2005-09-01
Abstract
Detailed testing and analysis of McAfee VirusScan Online.
Copyright © 2005 Virus Bulletin
It has been some time since a McAfee product has been the subject of a standalone review in VB, hence the return to its study. The look and feel of McAfee's corporate products have changed relatively little during that period and, while there have been additions to the feature set, and the particular flavour-of-the-month requirements of the market have stressed different aspects of the product, a user from several years ago would be able to launch and use today's version of VirusScan Corporate Edition without much confusion. This is good news for corporate users, but not so good for a reviewer looking for impressive changes to describe. Therefore, it is the home-user version of the software that is under review here, the 'Online' appellation arising from the ability to install VirusScan directly from the Internet.
In addition to the VirusScan product for home users, McAfee also offers a personal firewall, anti-spam product and an anti-spyware product. These can be purchased as a bundle or as more of a mix-and-match set of products. These products will be mentioned in the text, but were not tested.
As the product name suggests, the method of installation for this test was directly from the Internet. In theory, the user heads to the McAfee website, enters their login details and the installation process proceeds in a matter of a few mouse clicks. Unfortunately my experience of installation was not ideal, although it is unlikely that many home users will encounter the same number of problems, since they are likely to have different default settings on their machines.
The first problem occurred when I used my default browser, Mozilla Firefox, to access the McAfee website. Although the login process was reached with no problems, an error page came directly after this, stating that Internet Explorer was required for operation. Grumbling somewhat, I launched IE and stumbled again - this time after the licence agreement had been accepted. In this case my faux pas was that I had chosen to leave ActiveX disabled.
Although not totally unexpected, the fussiness of the installation process was ironic on two fronts. First, the use of Firefox and disabling of ActiveX are both recommended as easy ways to lessen the inherent security risks which beset anyone surfing the Internet. Relaxing security in order to install security products has always caused me wry amusement. The second, rather more interesting irony of the situation came as I explored other parts of the McAfee site.
An affiliate of McAfee offers an Internet security program, SecureIE, which is advertised on several pages of the main website. The advertisements lead to external pages where a routine 'security check' of one's computer is offered. Imagine my surprise when, with no settings changed within IE , the SecureIE page declared that I was running the risk of ActiveX affecting my machine maliciously. The security on my machine was both too great to install McAfee software and too little to suffice according to McAfee's affiliate - an interesting paradox.
Having instructed IE to accept the ActiveX control in question, the installation continued momentarily before announcing that pop-up blocking (which is standard as part of XP SP2) was rendering the installation process impossible. It was no surprise, considering the way things had progressed thus far, that the suggested solution was to disable this security feature until installation had been completed. I selected the option to allow pop-ups temporarily through the information bar which IE creates as part of the blocking process, and at this point the VirusScan Installation Wizard arrived on the scene.
The installation process was described as taking around 30 minutes on a 56Kbit dial-up connection, which seemed rather an optimistic estimate considering that the download time on a 1Mbit connection was close to five minutes. Nevertheless, this is remarkably speedy considering the size McAfee products have been in the past. Clearly some paring down has been done for the sake of efficiency.
I was a little surprised that, until this point, there had been no warning about other security products that may be installed on the machine. The warning comes on completion of the download phase. Since I am naturally paranoid, and I was using a test machine which is not totally expendable, my machine was already protected by a competing product. McAfee's installation routine detected this and announced that the product should be removed, stating rather sternly that VirusScan would not function correctly if the competing product were not disposed of. This is a little worrying, since if Microsoft's anti-virus APIs are implemented and interfaced with properly, two or more on-access scanners should be able to exist side by side. Either McAfee has no great confidence in some part of the process, or the appearance of this message is dependent upon the product detected, with a known issue having been discovered at some point.
The uninstallation of the other product triggered XP SP2's various warnings about the subsequent lack of protection. The lack of protection was something of a concern for me, although I suspect that changing from one anti-virus developer to another is not a situation encountered very often by the majority of home users.
In any case, the machine reboots speedily after the uninstallation, so that the installation of VirusScan can proceed. Several installation selections are made after reboot and before installation, however, which delays the process of restoring on-access functionality to the machine. It would be more sensible to relocate these choices to a less time-sensitive part of the installation process - after all, the creation of a desktop icon and participation in the Virus Map scheme are not particularly good reasons for keeping the machine unprotected.
The next stage consists of the installation of McAfee SecurityCenter. While the McAfee SecurityCenter may be installed in addition to the Windows SP2 Security Center, the installation dialog recommends that the Windows version is disabled so as to avoid duplicate security status messages. (Although the disabling of the Windows Security Center is at least automatically reversed if SecurityCenter is removed at a later stage.)
