Posted by Virus Bulletin on Jun 26, 2015
Paul Royal looks at malware served through the most popular websites.
Though VB2014 took place nine months ago, most of the papers presented during the conference remain very relevant. Paul Royal's paper 'Quantifying maliciousness in Alexa top-ranked domains' is no exception.
Large websites serving malware through direct compromises or through compromises of the ad networks they use (that being the subject of another VB2014 presentation) continue to make the news. Moreover, those serving the malware, typically through exploit kits, work hard to make sure that it isn't picked up by automated scans. For that reason alone, Paul's presentation is worth watching.
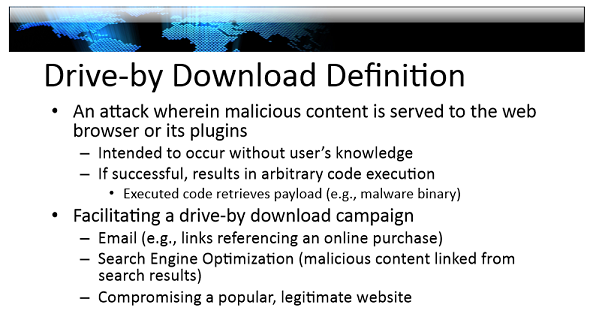
We have uploaded Paul's presentation to our YouTube channel. We also published the paper he wrote, which you can read here in HTML format or download here as a PDF.
If you like presentations like Paul's, why not register for VB2015? A 10% Early Bird discount applies until 30 June.