2008-01-01
Abstract
John Hawes discovers how firewall expert Agnitum has fared having added malware detection to its Outpost Security Suite product.
Copyright © 2008 Virus Bulletin
For some time now, VB’s standalone product reviews have tended to focus on the latest offerings from familiar names with long histories in the VB100 tests. This month, however, we look at one of the newest members of the VB100 club, Agnitum Outpost, which achieved its first VB100 award in the last test (see VB, December 2007, p.16) – on only its second attempt. While we have witnessed a recent trend that has seen many AV firms rolling firewalls into their products to build their security suites, this time we see how a firewall expert has fared having added malware detection to its product.
Founded in St. Petersburg in 1999, Agnitum’s launch products were proto-firewall Jammer and anti-trojan system Tauscan. With the release of the first version of Outpost in 2002 the company soon became expert in the firewalls business, with the Outpost name one of the most widely recognized and respected in the field, and licensed for inclusion in a raft of leading security suites. The company’s own Outpost Security Suite, first released in spring 2007 and recently upgraded to a 2008 version, includes the standard selection of security essentials: anti-malware, anti-spam and intrusion prevention, alongside the sophisticated firewall.
The company also provides a standalone version of the firewall – available, like the full suite, on a 30-day free trial basis – and a bigger suite aimed at small businesses providing gateway filtering and client management tools. The firm’s Spam Terrier spam-filtering tool is offered free of charge to all users.
The company’s home on the web, www.agnitum.com, is a clean and simple place, uncluttered by excessive frippery and displayed in a pleasant range of deep blues. The front page features prominent links to the flagship products, the firewall and the suite. Further down the page are links to various news articles, the company blog and signup systems for some monthly newsletters that provide product information and general security advice.
The standard pages of marketing information on the product range are augmented by some more useful technical information, which is often missing from such areas. Details of the latest product versions, file sizes etc. are provided to guide downloaders, and lists of changes in each version are provided for each, as well as the expected overviews of the products and their functionality. Screenshots of various parts of the interfaces and a clear and straightforward pricing guide can also be found here.
Some information about the company, its history, current vision and future plans is provided, along with testimonials from various companies that integrate the Outpost firewall into their own products – an impressive list which includes familiar names such as Lavasoft, Sophos, Novell, BullGuard and Quick Heal (formerly known as CAT Computing). An awards page is similarly well stocked, with recognition from a wide range of magazines and review websites affirming the firewall product’s excellent reputation. The monthly product newsletter, the company blog and numerous press releases discuss the latest additions and updates to the product, with the occasional aside to mention external recognition, the latest and most proudly promoted of which is a 100% rating in Matousec’s recent round of independent firewall leak tests. On a more general note, the company’s ‘Security Teacher’ area carries broader articles, quizzes and cartoons aimed at educating readers about the world of computer security as a whole.
This area is admirably simple, clearly laid out and lacks the marketing doublespeak that so often blights corporate websites. The support area proved similarly pleasant, opening with a set of popular entries in the knowledgebase. One of these was a piece on optimizing firewall performance when running a third-party AV product, with detailed instructions for excluding the Outpost log from on-access scanning in a lengthy list of common scanners. The remainder of the knowledgebase seemed similarly detailed and well written, although its full size was hard to judge as there was no option simply to browse the contents (always fun for the aimless visitor) instead providing only a search option for more purposeful users of the site. Further product support is provided in the ample, and again impressively well-written, documentation downloads, and also in a set of forums. In addition to the official company forum, links are provided to several fan-maintained pages in numerous languages. All of these seem to be bustling both with advice-seekers posting queries and legions of active power-users jostling to assist.
Should a problem prove insurmountable using these various resources, or should a user wish to provide general thoughts or feedback, direct support contact with Agnitum is available both via an online form and via live chat systems. Access is granted to free and trial users, but with priority given to fully paid-up customers.
The final entry in this area is a description of the ‘ImproveNet’ system, a collective updating technique which allows firewall rules created by users to be merged into a central database of known good behaviours, which can then be applied locally to new installations or those still adopting new rules. The idea is to keep popup requests for clearance to a minimum – aiming to reduce the longstanding problem in the firewall sphere where a certain amount of power to control behaviour has to be granted to the user, who often lacks the wisdom or experience to judge for themselves whether a given action is appropriate. Intrigued to see how this system would operate in the real world, I got down to putting the product to the test.
