2007-07-01
Abstract
John Hawes takes a detailed look at Avira's home-user internet security setup.
Copyright © 2007 Virus Bulletin
Avira, the company formerly known as H+BEDV Datentechnik, has been in business for over 20 years, and the first product based on its AntiVir engine was released in 1988. Based in Tettnang near Lake Constance, where the borders of Germany, Austria and Switzerland meet, the company has offices and labs in several other regions and partner links in still more, employs around 250 people and boasts over 15 million customers protected by its software.
The AntiVir product range now includes a variety of corporate and home-user offerings, including Linux and Unix products – an area which is something of a speciality for the company; the open-source Dazuko tool, used by many other security products, was designed, and continues to be maintained, by Avira developers.
The company has, for some time, made a basic version of its anti-virus software, AntiVir Personal Edition Classic, available free of charge to home users. A premium version, featuring extra detection capabilities including adware and spyware, is released under licence. Corporate desktop, server and gateway products, firewalls, management tools, and protection for mobile devices complete the set of solutions offered by the company.
The Premium Security Suite is a home-user internet security setup, and includes the full range of AntiVir malware protection, covering multiple vectors, alongside a firewall, spam and phishing filters, and the latest addition, a rootkit scanner.
Avira’s main website, www.avira.com, has an attractively simple home page, with plenty of white space to keep the product information clear and clean, and a smattering of warm red, mostly in the form of the umbrellas that are the company’s motif.
Prominent placing is given to the latest and most significant threats, and information on the latest product updates is also ready to hand. A news section at the bottom of the pages carries stories on the latest significant events in the malware world, and the ‘Company news’ area boasts proudly of Avira’s recent excellent ratings from both AV-Comparatives and AV-Test.org, whose testing placed Avira at the top of the league for detection, heuristics and scanning speed. Avira’s products have a similarly strong performance history in VB100 testing.
The ‘Virus Info’ section is particularly thorough, with a comprehensive and well laid-out encyclopaedia of malware descriptions. As detailed in a presentation at last year’s VB conference, Avira uses a sophisticated, automated description-creation system, which builds the malware description pages in multiple languages as part of the process of analysing and adding detection for new items. The system is improved continually as the amount of data available is expanded. The website also provides a selection of interesting statistical information, presented in graphs and tables, some security news items, a malware glossary and links to the WildList.
The ‘Support’ section carries some standard information on updates and product life cycles (support for Windows 95, 98 and ME platforms is scheduled finally to have come to an end just prior to the publication of this review). A fairly thorough FAQ is provided, covering a broad selection of common issues ranging from where to buy software to the meaning of specific error codes, along with a system for contacting support staff for help. An online form is provided for this purpose, as well as telephone contacts in Germany, Austria and Switzerland. The main focus of the support section for users, however, is an online discussion forum, which seems, if my rather rusty German is any guide, quite a busy place with questions posted regularly and answered pretty rapidly, by both company experts and community-spirited volunteers.
Elsewhere on the site is a wide range of the usual company and product information, with most products and associated updates and patches available to download, protected by a system of licence keys.
The company is the proud owner of the www.freeav.com and www.free-av.com domains, where its freely available home-user product is promoted. The company’s founders also run a charitable organization, the Auerbach Foundation, which receives a percentage of all Avira’s product sales and puts the funds to use in a variety of community projects – more details of their good works are available at www.auerbach-foundation.com.
The product provided for review came in the form of a download, available from the Avira site as either a zip or a self-extractor, measuring around 18 MB. Updates were also provided, some 14 MB of them, in a ‘bundle’ format which the product can be made to absorb into itself, for use in the VB test lab and other offline situations.
