Posted by Martijn Grooten on Jan 31, 2017
While avoiding the use of Flash is good advice for helping to fend off exploit kits, some of the vulnerabilities exploited by these kits actually target the browsers themselves. An important example of this is CVE-2016-0189, which affects Microsoft's Internet Explorer browser versions 9 through 11.
First discovered in the wild in targeted attacks in South Korea, the vulnerability was patched by Microsoft in May 2016 and started being used in exploit kits not long thereafter. It proved to be one of the most popular vulnerabilities for exploit kits in 2016.
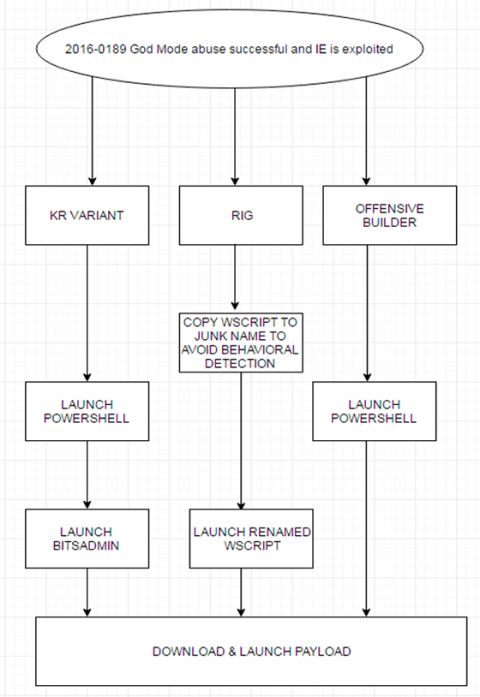
Today, we publish a paper (HTML and PDF) by FireEye researchers Ankit Anubhav and Manish Sardiwal, who thoroughly analyse this 'God Mode' vulnerability and explain what made it so popular in the cybercriminal ecosystem. Though this particular vulnerability may be on its last legs, it provides some important lessons, not just technically but also when it comes to understanding cybercrime.
If you have some research you'd like to share with the security community, we'd love to hear from you. Why not submit a paper for publication in Virus Bulletin or submit a proposal for VB2017.