2007-05-01
Abstract
John Hawes shares his experiences with Trend Micro's PC-cillin Internet Security suite.
Copyright © 2007 Virus Bulletin
Founded in California in 1988, Trend Micro is by far the largest security company based outside the US, with its headquarters in Tokyo and its founders hailing from Taiwan. In its home market in Asia Trend holds a comfortable market share, and its global profile continues to expand at the expense of its better-known rivals – its brand recognition having been aided by the company’s successful bid for the Microsoft Hotmail scanning deal in late 2004.
Alongside PC-cillin, which is the company’s flagship home-user product, Trend produces a broad range of security solutions including corporate desktop and server products, gateway software and appliances. Among many innovations supported by the company is the popular HijackThis spyware-spotting system, and the Housecall online scanner has also proved a useful and successful offering. The company maintains a global network of research labs, with several in Asia and Europe and one in the US.
The PC-cillin brand has been around for some time and continues to be applied to the company’s Internet Security suite, while in Japan the same suite is known as Trend Virus Buster Flex 2007.
Trend Micro is the proud owner of the www.antivirus.com domain name, which redirects to the company’s main US site. On visiting the more predictably named www.trendmicro.com the user is redirected to a locale-specific site – although I noted that the remarkably thorough list of countries provided in the ‘Worldwide’ selection does not quite follow through on the (implied) promise of pages tailored to the country/language in question.
The main US homepage is a little slicker than its UK and European counterparts, which seem somewhat pared down and lacking in substance in comparison, and also more closely resembles the Japanese site.
At the bottom of the homepage is a block of floating links to popular keywords. This includes a nod to a few more technical issues, although the site is mostly dominated by more sales and marketing-focused content. The standard datasheets on individual products are provided, as well as advice on selection of the appropriate solution for a given setup. This goes as far as providing a rather fun ‘Solution Recommender’, which gathers details on your environment and presents the dangers and ways of minimising them with plenty of cute graphics and simple terms.
Finding support content is a lot easier here than is often the case on vendor sites, with prominent support links provided in each product section. These lead primarily to a good selection of knowledgebase and FAQ-type solutions to the more common issues associated with the software, with further contact details (phone or email) available for those with more difficult problems.
Delving further into the technical content of the site reveals a comprehensive malware encyclopaedia. This is somewhat tricky to find on some versions of the site, but it has proved regularly to be a useful resource in my own research and features a wealth of detail on many issues. The encyclopaedia often includes in-depth malware removal instructions and in many cases funky graphics and charts to illustrate attack vectors and infection processes for the more complex or common threats. There is also a lab blog, which puts an even more light-hearted spin than usual on the latest issues and discoveries.
Services are becoming a big part of Trend’s online offering, with many of them integrated into the product as part of the TrendSecure system (discussed later on). One function that is freely available to all is the Housecall online scanner. This is an excellent implementation of an online scanning solution, and it suffers from fewer of the browser incompatibilities and less general bugginess than many of its rival services. HijackThis, a registry and settings analysis tool, is also made available free of charge, having recently been acquired by Trend from its original developer who was unable to continue maintaining it without funding.
Installing PC-cillin is a pretty standard operation, although while testing on some older systems I found I had to upgrade my browser to get through the process (the product requires Internet Explorer 5.5 or later, and supports platforms released since Windows 2000 SP4, including 32-bit and 64-bit versions of Vista).
Before any software is installed locally a brief scan is run to ensure the machine is safe, an activation code is required, and options are presented allowing a non-default installation location, and the choice of a normal or minimal installation (minimal in this case apparently being everything except the firewall component).
Permission is also requested to transmit data for inclusion in software and website filtering databases before the installation proper begins. Once complete, a reboot is required and for once the checkbox confirming that rebooting is OK is not checked by default, which is doubtless a bonus for the less attentive user.
At this point some useful information is thoughtfully provided, which is that the main product interface can be launched by double-clicking the blue-and-turquoise pill in the system tray. This is a concept which some other vendors, whose products seem to revel in stealth when it comes to accessing their controls, would do well to consider.
