2007-03-01
Abstract
John Hawes takes an indepth look at AEC's TrustPort Workstation.
Copyright © 2007 Virus Bulletin
One of my first duties, on taking over the running of the VB100 testing program, was to liaise with vendors regarding the last round of tests carried out by my predecessor. One such vendor was AEC, whose TrustPort product had narrowly missed achieving VB100 certification. The product’s developers were understandably somewhat bemused by this, as two other products whose engines are used by TrustPort had scored significantly better results. Some analysis revealed that much of the problem was due to certain file types not being scanned by default. TrustPort was submitted for testing again a few months later, and this time suffered no such difficulties, with splendid detection rates across the test sets.
After looking at the product in some detail during this period, I was intrigued by the concept of rolling multiple detection engines into one product. How, I wondered, did the improved detection balance with the additional overhead? When I learnt that TrustPort’s anti-virus functionality was not the entire offering – and was, in fact, generally only available as part of a larger product with a range of diverse and unusual components – I resolved to get hold of a copy for deeper investigation.
AEC, founded in 1991 and headquartered in the Czech Republic city of Brno, describes itself as a ‘Data Security Company’. The company started out as a reseller of anti-virus software, and has added further security offerings to its portfolio over the years.
AEC began developing its own anti-virus product in 2003, and the TrustPort Workstation offering is the desktop, end-user part of the Phoenix Rebel suite of security tools. The suite bears the bombastic tagline ‘the ultimate security solution’ and a logo theme which appears to show a bald eagle carrying a blue jewel. It includes anti-virus and firewall for servers, gateway products featuring anti-spam, mail and web malware filtering, web access control, and management tools for the control and deployment of these various items. The company also offers a range of security services, including assessment and penetration testing of corporate networks, managed services, and general security consultancy.
Beyond the anti-virus, which is the main focus of this review, the workstation suite contains some rather unusual items. The client firewall is fast becoming a standard part of such desktop security products, and spyware and adware are covered by some of the several engines combined to provide broad malware protection. Desktop web and email filtering (for both malware and spam) are also rolled in as part of the ‘anti-virus’ module. TrustPort’s most interesting aspect is the addition of data encryption, file encryption and signing, and secure shredding, thus placing another layer of security between hackers and sensitive data.
AEC’s website can be found at http://www.aec.cz/ – there are Czech, Slovak and English versions of the site. The English version of the site is a fairly simple, pared-down affair; the home page features links to details of the various product offerings, and some items of company news. Elsewhere on the site, apart from further product details, are: a list of sales partners (most of which are based in eastern Europe, but there are also some in the Middle East and Pacific Rim regions), contact details, pages for upcoming events, and FAQs, the latter two of which were pretty blank and ‘undergoing construction’ when I visited (although there were some entries in the Czech version of the FAQ page).
The complex business of providing information on malware, outbreak alerts and so on is mostly left to the providers of the individual engines used by the product (which are: BitDefender, Ewido, Grisoft and Norman). A support email address is provided on the contacts page (a test query elicited a terse, but accurate response within 12 hours – support for all the products is apparently included with the licence). Trial versions of several products are available to download from the website, following a brief personal details page.
TrustPort Workstation is available from the download site in a single 65MB file. The installer allows for a selection of the modular components to be specified, but defaults to the full set. Installing these in various configurations started simply, with a EULA and selection of components, along with install locations. There followed a selection of options for the eSign module, a list of secure identity management systems for which support is available, including Spyrus, Eutron and Aladdin’s eToken. After that came some setup for the encryption software, the choice of whether to create a new virtual disk or mount an existing one, and then the extraction and installation of files – a fairly rapid process.
Applying updates to the anti-virus portion of the software was the next step, and one which somewhat worryingly reported successful completion on my lab machine, despite there being no possibility that the software had connected to its update source. Thinking this could have been due to some setting of the webserver to which all requests in the lab are redirected, I tried again on entirely unconnected machine, but achieved the same result.
When run later on with a genuine web connection present, updating was much more successful, although a rather lengthy business (which is not surprising, given that four separate engines are used).