After this choice is made, a rather belated informational dialog arrives, detailing the capabilities of the McAfee SecurityCenter. It would have been much more useful to have been presented with this dialog before having to decide whether it should be the default area for such operations.
After this rather long series of events, VirusScan is installed fully on the target machine. A final dialog box is all that remains, offering a full scan for viruses and 'What's new?' information. Considering the unprotected state of the machine during parts of the installation procedure, it seemed wise to accept the scan.
Updates are checked each day by default, with pop-up warnings in the case of outbreaks being declared. Somewhat oddly, the pop-up for obtaining protection from these new threats does not link to a download site, but instead to the area on the McAfee site where the product may be purchased. Presumably the pop-ups are produced by the Security Center without reference to the presence or otherwise of VirusScan.
As indicated, this version of VirusScan assumes that there is an Internet connection. Indeed, the operation of VirusScan and much of the additional content linked from within alerts and the SecurityCenter require the presence of an always-on Internet connection in order to be of any value. For example, the option exists to test whether VirusScan is installed correctly. This relies on downloading a file from the McAfee website, having been directed automatically to the correct page by the SecurityCenter. Clearly this can operate only if the machine is connected to the Internet.
One notable feature of the McAfee web presence is the distribution of information over different sites - when installing and updating the corporate product, for example, it is necessary to visit, at the very minimum, the sites secure.nai.com and www.mcafeesecurity.com. This splitting of operations across sites also occurs in the informational aspect of the sites. If, when searching for virus information, one starts at www.mcafee.com, the journey will take one through www.avertlabs.com before arriving at the information on vil.nai.com.
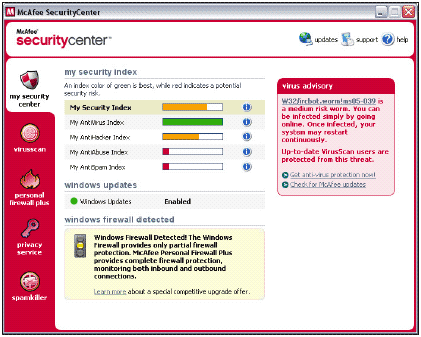
This maze-like aspect of the websites is a shame, since the content of the informational parts is among the best available. The vil.nai.com site contains the main virus information library, together with numerous tools and associated information sources. Also disappointing is the lack of true Firefox compatibility - several pages looked rather odd when viewed through Firefox rather than IE .

The main interfaces for the operation of VirusScan come through McAfee SecurityCenter and the default scan. Both are available from desktop links and from the start menu. The SecurityCenter is also available as a tray icon. The Start menu contains the options to create a rescue disk, manage quarantined files and the on-access scanner ActiveShield. In a departure from McAfee tradition, the on-access scanner does not have its own shield tray icon. Perhaps this is just as well, since these days red and yellow shields in the tray are signs that something untoward is afoot on the security front - imagine the panic that might be engendered by a red, white and silver shield.
The SecurityCenter default view is 'my security center', which is dominated by the combination of five status bars, an advert for McAfee Personal Firewall Plus and the latest virus advisory. The activation of Windows Update here warrants an unobtrusive green blob on this page.
With VirusScan installed, only one of the status bars showed green, this being the AntiVirus Index. Windows Firewall on its own rated a medium level of protection in the AntiHacker Index, while the AntiAbuse and AntiSpam indices rated no protection. This came as little surprise, since the programs that had been offering protection in these areas had been removed, since they were part of a competing anti-virus product. Clicking on these indices produces information about any related problems and how they might be rectified. However, rather than providing unbiased or useful information, this feature seems to have been hijacked by McAfee's marketing department as a method of displaying advertising copy for other McAfee products. In particular it surprised me to discover quite how much I needed to purchase McAfee Spamkiller when no email client was in use on the machine in question.
In addition to the 'my security center' tab, there are views for VirusScan, personal firewall plus, privacy service and spamkiller. Cynical readers will note that these are all the names of McAfee products rather than generic descriptions. McAfee's reason for suggesting that SecurityCenter is installed and Microsoft Security Center is disposed of becomes altogether obvious at this point. Having resolved to slay another few marketing executives before breakfast I moved quickly on to the VirusScan view.