After the reboot, my test lab machines popped up blue warning boxes to inform me that the lack of a web connection left the product unable to update, thus rendering protection less than optimal. A link in the popups led, not as I had expected to the network properties page, or to some stark warnings to fix the problem, or even (as I have seen a few times in the past) to a blank webpage confirming the lack of connection. Instead, some simple, clear advice was provided on investigating the problem, along with some simple solutions.
Connected machines at this point downloaded and applied updates, which were fairly large at around 30 MB, but which came down and installed themselves pretty quickly. With this vital step either completed or avoided, I was ready to look at the product itself.
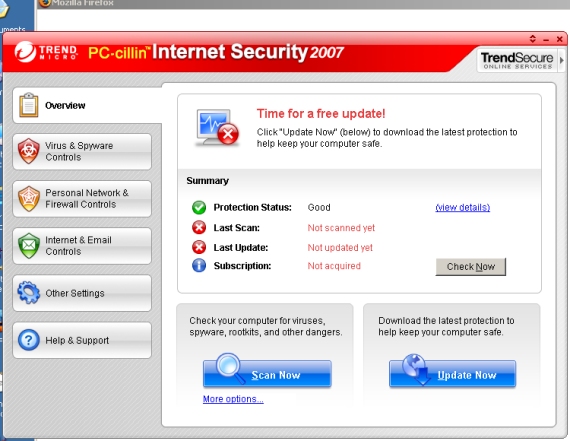
When the pill icon is first clicked on, a tutorial is offered, giving a brief overview of the product. Beyond a list of newly added features for this latest version, the overview was of little interest though, simply running through the available buttons and tabs and explaining what they are used for – most of which can easily be divined from the interface itself.
The interface is clearly and simply laid out, in a style reminiscent of several other such combined suites, which is perhaps an indication that this format is becoming something of a standard – clearly a good sign for users who value consistency in their user experience. There are a few oddities due to the fact that the product design includes an element of the trendy: the real window borders are hidden, which results in an invisible strip along the top blocking some dragging movements (and affecting screenshots).
Buttons are large and colourful, and much of the product features chunky icons which occasionally dwarf the functions they illustrate. On one version of the website a ticking-cog progress display took up much of the browser window while the site processed a request, but the spinning discs used to show progress in the product itself are less intrusive.
The main interface presents a series of tabs down the left-hand side for the major modules, malware controls, network controls, web and email settings, and ‘other settings’ (updates, subscriptions, access to the startup tutorial and logging).
Each section is further subdivided to provide information about and configuration of various aspects of protection, generally with simple on/off controls immediately to hand and more detailed settings windows available for fine-tuning, setting up of block/allow lists and so on.
The layout seems intuitive, although experience with similar products may have biased my view on this. Few of the functions seemed hard to find (with the exception of one item, described in the next section, that is notable by its absence), and few of the controls on offer were hard to fathom. The interface is also fairly responsive, with the occasional pause, accompanied by the spinning circle, as tabs are repopulated with fresh information, but these lags never intrude too much on one’s time.
Should users find themselves at a loss, the ‘Help & Support’ tab is clearly marked on the left, and filled with options to connect to the web for knowledgebase articles or virus descriptions, both discussed earlier.
The local help is copious, clear and pleasing to the eye, with its numerous diagrams and splashes of colour to break up the text. However, it suffers from a lack of context-based access in the main areas of the interface – for help with a particular topic, one must return to the help tab to open the documentation (unless you have figured out how to restore the window border).
Direct links to help on a given section are, however, provided on the more complex settings and configuration dialogs. Tips within the help are rarely, if ever, linked directly to the appropriate tab or subtab required, resulting in lengthy sets of instructions on many pages as a task is walked through from the ‘Open the GUI’ beginning. Nevertheless, the system is nicely laid out and based on tasks rather than buttons, making information on a specific topic simple to find.
