2006-01-01
Abstract
VB usually shies away from the testing of beta products, but the beta release of Microsoft's anti-virus offering OneCare Live proved to be just too tempting. Matt Ham describes his findings when he put OneCare Live under the microscope.
Copyright © 2006 Virus Bulletin
It has been something of an open secret for a while that some form of Microsoft anti-virus is on its way, though further details have been less forthcoming. Even now, after the beta release of Windows OneCare Live, the area of Microsoft's main website dedicated to security has no obvious links to the product – which is somewhat mystifying since reference to the company's anti-spyware product (also in beta) is hard to miss.
As many readers will remember, there was a previous Microsoft anti-virus product, which was released more than ten years ago. However, the product in question was doomed to vilification since it remained unchanged during a long period of OS production and there was no easy method of updating it. However, times have moved on and it is to be expected that the new beta will make full use of today’s prevalence of Internet connections for retrieving its updates.
For Microsoft, OS integration is not the simple matter it is for many producers, since legal as well as functional issues come into play. Complete separation of the product from the OS would be likely to put off potential users, while too tight a binding to the internal workings and external tools could see Microsoft charged with unfair competitive practices.
Thus before settling down with the product I already had a few expectations and uncertainties. Since the release of Windows XP Service Pack 2, the Windows Security Center (WSC) has been the hub of security configuration and status reporting on the XP platform. I would expect any anti-virus functionality to integrate into the WSC at the very least, but total replacement of the WSC, as in McAfee's consumer product, seemed unlikely (thus avoiding accusations of elbowing out competing products that do use the WSC).
Perhaps of more concern was the question of how the anti-virus and anti-spyware products would co-exist. The anti-spyware beta application is fully standalone. However, both products contain on-access scanners and both might conceivably attempt to detect files that are related to spyware and demonstrate viral replication. The anti-spyware functionality includes some fairly extensive behaviour blocking in addition, some of which may be anti-viral in effect, if not in intention.
With these thoughts in mind I proceeded to the somewhat hidden OneCare beta site. I must stress at this stage that the product is in beta and thus major changes may occur even between the time I write this review and the time it is published. Comments here are thus an initial view and are by no means (even less than usual) intended to be a buyers' guide to the product.
The version I tested was updated several times during the testing process, with both the base product and the definitions being changed. All comments made here refer to the final version that was installed. Newer versions may, of course, differ considerably. The operating system used was Windows XP Professional Service Pack 2, with all updates applied using Windows Update. Windows OneCare is available from http://beta.windowsonecare.com/.
The use of Firefox on web-based installation routines seems to be a method destined to failure. This fussiness does not come as a surprise at beta stage, but I fear the situation will change little in the full release if my recent experiences with other developers are typical. In this case the installation platform is not checked until after the user has supplied an email address – so it seems that those who refuse to use Internet Explorer will be subjected to emails concerning the beta despite not being able to install the software.
Thus I reverted to my copy of Internet Explorer, which in the past has been subject to a variety of extremely lax security settings, all of which were demanded for the installation of security products. However, in this case there is no need to change settings from the application’s default values, which is a relief on the security front. It is noted before installation begins that automatic updates are activated as a part of the installation process, not only for OneCare but for all Microsoft products. This is not a bad default setting, and I am surprised it was not made into a difficult-to-disable default within SP2.
The next stage is an automatic check that the machine in question reaches installation requirements – though no information is given as to what is being checked. However, any problems relating to browsers and OneCare already being installed are picked up at this point. At the moment OneCare does not support updating by overwriting an existing OneCare installation, though this is likely to change with the full release. If it doesn't, there is the potential for chaos should uninstallation files for OneCare be corrupted and OneCare itself also be in need of reinstallation. Perhaps not very likely through fate alone, but not entirely unlikely if malware is targeting the application.
After this check comes another, this time requiring an ActiveX application in order to check machine hardware and software details. Privacy fanatics will note that this gathers and sends various pieces of personal information as it executes, with the usual 'we will not share this information' caveat being given in the small print. This is also the stage at which any other anti-virus products on the system are detected and declared to be bad things which must be expunged. Once the ActiveX has been approved and installed the process here is fast and leads, if the checks are all passed, to the licence agreement.
