Posted by Virus Bulletin on Jul 7, 2014
Gabor Szappanos looks at the resurgence of malicious VBA macros that use social engineering to activate.
Macro malware had long been assumed dead. After all, macros are disabled by default in modern versions of Microsoft Office, which means they do not automatically execute upon opening a file.
However, macro malware has recently made a comeback. Earlier this year, we wrote about a report from the National Cyber Security Center in the Netherlands, on the resurgence of macro malware in targeted attacks. In April, Gabor Szappanos, a researcher from Sophos in Hungary, published a paper on the use of macros as an infection vector in the Napolar campaign.
Today, we publish a new paper by Gabor, in which he takes another look at recent macro malware. He shows how malware authors have discovered that, in many cases, fancy exploitation isn't needed: some simple social engineering suffices to make recipients enable the macros, upon which the actual payload is downloaded onto the victim's system.
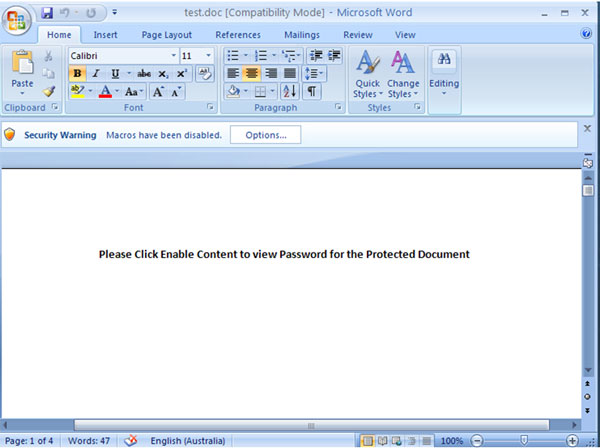
Remember that as of this month, all papers published through Virus Bulletin are available free of charge. You can download this paper here in HTML format, or here as a PDF (no registration required).
Posted on 07 July 2014 by Martijn Grooten