Installation is fairly straightforward, with the standard chain of information, EULA, location selection, and the choice of whether or not to attempt an update during installation before the process gets started – this is pretty smooth and speedy. The installer can detect several other security products, and can even tweak the modules installed to ensure compatibility where possible. The installation process was fairly rapid, though on some slower systems it tended to linger a little during the installation of some Microsoft Visual C++ related software and the core networking components.
Once the basic parts are installed, the user is presented with some choices – to implement standard protection levels or to go for maximum security by tweaking some advanced settings. The standard mode is highlighted by default, accompanied by a warning that some more esoteric leak tests may penetrate the firewall with this setting. Next come some efficiency choices – the option to enable ‘SmartScan’, a technique to speed up scanning times using hidden files caching logs of scanned files, and the on-access scanning settings, which default to scanning all accessed files but can be set to look only at programs being executed.
The final stage presents the option to join a community program sharing settings for known good behaviour, and offers a choice of setup methods, with either a set of standard rules being implemented from the off, or a ‘training’ period during which all activity will be allowed, but monitored and added to the list of trusted behaviour. This second mode is, of course, only recommended for users who are sure their systems are clean and safe, and due to time constraints was not experimented with for the purposes of this review. With all choices made, the final configuration takes place, chugging along for a few moments, and a reboot is required to get things fully activated.
On reboot, the main GUI of the product appears, looking a little unusual. The set of modules listed in the left-hand tab, and row of buttons for scanning, configuration, help etc. along the top are fairly standard, but the main area of the window is taken up with a bright splash of a logo and some blurb about the company’s blog and ‘Security Teacher’ portal, along with links to various parts of the website, including stats and documentation pages. There is none of the usual information regarding the state of the security system, which must instead be checked in detail on the various subpages.
On networked systems in the lab, the LAN was no longer accessible – and on some machines with unusual hardware, the screen resolution had for some reason been set to the lowest possible setting. This was simple to resolve, but showed the first of what was to be many popups requesting permission for a change to the registry. Fixing the LAN issue was a little more complex, and involved visiting the network controls section to find the LAN detection facility, where a few simple tweaks soon had things up and running.
On a simpler standalone home PC no such issue presented itself, and in both cases the systems seemed at first to run fairly unhindered by the new security setup, carrying out a series of standard tasks, opening documents, web browsing, emailing and so on without interruption, although an interesting-looking new sidebar appeared in Internet Explorer. On launching a game the product spots the switch to full screen and offers to move itself into a matching mode, preventing play from being interrupted by any popups, and can be set to default to this action whenever the system goes to full screen.
With the product set up to a basic level, it was time to put it to the test with some more non-standard activity, installing unusual software, foolishly running malicious files and so on.
Agnitum and the Outpost brand have been firmly associated with firewalls for some time. The latest iteration of the product adds numerous improvements to an already strong pedigree, including enough configuration tweaks and defences to attain excellent protection from leaks, as proven in independent tests. Blocking external penetration also seems solid, with the stealth mode fully preventing a system from being detected. Alerting on possible attack can be set anywhere from a minimal level, with only heavy bombardments being flagged for the user’s attention, all the way up to constant, with the user informed of every probe and poke from the network.
Configuration of the product is a somewhat convoluted task, relying heavily on the user to decide the correct settings for themselves – while many products have concentrated on maximum coverage of standard software behaviours, Outpost has a base knowledge and built-in rules for a core set of the most common items, with anything else prompting a query dialog, or more often several. These range quite widely in usefulness – while many recognize a type of action and offer to apply a default rule set for a type of software (such as browsers or chat clients), many more items require rules to be set manually. The process is rendered as simple as possible, but inevitably some understanding of networking terminology is required to ensure the best protection is in place.
To assist the decision process each popup includes some information describing the risks involved in allowing a given action, offering less educated users a valuable chance to learn about the way their system works and the possible dangers they face. With the ‘ImproveNet’ system, this process should become less arduous, as the user community adds more rule sets for a wider range of items.
No matter how solid a firewall is, there are many ways for malware to find its way onto a system, mostly at root due to a user doing something they shouldn’t. To counter this, Agnitum has beefed up its renowned perimeter protection with both standard anti-malware and an intrusion prevention system.
The malware scanning functionality is provided by VirusBuster, whose engine seems to be becoming an ever more popular choice for inclusion in third-party suites. VirusBuster’s own product has been a regular on the VB100 test bench for some time, having made its first appearance in 2000, and having achieved some excellent results in recent years. Detection rates, while not quite at the level achieved by the very best-performing products, have always been pretty good.