The installation process was pretty straightforward, with the only options along the way being a selection of modules to include. After spending some time watching files being extracted, in a window adorned with one of those red umbrellas and the slogan ‘More than security’, there was a EULA, the application of a licence key in the form of a file with a ‘.KEY’ extension, and then the options, which allowed components such as the firewall, rootkit scanner and mail ‘guard’ to be dropped from the install. Not wanting to miss out on any of these treats, I let the installation finish, and was offered a readme, which of course I did not read too thoroughly before allowing the reboot requested in a small blue window behind the text page.
When the machine rebooted, a splash screen showed a picture of a chap clambering around what looked like a complex climbing frame, carrying another one of those red umbrellas. A pop-up told me that my last update took place more than three days ago, and the machine was up and running without undue delay.
Updates did not seem to be initiated automatically, and of course attempting to run the update process in the isolated test lab resulted in disappointed error messages about failing to find the required site.
Moving to a machine with a web connection, I was puzzled to see similar results. Checking the connection, web browsing seemed fine through several browsers, and pinging the address of the update servers was successful too. After some tinkering, I resorted to browsing the forums on the Avira support site (my limited German told me that most queries on this sort of subject were solved with the question ‘Are you running a second firewall?’). I also sent off a support query via the site, but eventually discovered, thanks to more careful perusing of the readme on another install, that running Cygwin in conjunction with the product was known to upset the update process, and also that PGP Desktop 9 may cause users some difficulties.
The manual update process used in the test lab proved much simpler and entirely error free, and the incremental ‘ivdf’ update files are readily available from the website, with a link provided from the home page.
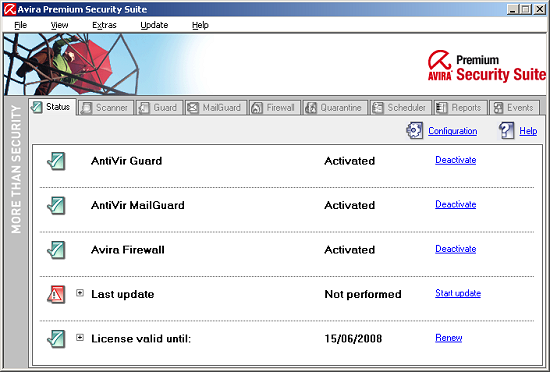
Once the product was running and safely up to date, I was able to take a calm look through the delights offered by the main interface. Once again, this was decorated with the image of the same chap clambering about high in the air with his umbrella, but the control area below was much more straightforward, angular and serious with a lot of white space, small unfrivolous icons and lots of text.
The opening ‘Status’ page showed that all my guard systems, including the firewall, were up and running, that my licence was valid, and also told me whether my updates had been successful. Each section had a ‘deactivate’ link which seemed very responsive, allowing the main modules, on-access protection from malware, mail filtering and firewall, to be switched on and off with ease. There were also links marked ‘Configuration’ and ‘Help’ at the top of the page, which led respectively to a separate configuration interface and a detailed-looking help system.
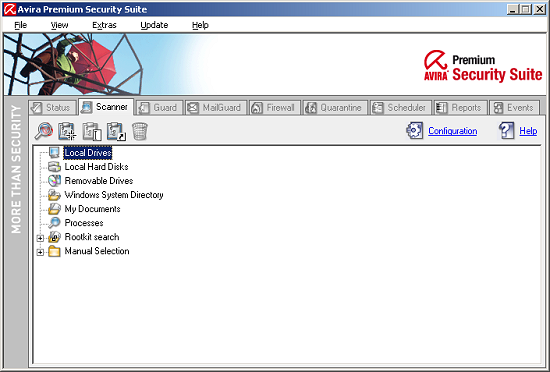
Sticking with the main GUI, a row of tabs led to various aspects of the product. The ‘Scanner’ tab came first, and included a selection of common areas and groups of areas to scan, as well as a nice simple ‘browse’ option to pick out specific files or folders, and a system to design custom ‘profiles’ for repeat scans.