Once the product had made contact with its home base in the Czech Republic, it informed me at once that 16MB of update was required, and this chugged slowly onto my machine over the next 45 minutes or so. Each product, it emerged, had its own progress bar, so just as I thought the update was almost complete it would revert to zero and begin on the next set of definitions, engine upgrades and so on. Although I didn’t watch this process too closely, I couldn’t help but notice that one engine (the one provided by BitDefender) reached an impressive 111% before it was completely happy. Another update, a few days later, comprised around 8MB (7MB of which were Norman components) and took only 10 minutes to complete, much of which was in the installation rather than downloading of data.
The final stage of the installation process was the creation of an encrypted ‘volume’, with size limitations and encryption options, including whether to use the AES (Rijndael) or CAST-128 cipher algorithm. A username/password combo was taken for access to the stashed data (without the usual advice on password length or complexity), and a random seed generated. The volume was then created in a matter of a few seconds, and the setup was complete.
Once installation was complete, the reboot that generally follows such a process was not requested. Impressed, I looked around for the anti-virus tools and signs of on-access protection. No new items were in evidence in the system tray, and a quick run of a file-opener utility showed no slowdown in file access, indicating almost certainly that no scanning was taking place.
On searching the programs menu, I found the TrustPort entries, one per module, and in the anti-virus section chose to ‘Open TrustPort Tray’. This added a rather attractive blue gem to the tray, which led to a raft of options for the various components, including a common configuration dialogue. Within here it took a matter of a few clicks to discover that the on-access scanner was in a ‘stopped’ state, with no clear way of starting it.
Rebooting the machine cured this, another (shield-shaped) icon was added to the tray and protection was fully in place. I later discovered that this issue appeared only to affect Windows 2000 installations, and there were no such problems on XP or Vista.
The other components, the shredder and data protection utilities, seemed to be functioning perfectly well on all platforms without reboot, although Vista support is not yet fully rolled out for all the modules. I had a brief look through these prior to running any serious testing, and was again impressed by the range. The firewall offered an extra stash of ‘Network utilities’, and while both the shredder and disk encryption modules seemed fairly simple to operate, the eSign component was less intuitive. It offered a fair few options but it wasn’t immediately obvious how it was supposed to be used, so I resolved to return to it once the main bulk of my testing was complete.
The first thing that struck me when looking into running a few scans over the VB test collections in the lab was that there seems to be no main GUI in the usual sense. Of the two icons dropped into my system tray on install, a shield-shaped one – quite logically used for operating the shields – allowed me only to disable/re-enable on-access and web scanning (these actions were also available to a user without admin rights under Vista). The second icon, a return of the blue gem, led to a tree of options for each product, appropriately shrunk down if only certain modules were installed.
Each section’s options included a ‘configure’ link, which led in turn to a central configuration interface with pages for each module installed. From here settings could be adjusted, with options laid out clearly and logically, allowing a broad range of tweaks and changes without swamping the user with overly technical tables of checkboxes. I noted that this configuration interface was rather slow to open, taking more than 30 seconds on some older systems, but once up it was fairly responsive. The interface was divided into sections, with an opening page describing each and detailing the available options. Somewhat oddly, these descriptions did not link to the sections they covered, which could only be accessed from the tree menu to the left.
Most of the AV part of the GUI made pretty admirable sense – on-demand scans operate by default in full paranoia mode, scanning all files using all engines, including the heuristic and sandbox functionality provided by some. Some options, which I would have assumed to form integral parts of a full anti-virus product’s GUI, were notable by their absence. While there were controls of all the options here, including logging and scheduling of updates, there was no option to schedule regular scans; the ‘scheduler’ page only offered controls for updating. I assumed the controls for scheduling, like immediate scanning, must be set up elsewhere.
For immediate scanning perhaps this is understandable, as it is something required more often by testers than the average person, but there was room for it here and it seemed sensible to have access to a scan while I was playing with the controls for it.
Logging also seemed to be lacking something – although the details of how logs were kept were controlled here, there was no ‘Show me the log now’ button, or even any evidence of where I could find it for myself. Looking later at the firewall section, I found the log for that was easily viewed, and an ‘external file viewer’ was also provided, but that wouldn’t show me the scanning logs, complaining about the format despite it being plain text. A simple button or window on the AV logging screen would make a nice addition.