After this, files are downloaded for installation. Installation is confirmed by the presence of a small green icon on the task bar. Many of the status notifications are also seen here, in the form of the infamous popup information bubbles.
The add/remove programs dialog gives the size of the OneCare package as 129 MB, though the initial download is certainly smaller than this with typical download times of only a few minutes at 1 MB/s download speeds. After download, the installation process is almost instant and requires only a reboot for completion. No other settings are tweakable here, which, again, may be something that is unique to the beta version. One feature of the method of installation used here is that installation onto standalone machines is currently not possible. Installation requires an active Internet connection.
Uninstallation of OneCare is short but simple and understandably requires a reboot as part of the process. The reboot can be delayed, which may be convenient, but this does result in a machine with no active firewall or anti-virus software until the reboot is performed. The reboot dialog states that network connections may fail until a reboot has been performed, though this did not seem to be the case. It would be better, from a security point of view, if network connections were terminated until reboot.
As might be expected, updates are automatic, although the process is rather mysterious. In this version there are no options beyond what amount to: updates on, updates off and look for updates now. These three are certainly enough, though the lack of an ability to set parameters for updates seems very strange when one is accustomed to dealing with the ultra-tweakable anti-virus packages of today.
Updates are not limited to those which affect OneCare directly. Urgent Windows updates are also checked, effectively duplicating some of the functionality of Windows Update.
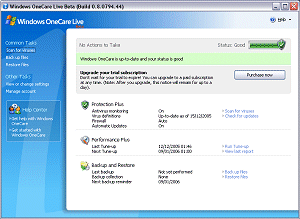
The mention of the update mechanisms just made will give some idea as to how much the product interacts with other established parts of the operating system. The main interface, for example, bears more than a passing resemblance to the Windows Security Center due to the presence of a large green (or red) shield in a three-part list of functions. In fact, the resemblance between the two interfaces is not so great upon closer inspection but is enhanced by the left-hand control pane, right-hand status view configuration.
The left-hand pane contains various actions and is, in effect, a set of short cuts to various likely actions and links to useful sources of information. Documentation is not yet in the form of a context-sensitive help system but rather through hyperlinks within the various dialogs. The links here take the user directly to the highest level entries in the help resources. The View or Change Settings Dialog is also positioned here, though to reduce confusion, the configuration changes possible here are included when the functionality is discussed in the right-pane description.
The right-hand pane is dominated by the status slider, which in my experience had only two positions – green where everything is approved in its settings, and red when any security setting is lessened. There is also an option to upgrade the subscription under which OneCare is being used, (obviously not relevant in the beta product). The three areas below this for which status is shown are Protection Plus, Performance Plus and Backup and Restore. For the purposes of this overview the latter two were not given much attention, though it is appropriate to mention them before heading to the more overtly security-relevant portions.
Performance Plus contains one anti-virus related function: that of a scheduled scan of the machine. However, this is combined with yet another scheduled check for updates, defragmentation of disks if required, automatic run of the backup application and an optional cleanup – deleting files that are presumably unnecessary. Each of these processes on its own can be something of a system hog. Combining these is clearly going to make the affair very burdensome indeed on system resources and the documentation for this area states that it might be best to allow the process to run unattended. Having seen the effect of such a tune-up in progress, I can say that this 'recommendation' is actually a necessity on all but very high-end machines.
Backup and Restore does very much what its name suggests. Backups are very useful in cases where files have been devastated by malware, though this particular backup method does seem somewhat limited in that it requires OneCare to be present for the retrieval of files. This makes the functionality less useful for system recovery and rather more for pure data recovery.
Protection Plus consists of on-access scanning, virus definition updates and, yet again, general updates for OneCare. It certainly seems that updates are one of the most stressed aspects of the application. Given the number of non-updated anti-virus applications that have given false security over the years, this is definitely a good thing (although, ironically, one of the first sources of this false security was the original Microsoft AntiVirus). Somewhat surprisingly this is an area where there is very little to comment upon and even less to see. On-access scanning is either on or off as a general setting. In addition, heuristics may be disabled, the default state being enabled.