Next came the ‘Guard’ section, with details of what the on-access scanner had been up to, how many files had been scanned, what nasties had been spotted and what had been done with them. A link to ‘virus information’ led to details on particular threats on the company website, but on unconnected systems popped up a jovial window informing me of my lack of internet connectivity, and suggesting I may want to upgrade from the free version to one of the premium products (making the assumption that anyone without an internet connection is likely to be using the free, home-user version of the software).
Moving away from the malware-scanning basics, the ‘MailGuard’ tab showed me the latest emails processed along with some more nice statistics, and offered various options for white- or blacklisting senders, and even switching off spam and malware scanning for certain addresses. The firewall page had a simple slider control, and more data on what was travelling in and out of my machine, along with a list of processes using the network.
The remaining tabs all featured simple, mostly clickable lines of text entries for different subjects. The quarantine page showed all items moved aside out of danger, which could be manipulated in all the expected ways. The ‘Scheduler’ tab included some default jobs, a full system scan, set up for once a day at noon but not active by default, and an update job, which seemed to set itself up for randomly allocated timeslots.
‘Reports’ listed the outcomes of various scans and updates, with details opened up on clicking, and ‘Events’ showed a list of actions and errors, including firewall activity. Oddly, on the system that had failed to apply the offline update successfully, there was no mention of the failure on either of these last two tabs, although failures to run an update from the network were clearly flagged.
Moving on to the configuration interface, at first glance there seems little choice available. For the anti-malware side of things, the file types scanned can be adjusted, the types of access which spark scanning, and the firewall rules and allowed/blocked applications can be changed, but that’s about it. Of course, the little ‘expert mode’ check box makes all the difference, with a far wider range of options opening up when it is ticked.
Pretty much everything seems to be covered here – the malware scanner has all the appropriate controls for actions and alerts on detection, depth and types of archives scanned, exceptions, heuristics levels and reporting.
The mail filter has similar settings for malware plus some further tweaking options for the spam filter, although there is no obvious tuning of the paranoia level here, while the firewall has the usual range of default and user-defined rules, sorted into those relating to individual network adapters and connections, and those associated with specific applications, plus a further page allowing one to disable the Windows Firewall and to lock down the hosts file.
A final section, marked ‘Extras’, provides some controls specific to the suite itself, such as some ‘extended threat categories’ for which detection can be added, and password protection for the controls, an area which offers particularly granular tuning with any part of the interface lockable.
The entire configuration interface features a handy information box in the lower part of each page, which carries a simple description of each option as the mouse hovers over the related controls. In most cases this is pretty informative and phrased in nice, novice-friendly terms, although in a few spots it could offer a little more than the wording on the button in question padded out to fill the space.
All these pages also link to the appropriate entry in the help system, via the Help button or F1, where more detailed information is provided in a reasonably clear and simple fashion, although most of it is laid out in order of the appearance of controls in the interfaces and does little more than explain their function.
A brief FAQ area includes some instructions on performing particular tasks, with most of the questions seeming rather simple, and a section entitled ‘Viruses and more’ contains a glossary of common types of malware, with a useful listing of the ‘extended threat categories’ for which detection can also be enabled.
‘Extended threat categories’ include packed files, files with multiple extensions, jokes, suspicious applications, diallers (apparently a big issue in the German-speaking countries, with much detail provided on their use in Germany, Austria and Switzerland), and also games, with some jovial information added on the economic impact of gaming in the office.
Throughout the Help area, the language shows clear signs of having been translated into English from a rather more formal tongue. Many sentences are long enough to upset the grammar monitors in Microsoft Word and the like and there is the occasional odd bit of syntax – for example, the term ‘action for concerning files’, which pops up quite often in the interface where other, simpler products might merely say ‘action’, is a regular eyebrow-raiser during VB100 testing.
For those requiring more detailed guidance, a full manual is available as a PDF download. The cover is again adorned with photography of those red umbrellas getting out and about, the layout is more task-oriented, and the style and syntax is a lot clearer, although it seems a little flat and unadorned, lacking both illustrations on a larger scale than simple depictions of icons, and internal linking, with a lot of bare, unclickable instructions to ‘see chapter…’.