With the software fully set up, and the controls reasonably well mastered, it was time to run a few scans.
With the settings thus examined, but not changed, I moved back to the system tray icon to find the ‘Scan selected area’ button, and ran it over the test sets. Scans could also be initiated, I found, from the right-click menu in Explorer, which simplified my task somewhat, but scans using both methods took some time to get going (up to a minute on slower systems). I suppose that with such in-depth processing using multiple engines, few users would expect an instant response, and on-demand scanning would in other products mostly be used in a scheduled, once-a-week-in-the-middle-of-the-night kind of way; I could find no scheduler here either though.
Logging, which is viewable from the scan results window if not from the configuration GUI, is presented in a clear and readable XML layout, and also stored as plain text, both of which formats came in handy during testing.
The scans of infected test sets showed an impressively thorough detection rate, with the product having no problems covering the collections. Although I would have expected each of the engines to miss a handful of files from the zoo collections, in this setup they overlapped nicely to cover each other’s shortcomings and ensure full marks for the product as a whole. Even in a non-updated state, nothing was missed in the sets used for the last VB100 review (perhaps unsurprisingly, as the shipped version included data from early January, just prior to the deadline for the comparative review). The addition of files from the latest WildLists and other more recent samples caused no problems either; all the newer samples were also detected, with several picked up either generically, as members of known families, or using the deep and sophisticated heuristics available – it was notable that a number of these were not spotted by the on-access scanner.
On-access scanning is designed with a lower overhead in mind, and by default only the Grisoft and Norman engines are active, although the others can easily be activated from the ‘engines’ tab of the config dialogue. Further on-access scanning options, such as the scanning of compressed files and use of heuristics, are also easily enabled.
The use of multiple engines is, of course, certain to add to the system overhead. An on-demand scan using the full paranoia settings is likely to be fairly slow, but sure. On access, however, there is a more significant impact on one’s user experience, and I was intrigued to see what kind of impact the product would make on a system. Running speed tests identical to those included in the last VB100 comparative review, I produced results for on-demand scanning, using the default full settings and full set of engines, and then for the separate engines running alone – the results for Norman and Grisoft are particularly interesting, as directly comparable data from the Vista test is available (see VB, February 2007, p.14).
I also measured on-access slowdown, in several configurations – the default, with two engines scanning by file type; the same with all files being scanned; then all four engines, scanning all files, but without heuristic/sandbox detection enabled; and finally equivalent settings to the on-demand scan, with all detection powers up to the max. The results are shown in the graphs below.
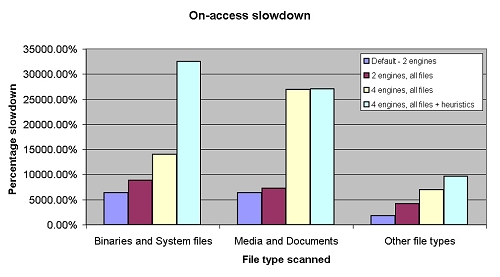
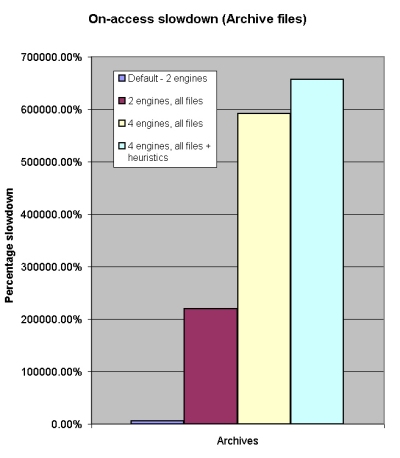
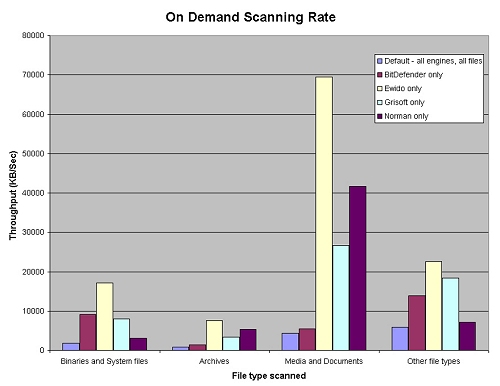
I was pleasantly surprised to observe that, despite the quadruple engines, scanning speeds were by no means sluggish, and on-access overhead, except in the most intensive modes, compared pretty favourably with many of the products tested in the same way last month. With all engines running, especially over archives, things did get fairly slow, but on demand with this setting a very respectable set of times were recorded. Indeed, figures for Grisoft and Norman were in some cases better than those recorded by the engine developers’ own products, although this may have to do with vagaries of implementation – despite the archive settings being left in the default, with all types scanned to unlimited depth, BitDefender found a significantly higher number of files and, from a visual inspection at least, seemed to be recursing deeper into a wider range of compression types. The Ewido anti-spyware engine, run alone, seemed to have no archive-scanning features at all, accounting for some further anomalies in the speed charts.
