2007-05-01
Abstract
Nirbot gains its notoriety primarily from the cat fight in which its author has been engaged. Although keenly aware of the descriptions and blog entries posted about his creations, the author seems not to be so well versed on the naming conventions used within the AV industry. Lysa Myers shares the details of this technologically unremarkable, yet reasonably successful bot.
Copyright © 2007 Virus Bulletin
There has been a considerable amount of discussion in the news recently about a new bot family which refers to itself as ‘IrnBot’. By all accounts, this is a relatively unremarkable bot technologically. It is less functional than your average Sdbot variant, and it utilizes fewer different exploits to get onto machines. And yet, it would appear that this tactic has been reasonably successful. New functionality has been added over time, but the bot has kept things relatively simple.
This bot gains its notoriety primarily from the cat fight in which the author has been engaged. The author seems to be keenly aware of the descriptions and blog entries posted about his creations, but not so well versed on the naming conventions used within the AV industry. The names chosen by the various AV vendors seem to have stuck in his craw, and since they have not been ‘corrected’, he has been picking fights. This has taken the form of comments within the bots, his choice of IRC server names, and his choice of vulnerabilities to exploit.
The first variants of Nirbot were backdoor trojans rather than worms, and were simplistic even by IRC backdoor standards. When executed, they copied themselves to the Windows System directory and created a registry entry in the ‘Run’ key. The trojan would then contact an IRC server to join a predefined chat room. It could then be instructed to do things such as carrying out DDoS attacks, adding and deleting files, downloading files, capturing keystrokes, and uninstalling itself. The chat room and IRC server names at this point were random, or at least nothing that would arouse much suspicion.
From there, functionality was added to disable a list of process names so that detecting the trojan’s presence would be marginally more difficult. Then, mirroring the history of Sdbot, scan commands and lists of usernames and passwords were added so that it could copy itself to open or weakly protected shares. At this point, the author seemed to turn his focus on vulnerabilities, adding the Windows SQL Weak Password vulnerability (MS00-035), Microsoft Windows Server Service Buffer Overflow (MS06-040), and the Symantec Client Security and Symantec AntiVirus Elevation of Privilege vulnerability (SYM06-010).
After increasing the bots’ spreading capabilities, functionality regained the author’s focus. The bots were made capable of sending spam, launching TFTP and HTTP servers and proxies, as well as stealing CD keys for popular programs such as Windows. He also added functionality to thwart debuggers so that getting memory dumps would be more difficult. Later variants were tied to other malware such as W32/SpotFace, which gave them the capability to spread through IM.
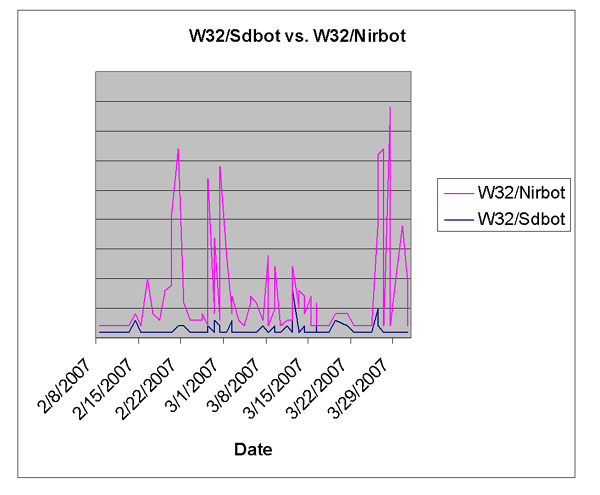
The choice of the Symantec AV vulnerability is what truly set this bot family apart. This gives it a potentially different set of machines to infect – people who have AV software installed, and who perhaps have a habit of patching their machines at least semi-regularly. Sdbots and their derivatives have an ever-dwindling number of infectable machines at this point, as they’ve been using much the same vulnerabilities for some months. Nirbot is not trying to encroach much on that territory. By focusing on machines with Windows Server, SQL, or Norton AV, Nirbot is going after a smaller subset of machines to begin with. Most of the machines that would be infected through these vulnerabilities will be enterprise machines which should, in theory, have better overall protection.
There is some speculation that the spike in botnets seen in March on ShadowServer’s yearly charts is due to Nirbot’s activity [1]. It has provided something of a revival in botnet activity, since the traditional bots such as Sdbot are no longer generating the flood of activity they have in the past.
That being the case, it is clear that people are not patching all their software, regardless of whether they patch Windows.
This is not the first time a virus author has been displeased with the AV industry’s choice of names, nor is it the first time that such a complaint gained them more media attention. In 2001, comments in later Nimda variants indicated that the author was displeased with the AV industry’s choice to ignore his choice of name – Concept [2].
From the first variants, the Nirbot author has included comments apparently intended for AV researchers. Their progression shows us that this author is one who keeps close tabs on blogs and media coverage of his creations, as well as monitoring detection by the various AV vendors. He seems to share the same misconception as the Nimda author about how viruses are named. Clearly, he either hasn’t been keeping tabs on any creations aside from his own, or else he’s new to the game.
The first comments to appear were quite friendly in tone:
Dear Antivirus Employee: I see you have found one of my creations. If you must make a definition please call it IrnBot. Lots of Love, Author of IrnBot ATTN ANTIVIRUS EMPLOYEE: If you’re going to name my very nicely coded modular bot, at least give it the proper name of “IrnBot”. Lots of love, Author of IrnBot Dear antivirus employee: well it’s been an interesting week, it’s been a good battle. P.S. The name is IrnBot, make corrections now please.