Unusually for an anti-virus product, the status of the product is given pride of place in this view, the same traffic-light symbol being used here as elsewhere in the interface. Below this are the actions available, each with a short description of its functionality. The most obvious option for inclusion here is scanning for viruses. The scanning also includes detection of what are termed 'PUPS' when detected, this derived from 'potentially unwanted programs'. One hopes that this designation is broad enough while not too damning of objects detected by VirusScan. In the current climate it is a short step from an overly harsh description of an application to the courtroom.
Within the scanning section the options are more clearly set out than in the corporate product, though they are fewer in number. Recursion of scanning, scanning of all files, compressed file scanning and heuristic activation are all supported. Together with the selection of scanning for PUPs, however, this is the full range of detection options on offer. Location can be selected, of course, though there are no options here as to the action to take upon detecting malicious files.
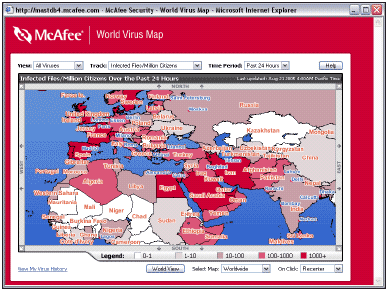
For a greater variety of options a separate view is available from the VirusScan tab. This is not an area where significant changes may be instituted, however. Areas where on-access scanning will be performed are adjustable, as are the parameters for scheduled scans. No scheduled scan is activated by default. There is a preset scheduled scan which may be activated, however. This is timed to occur at 8pm on a Friday. This seems strange timing for a product aimed at home users, since one might expect home users to be more likely to be using their machines then than at many other times or on other days of the week - and while an on-demand scan is in operation other applications certainly feel the strain. Virus Map reporting may also be deactivated here, or set to a different reporting location.
The Virus Map is viewed through another of the parts of the VirusScan tab. The information contained here is very interesting, though it would be more so if there were finer granularity in the data reported. The location data as entered in the registration process distinguishes between US states, for example. However, the Virus Map indicates that the whole of the USA has the same level of virus detections - it would be useful to know whether this is because the data applies only to the US en masse, or whether each state does indeed have over 1,000 infected computers per million citizens.
The VirusScan tab provides a link to virus information. Strangely, this does not take the user to vil.nai.com but to a rather more rounded, pastel-coloured interface at us.mcafee.com. It seems that vil.nai.com is reserved for enterprise users rather than home users or small businesses, although the virus information on both sites looks, reassuringly, as if it has been pulled from the same database.
The remaining three areas which can be reached through the VirusScan tab are the Test VirusScan page, version details of VirusScan and the area where a rescue disk may be created. Incidentally, the file used to test the detection capability at this point is not the EICAR test file but an in-house McAfee creation, which is 24KB in size. The machine I was using did not possess a floppy drive, so the rescue disk functionality could not be tested. Since machines are increasingly likely to have a CD or DVD writer instead of a floppy drive, some method of burning a rescue CD would be a wise addition.
Although in the past McAfee's various product lines have been increasingly inclusive of all possible security functions, the version on offer here seemed very much limited to anti-virus. This is not to say that the integration of extra products is not supported - quite the opposite in fact. It is very strange, however, to see the parts of the McAfee Security Center where these extras can be bolted on.
The provision of options for firewalls etc. in the SecurityCenter set me pondering. What happens if, for example, I wish to retain McAfee's anti-virus product, but use a different vendor for each of anti-spam software, firewall and privacy protection? The Microsoft Security Center supports only two of these functions but currently does allow for a software firewall and anti-virus product from different vendors. Matters may become more complicated when Microsoft's anti-spyware product finally arrives. Logic would, however, mark this as a perfect time for Microsoft to expand the Security Center's coverage to include anti-spyware. This would be one more reason to reject the McAfee version and opt for Microsoft 's offering.
While reading through the comments I have made in this review, I notice that many of them point out foibles in the product that caused me to feel uneasy. Usually I am quite happy for the reader to share my disappointment with a product, but in this case my overall impression of VirusScan was less negative than my comments might suggest. The heart of VirusScan is well constructed and designed, and I certainly find it more user-friendly than the corporate versions.
Test environment. Athlon 64 3800+ with 1 MB RAM, 80 GB hard drive, CD/DVD ROM drive, 1Mbit ADSL connection, running Windows XP Professional, Service Pack 2.
Product. McAfee VirusScan 10.0.25 Engine 4400 DAT 4563.
Developer. McAfee Inc, Freedom Circle, Santa Clara, CA 95054, USA. Tel: +1 888 8478766, email: <[email protected]>, web: http://www.mcafee.com/