Scanning speeds in the recent VB100 tests have been quite impressive for VirusBuster too, and although some hardware compatibility issues meant that Outpost had to be excluded from the speed measurement in the most recent test, the scanning throughput and on-access overhead seems to be at around the same level, with scanning slightly faster and overhead slightly heavier than the parent product. This can be improved upon using an optional system of hidden files logging already checked items, which are then excluded from future scans.
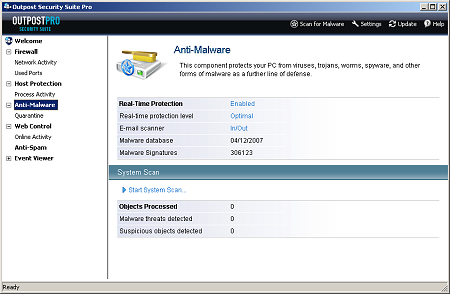
Control and configuration of the malware detection element of the product is very well designed, clear and simple to use – and to my mind, considerably easier than the interface offered by VirusBuster’s own product. Scanning from the interface or the context menu is straightforward to implement, with a fair amount of configuration available for both this and the on-access scanner.
The on-access scanner defaults to checking files on every access attempt, but can also be set to examine files only when fully executed. The default, and apparently only available behaviour of the on-access scanner is to block access to infected files without further action, leaving them in place on the system. It may, therefore, be wise to ensure an occasional scheduled scan is run with the ‘cure’ or ‘remove’ options activated, to ensure no nasties are left lying around waiting to be activated when the suite is switched off.
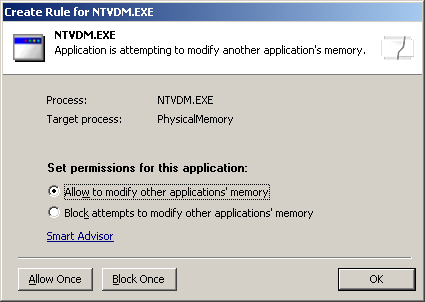
The HIPS system is a little more demanding on the user. This works in conjunction with the firewall, watching the activity of running processes and flagging up any possibly dangerous behaviour, in this case focusing on the local system rather than the network. Despite receiving a shiny new version of the product several days into the month, with only a short space of time in which to run tests, it was not too difficult to find a selection of files not spotted by the anti-virus engine with which to exercise the behavioural blocker.
A series of worms, trojans, adware programs and other nasties were run to observe the actions of the protection system in its default settings, and most seemed to be spotted in some way or another. The registry is closely guarded, and any attempt to add or adjust entries in important areas is blocked. Attempts to open network ports or connect outwards in any way are picked up by the firewall, of course, and processes trying to modify other running processes are also spotted. Installing files into vital system folders is not counted as a bad action, however, and numerous items were able to drop their executables and libraries into the system32 folder or elsewhere.
File infectors also seemed to be allowed a fairly free rein – it would seem sensible to assume that something trolling through folders altering every executable it finds is probably malware, or at least worthy of an alert. With higher security settings, more behaviours are watched for, and at the highest level just about any attempt to run an executable for which explicit rules have not yet been created generates a popup dialog. Even in the default mode, however, just about every piece of unknown malware that was run resulted in some form of detection, even if in some cases it was only at the last line as outbound connections were spotted.
Throughout the last paragraph every reference to detecting or blocking an action in fact means that a popup appeared, offering to allow, block or create rules. Like the firewall, considerable user interaction is required, and likewise at least some level of alertness and understanding is necessary. The default action of the popups is generally to allow, and it seems likely that less switched-on users will end up blindly clicking ‘OK’ without much thought about what might be happening. The alert user, seeing an unexpected action occurring, will be able to investigate further and thus maintain a highly secure system.
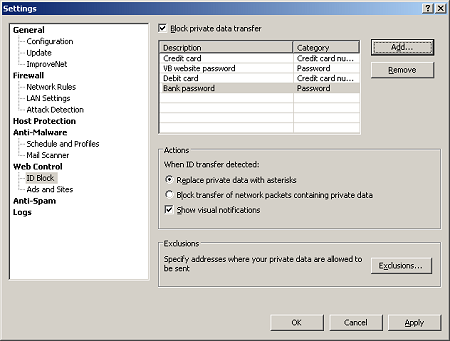
Many of the other tools here are fairly obvious extensions of the overall scheme. Web filtering is provided, with a tool in the configuration interface controlling active content in web pages mirrored by a plug-in for Internet Explorer. While these options are mostly controllable from within the browser, having them more easily accessible is a useful idea; this is combined with advertisement blocking, detecting ads based on common keywords and image sizes, with additional data updated constantly via the ‘ImproveNet’ system.
