Posted by Martijn Grooten on Feb 7, 2018
In December last year, a joint operation involving law enforcement agencies and many security firms led to the dismantling of the Andromeda botnet, also known as Gamarue or Wauchos.
Such takedowns have become a common feature in the fight against online crime, though there have been many instances where a disrupted botnet has subsequently been resurrected. That's unlikely to happen in this case though, as in the same month as the takedown, the suspected owner of the botnet was arrested in Belarus.
The fact that it seems likely we have seen the end of Andromeda makes this a good opportunity to look back at the botnet which, for more than half a decade, plagued computer users around the globe.
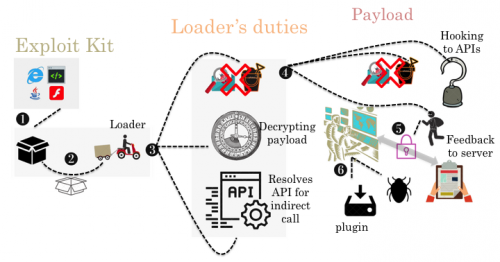
Andromeda at a glance.
Today, we publish an analysis of Andromeda by Fortinet researchers Bahare Sabouri and He Xu, in which they look at the malware, its anti-analysis tricks, its C&C traffic, and how it has evolved over the years. The article is published both in HTML and PDF format.
If you have analysed a malware family, or looked at a threat campaign, why not submit a paper for VB2018, which will take place in Montreal in October? The Call for Papers is open until 18 March 2018.