Posted by Martijn Grooten on Feb 18, 2016
Google's Android operating system may have a bit of a bad reputation when it comes to security, but it's worth noting that recent versions of the operating system have been hardened a lot.
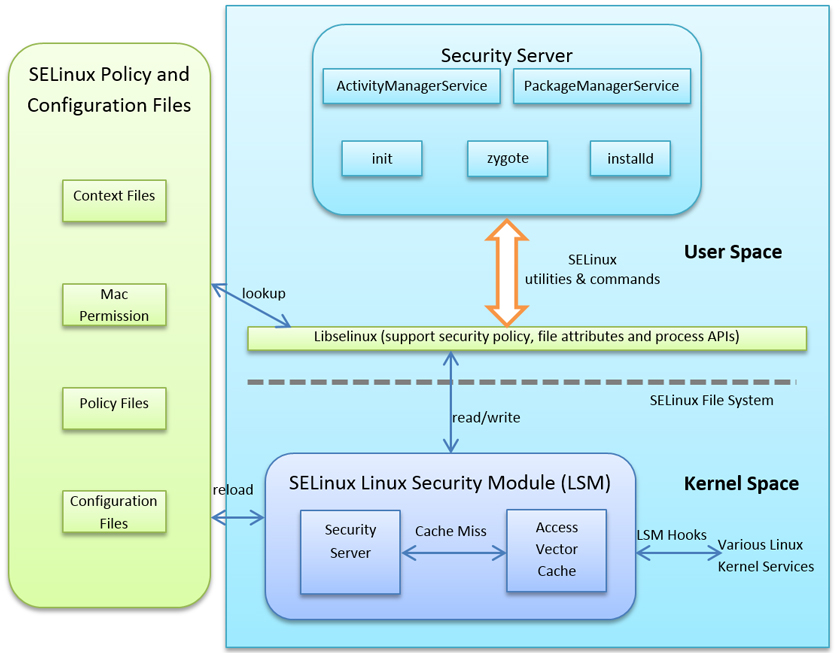
In a paper presented at VB2015, Sophos researchers Rowland Yu and William Lee look at two recent security enhancements, Security Enhancements for Android (SEAndroid) and containerization, and ask whether they will be able to stop future malware targeting Android. Based on how existing Android malware gets onto the operating system, they conclude that these enhancements won't be sufficient to keep either current or future malware out.
You can read their paper "Will Android Trojans, Worms or Rootkits Survive in SEAndroid and Containerization?" here in HTML format or here as a PDF, and find the video on our YouTube channel, or embedded below.
If you're interested in Android malware, don't forget to read Rowland Yu's VB2014 paper "Android packers: facing the challenges, building solutions", or watch him discuss Android malware at RSA next month.
Are you interested in presenting your research at the upcoming Virus Bulletin conference (VB2016), in Denver 5-7 October 2016? The call for papers is now open.