Beyond these stylistic shortcomings, there is ample information in the various resources for most users to find their way around the deepest intricacies of the product.
Avira has had some excellent scores in recent VB100 tests, with detection across the VB test sets at the very highest level, and its speed results have been similarly impressive. Both on-demand scanning times (over clean files) and the overheads imposed by the on-access component have been among the best in several comparatives – results which, again, have been confirmed by other testing bodies.
Running the product over the latest versions of the VB test sets showed no diminishing of the accuracy and efficiency of the product, or of the development and analysis teams behind it. Using a non-updated product, with virus definitions dating from mid-April, the product still managed some excellent detection of more recently acquired samples, including all but two files from the latest WildList (although that does itself also date from April); with heuristics turned up a notch, from the default ‘medium’ setting to ‘high’, only a tiny handful of items remained undetected.
Those that were still not spotted included a W32/Rbot variant included on the April WildList, but when this tried to connect outward the firewall component did, of course, pop up a dialogue requesting permission. Whether the general user would be sufficiently savvy to know that ‘Services.exe’ is not necessarily a trustworthy item is perhaps a difficult point, but to at least some extent no item of malware tested entirely defied detection in one form or another.
Without the kinds of behavioural and intrusion-based detection gradually coming to the fore these days, the product relies on its advanced heuristics (dubbed ‘AheAD’), which are designed to spot suspicious websites as well as files. This, combined with the efficiency and completeness of its signatures, seems to offer a very solid level of detection, and the product has also come top of the league in independent retrospective testing against unknown samples.
On the ‘general’ tab of the configuration interface a list of extra threat types can be selected. Several of these, such as adware/spyware, diallers, backdoors and phishing attempts, are active by default, but some more, including jokes, games, suspiciously packed files and suspected security risks, can be added for maximum paranoia.
With all these selected, some more items were detected from a stash of hacker tools and other dodgy files, as well as some games. However, I found I could still happily while away my important time with those perennial office favourites, Minesweeper, Freecell etc. (and also Spectrum classic Manic Miner). As far as the built-in Windows games go, it seems likely that the main situation in which such items would be unwanted is in a business environment, and one would hope that any corporate admin charged with ensuring the workforce keep their noses to the grindstone would be more than capable of removing these from desktops anyway.
Rootkit scanning is a fairly new addition to the suite and, as malware grows in sophistication and the ability to remain quietly hidden on a system becomes a more important goal for its creators, it is a feature that is increasingly becoming a prerequisite of this type of product. Rootkit scanning is integrated into the scanning interface, with a simple entry in the list of available scans, and any drive on the system can be targeted. The scan is significantly faster than some of the rival products I have looked at, running through an entire system in only a few minutes. It also seems fairly effective, detecting a selection of hidden items and removing them, with a reboot required to complete cleaning.
Scanning in general was very fast, and system overheads low, with similar figures to those recorded in the recent VB100 comparative (see VB, June 2007, p.10), where AntiVir put in an excellent performance. The interface offers options to adjust the priority of on-demand scanning, with the default set to give way to other processes if necessary.
Beyond the basic detection of malware, the product also offers other security features, including some major modules covering access vectors for malware, system attacks and data leakage, as well as some less conspicuous extras.
Top of the list, and becoming something of a ubiquitous inclusion in such offerings, is the firewall, which features the standard set of controls on incoming connections and local applications sending outbound data.
