Posted by Virus Bulletin on Nov 2, 2015
Great research presented in a stimulating environment.
I had heard many good stories about previous Hack.lu conferences, so I was excited this year to finally be able to make it to Luxembourg itself, where the conference took place in a hotel just outside the country's eponymous capital.
With more than 400 people in attendance, the conference has become one of Europe's bigger security events, but it still managed to feel informal, friendly and welcoming. Wearing my VB Editor's hat, it was also nice to see a number of Virus Bulletin authors and speakers presenting their research at the conference.

Hack.lu is primarily a single-stream event, but there were a number of workshops taking place in parallel with the main stream. I only attended one of these, by Didier Stevens, in which he explained how to use his popular oledump.py tool for analysing potentially malicious Office documents.
Unsurprisingly, there were several talks on Internet-connected devices, including one by Axelle Apvrille, who talked about her research into Fitbit trackers. Although her proof-of-concept of using a tracker to crash a computer it was connecting to received quite a bit of media attention, I was more intrigued by the idea of using such a device to automatically lock a computer when you walk away from it.
The two keynotes also looked at the subject of IoT. In the first of them, Paul Rascagnères looked at the possibilities of hacking (often Internet-connected) devices, a session which included the presentation of the world's first Internet-connected underwear and, much to the audience's bemusement, looked at the possibilities of hacking certain adult toys.
The second keynote, by Marie Moe on medical device security, was more serious. This is a popular topic, yet also one that can easily turn into rather unrealistic horror scenarios. For Marie, however, the subject is very important: she herself wears a pacemaker. "The Internet of Medical Things is real", she said, "and my heart is wired into it." Marie explicitly urged hackers to look for vulnerabilities in medical devices, thus helping to make them more secure.

Marie Moe on stage. Photo: Claus Cramon Houmann.
Another interesting presentation was given by Saumil Shah, who promised to show us a way to serve a browser exploit with just one image. This sounded far-fetched, but actually wasn't: textbook steganography was used to hide well-known exploit code inside an image file, which was then modified so that its visible content didn't change, yet at the same time it became an accepted HTML file (which, through JavaScript, triggered the exploit) that was accepted by all major browsers.
Saumil's goal, of course, wasn't to tell us how to serve browser exploits more effectively, but rather to warn about the dangers of the second part of Postel's law: being liberal about what 'errors' you accept in content provided by others, while sounding nice in theory, can have pretty serious consequences.
Later, Ange Albertini re-emphasized the same point. Ange gave an interesting talk on his favourite subject, that of 'polyglots': files that can be opened as more than one file type, like Saumil's example of an image that is also an HTML file or, as Ange and Axelle Apvrille had shown at Black Hat Europe last year, an image that is also an Android package file. While a nice ingredient for CTFs and other kinds of puzzles, polyglots could also be used to bypass security measures.
The subject was also touched upon briefly in a more theoretical presentation by Jacob Torrey on Crema, a programming language inspired by the LangSec principles, the idea behind which is that programmers are going to make mistakes, so the language should reduce their chances of doing so and also reduce the damage caused by mistakes once they are made — and that includes file parsers being more strict about how they treat external input.
Several talks, rather than look forward to possible future attacks and solutions, looked back at what has already happened. Marion Marschalek, Paul Rascagnères and Joan Calvet spoke about the 'cartoon' malware family, which has been linked to French intelligence. Marion had presented some of this at VB2015, but as it is a fascinating subject, I didn't mind seeing it again.
Dhia Mahjoub spoke about using DNS 'big data' to track exploit kits and the companies hosting them. This was essentially an updated version of the paper he presented at VB2014 last year and it was nice to see these methods continue to work.
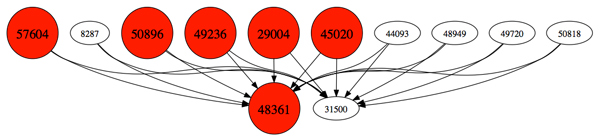
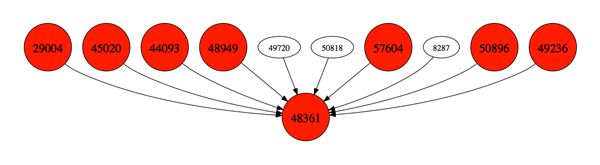
Malicious ASN leaf nodes made an appearance in Dhia Mahjoub's talk.
As the conference programme was rather full, there were a number of interesting-looking talks I sadly missed, including talks on the Android exploits used by Hacking Team, on automatic unpacking, and one on using a KVM device to bridge an air gap.
Two of the talks I made sure I didn't miss were on a subject close to my heart: the encryption (or lack thereof) of messaging protocols.
Frederic Jacobs presented an overview of the work that is being done on encrypting email and chat protocols and the many issues involved, including the lack of forward secrecy (which has been an important requirement, especially following Snowden's revelations), the fact that many messaging protocols need to work asynchronously and, perhaps most importantly of all, that encrypted messaging protocols tend to be difficult to use.
The latter shouldn't be an issue when it comes to the use of STARTTLS in email, where it is often used to encrypt the message as it travels over the public Internet, which should happen transparently to the user. However, in his talk Aaron Zauner presented the result of an Internet-wide scan of mail servers which found that many don't support encryption at all, while those that do often implement it poorly. The take-away message here was one that I have made in the past: if you send an email, unless you explicitly add encryption yourself, you should assume it is sent unencrypted over the Internet.
There was, however, a small silver lining to this talk. Aaron and his colleagues received a number of complaints following their scanning. This shows that some people do check their server logs for anomalies and thus suggests that 'noisy' attacks, such as ones requiring a protocol downgrade, are less interesting for those who desperately want to stay under the radar.
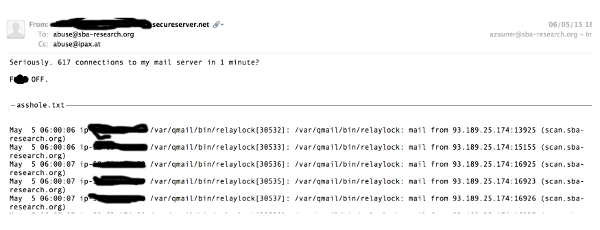
Some people don't respond in a very friendly manner to scans of their mail server.
After three long days, I left Luxembourg with a lot of ideas for new research and a great feeling from all the kind people I met. I also left with a strong desire to come back for the 12th Hack.lu next year.
While writing this blog post ten days after the event, Xavier Mertens's conference blogs (day 1, 2, 3) were very helpful. Slides from many talks are available here.
Posted on 02 November 2015 by Martijn Grooten