It is also possible to specify exceptions for scanning here, though it seems that whole drives cannot be selected, nor indeed can anything but individual files. This is a simplistic and potentially irritating way of dealing with exclusions, though likely to encourage exclusions for only a very small number of files.
It is obvious from this list of configurable features that the anti-virus functionality is not really designed to be messed around with, the user having to be content that Microsoft has chosen appropriate settings. In all honesty this is probably the best way to deal with the majority of customers. Unfortunately a vocal minority is almost certain to complain about the lack of features, believing that more is always better, even for the most technically philistine user.
The firewall function of OneCare replaces rather than complementing the existing Windows Firewall, which surprised me. I certainly can't see people being persuaded to buy OneCare based on it having a firewall included when one is available already, free of charge, from the same vendor. This aside, the OneCare firewall integrates with the WSC as would be expected. Firewall settings are controlled through the same menu as the anti-virus functionality already mentioned.
Three sensitivity settings are provided. The first one, off, requires little explanation. The automatic setting is the default, which allows programs access to the Internet if they are known or are given explicit permission. Permission may be granted manually through this interface or, more usually, when the application is first used. Permissions may be enabled or disabled on an individual basis through the GUI, or deleted totally. Blocking here occurs immediately if permissions are rescinded, even if the connection has already been opened by the application in question. The more stringent Prompt setting does not allow any program to access the net without manual permission on every occasion.
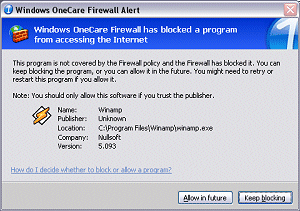
The firewall settings are slightly different from those supplied by the built-in Windows Firewall, in both good and irritating ways. For example, exceptions from blocking are not simply triggered by filename but are rechecked if an application is patched or overwritten. This seals a major flaw in the old firewall, where malware could simply replace an allowed application and trigger no alerts when accessing the net.
On the more irritating side is the fact that Microsoft products – Windows AntiSpyware and Internet Explorer for example – are allowed access to the net automatically, while their non-Microsoft equivalents (Firefox being a prime example) cause warnings to erupt on first use. Obviously Microsoft is able to verify the trustworthiness of its own applications, with other products being less easily declared as benign. However, it would be nice at some point for OneCare to include a list of commonly used exceptions for blocking which were not necessarily created by Microsoft.
More interestingly, although OneCare is aware of Windows AntiSpyware the reverse is not the case. During initial use of OneCare several of its activities were flagged as worthy of attention by AntiSpyware's behaviour analysis.
When run against the Virus Bulletin In the Wild test set as used in the most recent comparative review (see VB, December 2005, p. 16), results were initially difficult to determine due to the lack of any real logging. However, after further investigation it was determined that the scanner had missed detection of one sample of W32/Argobot and two samples of W32/Mytob.
Conclusions seem somewhat premature, though some general thoughts occurred to me while inspecting the features of Windows OneCare. First is that this is obviously designed to be as simple as possible to operate. The installation procedure is very much click-and-forget and the update procedures are not only automated but improve upon the updates for other Windows components. Certainly it makes sense for the anti-virus application to ensure that patches are applied before a virus is on the machine rather than taking action when the machine is infected.
Questions remain, however, as to how the product will interact with existing security applications. Including anti-virus and firewall functions in OneCare, while having a completely separate anti-spyware product seems unneccesarily confusing. The similarity between the OneCare interface and the Windows Security Center might mean that it will be either merged with, or replace, that application, or the similarity might simply be an effort to maintain a coherent look and feel. Thankfully, the beta state of the product makes answers to these questions impossible, so I can sleep soundly despite not knowing the answers.
Test environment: AMD64 3800+ machine with 1 GB RAM, 80 GB hard disk, DVD/CD-ROM and 1 MBit ADSL Internet connection running Windows XP Professional SP2.
Developer: Microsoft, One Microsoft Way, Redmond, WA 98052, USA. Website http://beta.windowsonecare.com/.