When I came to run some scans over various test sets, I was thrown for a moment by the option for selecting an area to scan. At first this appeared only to offer full system scans, however, once I had figured it out I was able to configure it quite simply and run scans across individual folders.
The facility to scan a single file is missing from this part of the interface, and no integration into context menu is provided either, leaving users who find themselves pondering the contents of a newly downloaded or discovered file with a rather more complex process to undergo than strictly necessary. Of course, scheduled scans are also available and can be configured to cover individual files as well as drives and folders.
Scanning results were consistent with recent performances in VB100 comparative reviews, with coverage of the older collections reasonably thorough but a little behind the top performers. On more recent samples there were no such shortcomings, and coverage was excellent. Speeds were good over clean sets, and a little slow over large batches of infected files as detections are alerted on and logged, but this is unlikely to affect the average user unless they are unfortunate enough to acquire infections numbering in the thousands. Trend products have been conspicuous by their absence from the most recent VB100 tests, so gathering speed figures over the new speed sets would offer little value for comparison, and we must hope that an entry in the upcoming Windows XP test will allow scanning rates and overheads to be measured against competitive products.
Options for removal, disinfection or simple logging are generally to hand wherever a scan is set up, along with other aspects of scanning behaviour, such as the filetypes scanned or archive recursion levels (which in some products are tucked away in an obscure corner). Shutting down on-access services is achieved easily with a simple drop-down box on the appropriate tab, and invariably offers the option to restart after a given period of time.
Included on the malware protection tab are controls for the ‘Venus Spy Trap’, which alerts on suspicious changes to the system or software components being installed by untrusted programs. The system can be configured to monitor various areas and types of behaviour, and a whitelist of allowed programs can be set up simply by browsing to the required executable. This proved sufficient to alert on several pieces of malware not covered by definitions in an updated product.
Alongside this tool is a very interesting feature, the ‘suspicious changes’ listing, which offers information on any changes made to the system prior to the installation of the product, from a base level of known-safe or factory default settings. These are divided into areas such as startup items, browser settings, services, installed ActiveX controls and other software and so on. Entries within each section are graded by colour-coded risk level, from the fairly benign to the very serious security risk, and accompanied by copious detail about the change and its associated dangers. Risks deemed undesirable by the user can easily be nullified by the checking of a box and a click of the ‘Undo change’ button – altogether an ingenious, very helpful and wonderfully simple-to-use little item. My only quibble would be the focus on Explorer with no mention of other browsers, which could also present vectors for attack if not configured properly.
The final component in this section is an outbreak warning system, which presumably polls the Trend servers for alerts on major malware events, and ensures that updated protection is downloaded as well as warning the user of such events. Fortunately no major new attacks occurred during the testing period so the impact of these warnings could not be examined.
Of course, as an Internet security suite, there is much more on offer here besides anti-virus and anti-spyware protection. A firewall is perhaps the most basic addition – an increasingly necessary defence tool. As most sensible people upgrading from a plain anti-virus product are likely to have a firewall already in place and tuned to their liking, the option to miss out this component during installation is a useful one. However, the idea of products like this is to keep as much of one’s security controls together in one place and control them with an integrated interface, and here everything is fairly clearly and simply presented.
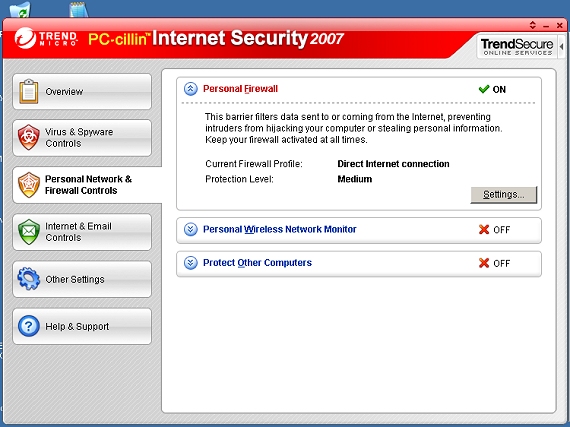
The settings tab on the firewall section opens a dialog listing types of network connection, and showing the basics of the protection profile provided for each. This can then lead to further dialogs which start with simple sliders to illustrate paranoia levels and provide further configuration fine-tuning on other tabs, covering programs allowed to connect outwards and ports open or blocked for inbound traffic, as well as more general networking settings. Explanations of what each section does are put very clearly for the untrained user, and the default settings seem generally pretty solid with no obvious attack vectors left open. Firewall modes can also be changed from the system tray menu, which also offers an emergency network shutdown option.
