warning box to one with options to disinfect or delete (or skip, along with an 'apply to all' box which, thankfully, allowed me to carry on with the scan). Stopping and restarting the scan invariably offered the chance to pick up where it left off or rerun from the beginning, which I found useful. The timer seemed a little temperamental, claiming already to have been running for 40 minutes only 10 minutes in – this soon righted itself however, once the 'Finish time' prediction that runs in conjunction with the (fairly accurate) progress bar had settled down to a stable estimate.
When running a scan of an entire (clean) machine, the product was nice enough not to slow down anything else going on – in fact, it slowed itself almost to a halt when anything else was running on the machine, and only really got going when it was allowed free rein of the available resources. Even in full-paranoia mode there was little effect on other operations, although the scan did take many hours on a slower, more well-used machine.
The product sailed through the VB collection, happily picking up all the WildList set and missing nothing in the zoo either, only seemingly to get snagged for a time on the very last file, overrunning its predicted finish time by several minutes. I soon realised this was a recurrence of the above problem, apparently going back over the vast swathe of infection reports to find the first one before presenting it to me. The 'Prompt for action when scan is complete' option produces a dialog box at the end of the scan (or, in the case of a scan of a large area with many thousands of infected files, a minute or two later), and the timer for the scan continues, rather oddly, until an action is selected.
On-access scanning over the collection ran at first at a fair speed too, although trying to do anything else while this went on was painfully slow, as is perhaps to be expected with so many infections being found at once. Once it got above 5,000 infected files accessed by the same process though, things slowed to a snail's pace, and a job some scanners have managed comfortably in half an hour ran to well over six.
Opening huge numbers of uninfected files in a similar manner presented no such problem though, so presumably on an average home user's computer – which, one hopes, would rarely have more than a handful of infected files on it at any given time – this would not present a major problem; it's also possible that some kind of tweak to the near-infinite configuration settings would speed things up. Looking at it more closely, it seemed likely that the problem was something to do with alerts and counts of viruses – as the script ploughed through the infected files, the GUI trying to display stats of viruses found and blocked lagged far behind, hitting the 100 mark at about the time when 5,000 had, in fact, been stopped.
My only other issue with the on-access protection feature is the apparent absence of an exclusions list, although admittedly such a function is likely to be more useful to virus researchers and testers than to the average home user.
Using machines connected to the web, or to spoofs of it, I was able to play with some of the other functions. The 'anti-hacker' segment seemed fairly happy in its training mode – it would occasionally let out its wild yelp and suggest I should be worried about programs using 'invader' techniques, or query whether I really wanted to let my browser connect to the web, but once it had learnt a few of the basics it seemed content that I wasn't doing anything crazy.
A spell of web browsing seemed to suffer no significant slow down, and every ten minutes or so I was informed of a blocked attack from some network worm or other, which made me feel very safe. When I started trying to download suspicious files the scream would be there to warn me, and nothing unpleasant slipped by its guard when I tried downloading the entire WildList from the lab webserver. Sadly, the anti-spam functionality fell outside the scope of this test, but the whitelist 'training' area requires an Outlook inbox containing a minimum of 50 legitimate emails, to acclimatize to your mail habits; mail anti-virus is independent of the mail program.
The anti-spy area includes phishing, dialler and popup protection, along with an anti-banner tool (not activated by default). Again, most of these have configurable whitelists and blacklists. 'Proactive defence' covers behaviour analysis, preventing suspicious actions such as injecting into other processes, along with monitors watching for changes to the registry and unwanted Office macro behaviour.
All of these tools have a nice sliding scale on their settings pages, running from switched off to total lock-down, with the recommended level somewhere in between, and with deeper and more complex settings available for the more advanced user, producing a reassuring sense of consistency.
On top of all this, there is also a command-line interface, allowing the serious techie to get his fingers dirty, and perhaps even integrate the software's varied functionality into other tools, and a boot-disk creation utility, which uses the BartPE utility (not supplied) and a Windows XP install CD to create a bootable live CD with Windows and KIS6 all ready to be run, providing a fully secure safe mode.
With little to criticize and much to praise, this is a solid, well-designed product, neatly and seamlessly integrating a wide range of protection into a single, easy-to-use interface. Though perhaps not the fastest in terms of scanning times, especially during heavy on-access testing, this is perhaps the price one must pay for the thoroughness shown. The combination of easy-on-the-brain controls for the general user to ever more fine-tunable configuration settings for the expert is welcome and well thought out, and the visual design is a similarly happy blend of friendly, cartoon-like graphics with serious-looking controls.
Kaspersky has aimed to cover as many security aspects as it can in a single streamlined application, and to allow the user to apply them in as flexible a way as possible. In terms of clarity of design and simplicity of implementation, Kaspersky has created an extremely strong user interface, backed up by solid and thorough detection technology.
Technical details. The product was installed at various times on: AMD K6, 256MB RAM, dual 10GB hard drives, no network, running Windows 2000 Professional SP4. Intel Pentium 4, 512MB RAM, dual 20GB hard drives, 10/100 LAN connection, running Windows 2000 Professional SP4 and Windows XP Professional SP2. Intel Celeron notebook, 256MB RAM, 10 GB hard drive, 2Mbit ADSL modem, running Windows XP Professional SP2.