Also controlled is personal data, which can be entered into a secure database (although canny users will, of course, avoid entering entire passwords or credit card numbers, as entering only parts of them will suffice) and prevented from passing out of the system – the exclusions list manages which sites such data can be sent to, but seems not to link sites to specific data, simply allowing any personal details to travel to any trusted site.
One item which usually does not quite fit in with the overall theme of security suites is the spam filter. Now an obligatory part of any self-respecting suite, spam filtering feels slightly different in its requirements from system security and integrity, and seems to have been added to many products simply to check the box. Agnitum’s offering, also available separately as the freeware Spam Terrier, does at least slot fairly neatly into the style of the rest of the suite with its heavy reliance on user decision-making. With limited in-built abilities, it appears to rely to a large extent on training itself to patterns of mails. A wizard is available to scan current pre-populated mailboxes divided into spam and ham to familiarize the filter with the user’s mailing style, and the usual ‘Mark as spam’ buttons continue the learning process over time. With less than a week to test the entire suite an in-depth analysis of the spam filter’s powers was not possible, but at least it’s there for those who need extra email filtering.
For all of the above items, in-depth guidance and assistance is never far away. A quick-start guide and full manual are available from the support section of the company’s website, both of which are highly detailed and clearly written, providing much vital information for those intrepid but uneducated users embarking on a journey into the frightening world of serious security software. The document covers both instruction on the operation of the product and insight into the issues created or mitigated by certain settings. The firewall section is particularly in-depth, running to some 20 pages.
Help is, of course, also included with the product, and it mostly seems to mirror almost exactly the manual, albeit in a more easily browsable style and with fewer illustrations. The effort that has gone into keeping things as informative on broad topics as possible, while still providing lucid instructions for vital tasks, is even more evident here, where sparse and simple language is more expected. The system could do with being a little more context-sensitive and integrated with the product itself – while the ‘help’ button is accessible from most parts of the interface, it invariably leads to the introduction rather than directly to the page relevant to where the user is. There is no button on the more complex configuration dialogs and there is no linking back out to the right section from within the help pages themselves either.
One final aspect of note is the detailed event viewer, where data on the various areas of the system and network being monitored can be perused at leisure. Various aspects of this can be configured to record more or less of what is noticed, allowing the committed statistic fan to gather vast amounts of information, or minimizing the system impact by keeping things to a minimum.
Agnitum is in the happy position of being a firm that has developed considerable expertise and produced solid and reliable products, yet has not been affected by the booming success which generally sees firms lose drive and focus in the face of strict financial goals. The company’s online information and product design ooze a technical excellence tempered only minimally by marketing meddling, while still providing a respectable level of usability for newcomers. As the ‘Pro’ in the title implies, this is no simple product, but is aimed squarely at those who take an active interest in the security of their systems. It requires its users to exercise their brains and their judgement to ensure a smooth and safe ride, but thanks to some felicities of design, and a large and welcoming community of users, it does allow at least some access to the newcomer.
There is a lot of protection in here, all of it seemingly implemented in a very thorough and reliable manner. The HIPS system does, perhaps, have some small room for extension, and while automation of some of the decision making has been included this could perhaps be carried further across the product. Of course, it could be that the various training modes and the community system already achieve this goal, given a longer period to settle into a given machine. The set-and-forget approach is certainly not immediately in evidence here, and those who are easily annoyed by requests for decisions will most likely find it less than ideal. However, by not dumbing down its approach, and making great efforts to provide the information and understanding required to properly implement a sound security policy, Outpost Security Suite Pro actively encourages its users to take an interest in the threats that face them and how they can be mitigated.
In the right hands, this product offers some powerful system monitoring and provides a very solid, well-integrated and highly effective range of security tools. Those hands do not have to be those of an expert, but they must at least be awake, alert and on the ball, which should really be a requirement for anyone venturing into the precarious world of the Internet.
Agnitum Outpost Security Suite Pro 2008 was variously tested on:
AMD K7, 500MHz, 512MB RAM, running Microsoft Windows XP Professional SP2 and Windows 2000 Professional SP4.
Intel Pentium 4 1.6GHz, 512 MB RAM, running Microsoft Windows XP Professional SP2 and Windows 2000 Professional SP4.
AMD Athlon64 3800+ dual core, 1 GB RAM, running Microsoft Windows XP Professional SP2 (32 bit).
AMD Duron 1GHz laptop, 256 MB RAM, running Microsoft Windows XP Professional SP2.