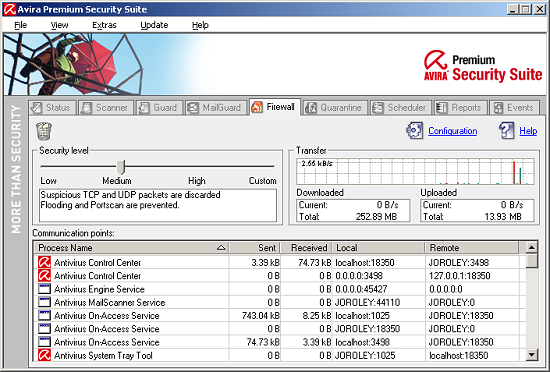
The initial settings seem fairly paranoid, with very little enabled by default. The first few minutes of operating on a normal web-connected machine involved numerous pop-ups requiring permission for a wide range of software wanting to contact outwards, including several involved in firing up some standard browsers and even a couple for other components of the Avira suite.
The pop-ups feature an ‘enlarge’ button, which presents more detail on the individual item requesting permission, which is useful for more technically minded users, especially when the basic pop-up only says ‘System’. For less well-informed users, as mentioned earlier, it seems likely that most such pop-ups will be OK’d without much thought – rather denting the efficacy of such protection – but this is a common problem wherever user understanding is required.
The design of the configuration system is better than many from a home-user perspective, with the often bewildering array of protocols and connection types hidden behind some more novice-friendly sliders and buttons. While this may sacrifice a little of the fine-tuning available in some products, it should cause minimal terror for less proficient users.
The email-filtering side of the software seems similarly simple to operate – a condensed version of the standard malware-handling controls is available, alongside some anti-spam settings. These are minimal in the extreme, with little more than options to switch logging and the use of real-time blacklists on and off, a choice of detail in messages appended to spam subject lines, and a button to purge the ‘training’ data, which is gathered from the user marking messages as false positives or negatives. Phishing attempts are also flagged.
Other extras include a searchable list of the available detection names, though without further information available offline this seems of little use compared to the excellent online databases provided. As mentioned earlier, password protection of the interface options is available at a very granular level.
For what it does, Avira’s suite is an excellent product. It may not be the prettiest product on the market, but where some rivals have invested in slick and shiny interfaces, Avira has focused on thorough coverage of malware and efficiency in the scanning engine, and for most users this is the most important aspect.
A security suite is not something most users expect to be playing with on a regular basis, and this is one that can safely be left to its own devices, shutting out malware without undue effort or system overhead. Defaults are sensible throughout, and a lack of glitter does not make the GUI any less easy to navigate.
While the firewall and spam filters were not given a thorough workout here, they seem perfectly adequate and offer sensible levels of configuration.
If there were any criticisms to be made beyond the mere superficial angle of appearance and presentation, it may be said that there is little here beyond the basics offered by almost all such suites. In the most recent VB100 comparative (see VB, June 2007, p.10), a group of new products came to our attention, introducing innovative ideas into the market with the likes of vulnerability watching and patch management already rolled into the products. Other suites include cryptography and data protection, data recovery, system cleaning and optimization, and the need for advanced IDS/IPS and behavioural detection of malware-like activity is also becoming ever greater.
All of this, of course, can easily be added by combining separate specialist products. For pure anti-malware protection with some of the best records of keeping signatures up to speed and some excellent heuristics, combined with highly impressive scanning times and minimal system overheads, Avira’s Premium Security Suite is pretty hard to beat.
With more functionality being added to its product sets all the time, Avira looks set to grow beyond its current localised focus and to become a very strong global player in the near future.
Technical details. Avira Premium Security Suite supports Windows 2000 and later desktop platforms (including 32-bit Windows Vista), and requires a minimum specification of Pentium-class 133 MHz, with 40MB free hard drive space and 40MB free RAM. It was tested on:
AMD K6, 400Mhz, with 512MB RAM and dual 10GB hard disks, running Microsoft Windows 2000 Professional Service Pack 4.
Intel Pentium 4, 1.6Ghz, 512MB RAM, dual 20GB hard drives, 10/100 LAN connection, running Windows XP Professional SP2.
AMD Athlon64, 3800+ dual core, 1GB RAM, 40GB and 200GB hard drives, 10/100 LAN connection, running Windows XP Professional SP2 (32-bit).