Posted by Martijn Grooten on Mar 28, 2017
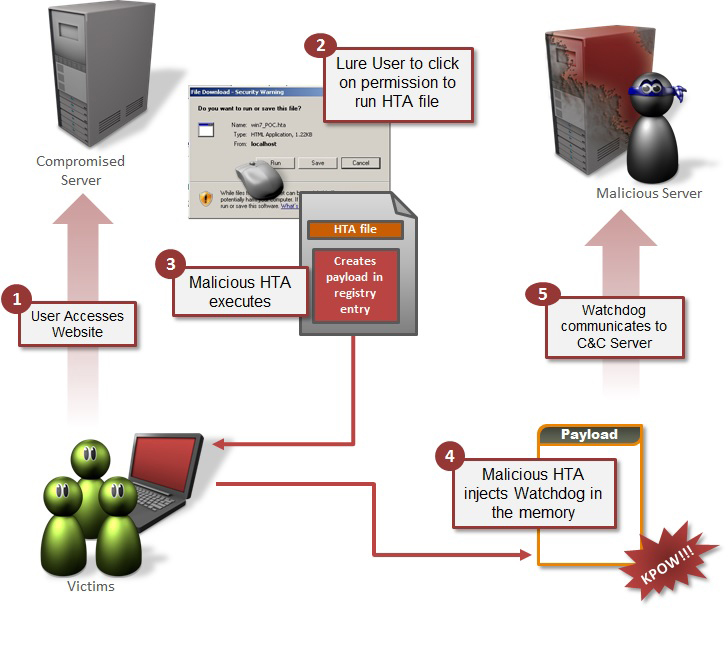
Over the last few years, we have seen a sharp increase in 'fileless' infections, where a machine is compromised without a malicious file ever being written to disk. Though not impossible to detect and prevent, they do require a security product.
In a paper entitled "One-click fileless infection" presented at VB2016 in Denver, Symantec researchers Himanshu Anand and Chastine Menrige discuss fileless malware infections in general and one kind in particular, where it meets one-click fraud to become one-click fileless infection: an infection where a single click is enough for a device to become infected, and no malicious file is written to disk.
Today, we publish their paper in both HTML and PDF format. We have also uploaded the video of their presentation to our YouTube channel.
The programme for VB2017, which will take place 4-6 October in Madrid, Spain, will be published next month. Registration for the conference will also open in April.