Alongside the firewall on the ‘Personal Network’ tab is a tool designed to look out for ‘uninvited guests’ intruding on a wireless connection, which can probe on demand or on a schedule to see if the neighbours are stealing your bandwidth. Also in this area is a section for protecting other machines, allowing basic management of Trend installations on other systems in the local network, thus extending the functionality usually provided for corporate network users to the home office and multi-computer homes in general. Details of installed versions can be checked remotely, and if necessary updates can be applied before scans are run to check the remote machine’s security.
The final of the three main security sections concerns the web and email, and opens with an anti-phishing section which seems to be little more than a summary of the rest of the module along with other significant items such as spyware blocking. Spam filtering is provided, but controls are fairly basic, with a simple slider for paranoia settings and no deeper configuration other than lists of approved and blocked senders.
Web filtering has slightly more complex controls, with more allow and block lists which can be set up manually and can be set to allow access to trusted sites only or merely to block the untrusted list. Known phishing sites are alerted on and a further filter allows blocking of sites by content, with a large range of categories from spyware and phishing through sex, drugs and violence down to shopping, gaming and dating. Some playing around with these settings suggested that it worked quite sensibly and thoroughly, although a few gambling sites seemed to slip through the net. A pretty thorough range of browsers and email clients are covered, including the Japanese Becky! System and several major webmail providers.
Finally under this heading is a data-theft protection system, which can be used to prevent items of information from passing outwards from one’s computer. There is a large table of protected items, including credit card numbers, names and email addresses which can be stored for comparison against outgoing data, which is a good idea as long as one trusts that this area is a secure basket in which to store all these eggs. This section ties in with several other online security measures provided by the ‘TrendSecure’ online services offering, which also includes a ‘transaction guard’ tool, a Java applet which provides a ‘secret keyboard’ for entering sensitive data from unprotected systems such as Internet cafes, as well as spyware checking in such locations, but requires administrative access to set up.
Overall this is an excellent product, with the basics covered well and an impressive range of innovative additions, the section for detecting potentially risky software and system changes being of particular note.
Trend has a decent record in VB100 testing, with only one failed test (due to a single in-the-wild miss in December 2006) since 2002, although the product’s frequency of entry is not as good as some. Detection of VB’s zoo sets is generally in the mid-90% range and seems to improve all the time, demonstrating a commitment to adding quality in depth as much as to developing new ideas.
The design of the product is the main thing here though. The majority of home users need a product that can provide them with broad security coverage without excessively taxing technical involvement, and this suite certainly fits the bill with its very clear design and simple layout, and the more complex items explained in well-worded layman’s terms.
More in-depth configuration is generally available for those with a little more knowledge who want to fine-tune things, although the spam filtering settings seemed less flexible than might be expected.
The colourful displays and large chunky icons may be a little much for some, but even these are, in parts, configurable. The only real flaw is the absence of that handy right-click scan, which I’m sure Trend will be adding in at some time in the near future.
Technical details. PC-cillin Internet Security 2007 was tested on: AMD K6, 400Mhz, with 512MB RAM and dual 10GB hard disks, running Microsoft Windows 2000 Professional Service Pack 4. Intel Pentium 4, 1.6Ghz, 512MB RAM, dual 20GB hard drives, 10/100 LAN connection, running Windows XP Professional Service Pack 2. AMD Athlon64, 3800+ dual core, 1GB RAM, 40GB and 200GB hard drives, 10/100 LAN connection, running Windows XP Professional Service Pack 2 (32-bit).