By the beginning of the third week in February it was clear that the author was keeping tabs on the detection of his creations, and that he was not happy with what he saw. He had quickly progressed from a very friendly tone, to pleading, to being downright vitriolic:
Hello antivirus employee, I must protest your virus naming system, it isn’t very accurate. I as a malware author believe that I deserve the right to at least have my creations named properly; like come on, I’m the one who keeps your ass in business. Anyways this isn’t “RinBot”, “VanBot” or “NirBot”; the correct name is “IrnBot”. Thank you Panda Antivirus for getting this correct. For the rest of you, I hope you read this and make the correction, or ELSE.
As people within the security industry started trying to shut down his botnets, the author started taking the attention quite personally. He threatened DDoS attacks against the SANS website and started using IRC servers named to insult both Symantec and SANS. Stephen Doherty was the author of the first Nirbot/Rinbot description for Symantec, which seems to have earned him a special place in the malware-author’s heart.
You better f*** off SANS.org especially that Johannes Ullrich (jullrich@***, ***-***-****) and Kevin Hong (khong@***.**, +**-*-**-***). I really don’t have anything against you, just p*** off alright? Dear Antivirus Employee: It’s been a rough week here at base camp, but we will prevail. Lots of love, author of IrnBot. P.S. F*** off Symantec. Sorry about the hospital computers :( ; Dear Symantec: For years I have longed for just one thing, to make malware with just the right sting, you detected my creation and got my domains killed, but I will not stop, I can rebuild. P.S. F*** you a**holes, especially Stephen Doherty who is the biggest f***** I know of.
The comment about the hospital seems to pertain to a particularly disruptive Nirbot infection in the Quebec health care system in mid-February which effectively knocked out its network for three days. Some hospitals had switched to VoIP phones, which were also knocked offline [3].
On 1 March 2007, CNN was infected with one of the Nirbot variants [4]. Later that week, comments appeared that were a mock interview between the malware author and CNN. They make it clear that the author has a rather distorted view of what fraud entails, and the effect his creations have on computers and networks. He implies it’s only affecting old or ignored machines, and actually doing them a service by removing other malware:
Tonight on CNN: An interview with the author(s) of Rinbot. Who are you? Hacker(s). Are you actually disgruntled? No. Then why are you actively going after Symantec? The worm is designed for getting the highest yield of computers infected, not to aggravate Symantec; there is no hate. So why attack the Symantec anti-virus program? A lot of businesses and universities run the application, making it a prime target for exploitation. Are you aware that your worm is crippling computer networks? Yes that can happen on slow networks or networks with many computers; the worm also searches and removes other worms from the system, acting as a small anti-virus program if you will. If you wish not to have those problems keep your software updated. Why did you taunt Symantec and other security companies? They were the first to list the worm on their site and try and get servers shut down. What do you intent to use the infected computers for? Nothing very malicious; no fraud or anything like that. What is the real name of the worm and how did you come up with it? The real name is IrnBot, it is named after a popular soft drink called IrnBru. Thank you for your time author of Rinbot. You are very welcome CNN, thank you for the opportunity to explain.
The soft drink he mentions, Irn-Bru, is a soda that touts itself as ‘Scotland’s other national drink’ [5]. It has been around in one form or another since the early 1890s, and until recently outsold Coca-Cola in Scotland.
A few days after the CNN incident, Offensive Computing posted a neutral discussion of this variant, including the comment above. In response to this, the Nirbot author started giving ‘shout outs’ to them by referencing them in channel names [6].
In what apparently was his last comment, the Nirbot author waxes extra-bilious about a blog posted by Pedro Bueno, discussing the addition of functionality to try to thwart reverse engineering [7]. The author’s choice of IRC server names switches from insulting Symantec and SANS to insulting Bueno directly.
Looks like Pedro Bueno is getting smart at least that’s what he thinks. Apparently he added some new entry to his super-hyper-extra-f*****y lame blog. Which, by the way, does not prevent in ANY way the infection of your computer. Pedro Bueno is gay, gay, gay! (For Richard Simmons, that is. P.S. If you were actually anything other then a complete d***** bag you would realize that it was not intended to stop antivirus researchers, just your everyday script kiddy. Yours truely, Author of IrnBot.
At the time of writing, since the media hype and blogging on the Nirbot family has died down, the author seems to have ceased commenting his creations. Variants continue to be discovered by the handful each day, and show no signs of abating. But it appears, for now, that the cat fight has ended.
This virus is really nothing new in terms of general tactics, though it’s notable how successful it has become with less functionality than the usual crop of Sdbots. It would seem, in terms of both spreading and notoriety, that this virus author has done quite well in targeting AV vendors.
While a policy of not using virus writers’ intended names is laudable, it does little to curb media interest in this sort of story. It is likely that this policy does discourage some script kiddies from trying to gain notoriety, even when it occasionally backfires as in this example.
In terms of the Symantec vulnerability used by this threat, there is not much that can be done aside from continuing to use secure programming practices. It is quite clear from the proliferation of bots using years-old vulnerabilities, that some users are reluctant to apply patches even when they’re offered automatically.