Of course, the other flipside of having multiple engines to increase one’s chance of catching malware is the similarly multiplied chance of a false positive. The Norman engine suffered such an event in the Vista comparative last month, and Trustport had the same result, detecting a trojan, somewhat ironically, in a piece of software provided by BitDefender. Consultation between VB and developers at Norman has since had this problem fixed, as a quick check with a fully updated version proved, and no further false positives were produced by the team of scanners.
Many ‘Internet Security’ products make much of their multiple offerings, with anti-spyware, anti-spam, web malware filtering and firewalls rolled into a mighty product with spacious tabbed pages on the interface dedicated to controlling each of these aspects. Of these, TrustPort considers only the firewall to be a separate component. All the malware and spam filtering is combined, rather modestly, into the ‘anti-virus’ module, irrespective of the vector.
The firewall offers all the standard functionality of such things, with protocols and ports to block or allow traffic. Configuration seemed even more complex than is usual with such things, but a nice simple slider was provided, with options from blocking all traffic to allowing everything, with allowing all outbound or applying the default rules in between.
Beside the controls for the firewall itself, this section had more surprise goodies; in addition to the standard controls over access ports and connections, a handful of extra tools were included. Alongside some statistics and detail on traffic hitting the firewall, including data types and sources, are a selection of other ‘network utilities’, including simple interfaces to ping and whois, and a geographical lookup system. These were fun little tools, and probably quite useful on occasion, for checking out a suspicious IP address recorded on the connections list. It would have been more usable had the individual items been more closely integrated – for example, the ability to right-click on an address listed as trying to connect to my machine, and perform lookup and geographical search operations to help figure out why, would have been more useful than needing to note down addresses and type them in afresh into a separate box.
The DataShredder utility is a simple tool, with a list of areas available for utter destruction. These include temporary files and folders, recycle bins, and histories, which could be shredded en masse or by individual area, and using a range of shredding methods. The default is the US Department of Defense approved method of running seven passes over the data. A quick version, with a single pass, is also possible, while for the most paranoid the Guttman method can be chosen. The description of this method reads: ‘This method is suggested by Peter Guttman. It’s very secure’, and indeed it is, running no less than 35 passes over data to ensure absolute deletion.
I had a moment of confusion when running the program – having seen several options on the config screen relating to logging, I noticed that before starting its actions the product prompted for a log to write to, starting a browse window, for some reason, in the log folder of the anti-virus component. Browsing for a file with the required (.rpt) extension proved fruitless, and finally I realised that I had to create one for myself, with whatever name I fancied.
The shredding process now commenced, and using the DoD method I trashed all old data from an aging and very full machine (this took quite some time), and was quite astonished to see it rubbing out the traces of files I was sure I’d deleted at least two years previously. Considering the amount of data I’ve added to and removed from the drive since then, it seemed remarkable that any trace was still there – it has most definitely gone now. A context-menu option is also available on right-click within Explorer, to delete files securely at will.
The disk encryption system was similarly straightforward. A volume is created, with two types of ciphering available, and locked down with a username and password. This can then be mounted as a simple additional drive, and files stored in it in the normal way, and when unmounted this data is safe from all but the most expert and patient of information thieves. A number of such drives can be created, and transported as simple files from place to place; mounting can take place automatically on startup, and unmounting can be scheduled after a certain period of inactivity.
When I described the additional components of the TrustPort suite to a colleague prior to my testing, he suggested that it sounded like something that would be useful for spooks and spies. This component would certainly seem ideal for those FBI agents, and other representative of law enforcement institutions, who seem so prone to leaving their confidential data-laden laptops in taxis, in the seat pockets of aircraft and on other forms of public transport; there is even the option to set a hotkey to unmount all volumes instantly, for use when that mysterious red dot begins tracking its way across the wall towards you.
Like the shredder, all controls were available from the central configuration tool; the only slightly frustrating aspect of the controls was that the ‘Image editor’ section browse button did not default initially to the directory where I had been prompted to deposit my initial image. This seems to be a minor issue across several of the products, with the browse start point often placed rather randomly.
The final component of the suite is eSign, an implementation of PKI for data encryption, signing and so on. Configuration options in the main GUI include options to add oneself, one’s ‘Supervizor’, and a list of other recipients automatically to all encrypted files, and a selection of algorithms and methods for signing and encrypting your data.
Other functions are available via two further interfaces, a key management GUI and a wizard with options for signing and encrypting data; the second set of tools are available in Explorer context menus, to encrypt or sign selected files. Such a tool is certainly useful for secure communications and authentication of data and messages. Much of the functionality is available in the already-popular PGP/GPG system, one which does not rely on both users running specific proprietary software, and to my mind it would have made more sense to have used the OpenPGP standard, or at least to have provided the option to manage keys and encrypt data to this standard; however, I suppose that a closed system like this adds yet another layer of safety around one’s data.
TrustPort’s claims to be ‘the ultimate security solution’ are far from groundless. There’s a lot here, far beyond the in-depth protection offered by four separate malware detection engines. These, of course, benefit not just from the spread of labs to ensure the latest items are identified and added to databases, but also using a range of sophisticated heuristic methods to catch some new items without specific definitions. While these themselves operate in a solid and efficient manner, producing some decent speed times for such a product, the addition of the extra functions provides several further layers of security.
I encountered a few minor problems in the course of my testing, mostly issues of usability, and many of them perhaps only really issues for someone in my rather unique position; few people are interested in running numerous local scans with minor changes to the settings. However, there is certainly room for a little more integration between some of the modules, and a central logging and log-viewing area would be a good place to start. Of the more technical issues, the lack of a ‘reboot required’ method after install on some platforms, and the misleading ‘Update successful’ message, both stand out as particularly serious; both could lead a user into falsely believing they were safe from viruses – a dangerous situation to be in. The lack of integrated scheduled scanning is also a pretty significant failing; although a command-line interface is included to allow such scanning, a small addition to the interface would be a simple, but valuable improvement.
On the whole, however, I found TrustPort an interesting and generally well-designed set of products, and was most impressed by the integration of the multiple engines without an enormous impact on system resources. While its in-depth, multi-layered approach may not be necessary for many users, particularly those running older or less powerful hardware for whom the added overhead may be too much, the TrustPort suite provides a strong set of utilities useful to anyone for whom security and authenticity, of both systems and data are important concerns. With a little more development to wrinkle out a few issues, TrustPort could well become a very strong specialist player in the security marketplace.
Supported platforms: The TrustPort Workstation suite runs on Windows NT, 2000 and XP; when submitted for review, only the anti-virus component supported Windows Vista, but support has since been added for the eSign and Disk Protection components; a Vista-ready version of the DataShredder module is expected soon. The eSign and DataShredder modules also support Windows 9x and ME.
Tests were variously run on: Intel Pentium 4, 1.6 GHz, 512MB RAM, dual 20GB hard disks, running Windows 2000 Professional SP4 and Windows XP SP2; AMD K6, 300 MHz, 256MB RAM, dual 10GB hard disks, running Windows 2000 Professional SP4; and Intel Celeron laptop, 256MB RAM, 10GB hard disk, running Windows XP SP2.
All speed tests were run on: AMD Athlon64 3800+ dual core, 1024MB RAM, dual 40GB and 200GB hard disks, running Windows Vista Business Edition.