Posted by Martijn Grooten on Sep 19, 2017
Six years ago (coincidentally the last time the VB conference was held in Spain) saw the first VB conference paper presented on Android malware, which at that time was still an esoteric and mostly theoretical threat. Things have changed a lot in the last six years – something that is perhaps best illustrated by Google's open approach to the subject: this year's programme includes a last-minute paper by Google's Jason Woloz, in which he will present the company's Android malware statistics.
The rise of Android malware has also led to a number of researchers specializing in this area, one of the most prominent being Fortinet's Axelle Apvrille, who writes and speaks regularly about threats against both mobile and IoT devices – something she combined in her VB2016 paper.
Axelle is back on the VB2017 programme, this time to present a paper in which she shares the tools she uses to reverse engineer Android malware. In particular, she focuses on tools that may be less obvious in their use for this purpose, including Docker and Radare. Axelle's paper, and her presentation in Madrid, promise to be valuable for both beginners and those who are already well-versed in analysing Android malware.
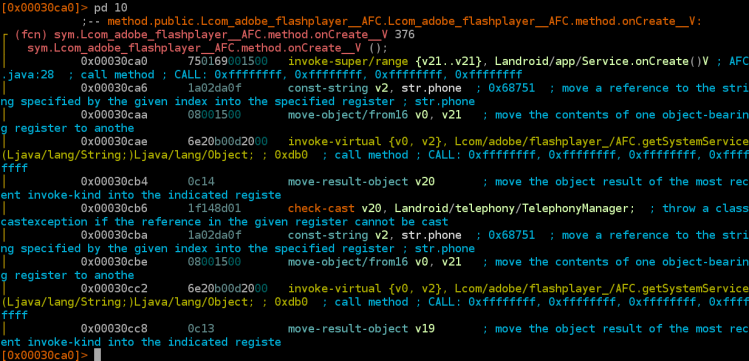
Android/Crosate disassembled by Radare2.
To see Axelle share her tools and tricks, and to listen to more than 50 other speakers discussing the latest threats and the tools to fight them, register now for VB2017. And to get in the mood, why not watch the video of Axelle speaking at VB2016 in Denver?: