2008-11-01
Abstract
John Hawes looks at two products from DriveSentry - part of a growing new breed of security products, which focus less on the traditional arts of the anti-malware world, and aim instead to protect systems by preventing unauthorized software from performing any potentially dangerous activity.
Copyright © 2008 Virus Bulletin
This month marks a bit of a departure from the norm, as we look at one of a growing ‘new breed’ of security products, which focuses less on the traditional arts of the anti-malware world, such as detection of malware via signatures, heuristics and behaviour patterns, and aims instead to protect systems by preventing unauthorized software from performing any potentially dangerous activity.
DriveSentry is a fairly young company, set up in 2005, but has managed to generate quite some buzz around its product line. This has been helped, no doubt, by the company giving away the basic versions of its software and making money on upgrades to slicker, higher-spec editions – an increasingly common practice among security vendors. The product range is pretty basic, with the DriveSentry technology available as either a standard desktop product or as a special version designed to protect the growing range of removal and portable storage devices on the market. I took a quick look at both tools to see how they fared in the VB test lab.
DriveSentry’s website (www.drivesentry.com) is a pretty groovy place, presenting a cool black background with lots of funky graphics and animation. The home page heavily promotes the company’s flagship products, proclaiming them to be ‘next-generation anti-virus’, with a graphic showing various types of drives and storage devices being protected by a nimble line of defence. Fat shiny buttons provide access to product downloads, feedback areas and a recommendation system, encouraging users who have been impressed by the product to pass it on to their friends. Much of the site, and indeed the products, takes a similarly ‘Web 2.0’-approach, with lots of user-generated content and interactivity.
Various help and support buttons seem only to lead to a range of nifty little videos guiding users through the various steps of installation and setup, with screen recordings slowly following the prescribed path through the product to perform various tasks. The company’s logo, a heavily armed, red-jacketed guardsman standing watch over an open hard drive, adorns the intros. The videos provide a fairly extensive guide to the operation of the product, in a very simple, unwordy manner that would be accessible to the most uneducated and unskilled computer user, but may be a little slow for those with a short attention span. More detailed assistance is provided via a forum, traffic on which currently seems to be mostly company-generated, but which clearly has a select core of regulars posting both problems and advice to other users. Responses from company reps are refreshingly open, polite and helpful as well as prompt. There are also fairly well-stocked threads about the products on the Wilders Security forum and others elsewhere, again with good input from the company.
For users with more urgent problems, DriveSentry also provides an online chat system, which of course merited a brief trial. A contact greeted me almost immediately, and a few deliberately vague queries about some issues with the product were answered in a similarly prompt, friendly and helpful manner.
The website also provides some more in-depth information on the product and its sales model. The desktop version is provided free of charge, but with a one-off licensing fee payable for continued access to automated ‘tricklefeed’ updating after the first month – non-paying users can continue to update manually. The protection system is described as ‘tri-security’, referring to the blacklist of known malware (variously counted on the site as containing ‘over 1 million’, ‘over 1.3 million’, and ‘1,866,852’ unique items) and a whitelist of trusted software (with a much smaller content: fewer than 50,000 items) operating alongside a herd-immunity system which relies on the input of other users to decide whether to trust an item.
Elsewhere the site offers information about the company, a news section featuring both company news and feeds from some major security news sources, and on the home page a scrolling ‘threats’ section promises a range of interesting-looking articles on topics including threat analysis and general security advice. A final adornment to the home page is the Check Mark logo, indicating that the company’s products have achieved Check Mark certified status. Further investigation revealed that the products had managed complete coverage of the January 2008 WildList, which is an impressive feat for such a young and apparently small firm given the range of complex polymorphic viruses in the list.
With this factoid to whet my appetite, I headed into the lab with a freshly downloaded copy of the software, and had a look for myself.
Initial setup of the product is simplicity itself, with a small download of 30 MB or so and an installation process running through the standard pattern of introduction, selection of install location, EULA, file copying and release notes. Once this is complete the product has to download its white- and blacklist data. This takes a little longer (around ten minutes in some cases), and at the first attempt there was a problem after reaching 99% of the download – an issue apparently caused by the remote copy of the database having been updated before copying could complete. This was fixed in the next version of the product, which was available later the same day. With the databases fully stocked, a little tour of the interface was in order. It proved pretty simple to navigate, clear and slick.
The main pages show the range of folders, file types and registry keys being monitored by the software. The file types and registry key settings are pretty exhaustive, with most of the important areas covered, but the default folder list seems a little sparse, limited to the personal documents areas and the folder where the Windows hosts file is kept. All of these lists are simple to modify, with additions and changes to existing settings able to be put in place within a few clicks, but some more advice on the potential impact of such changes might be appropriate in some cases. More savvy users might, for example, want to keep an eye on other areas – such as the system32 folder, a pretty standard location for malware to use. This can be done fairly easily, but should be expected to generate considerably more prompt messages. Further tabs under the same section provide details of the default actions for various items and areas under protection. The default is to ‘prompt’ in most cases, and there is a list of trusted applications installed on the current system, a sensible method which avoids the exhaustive but often unnecessary lists of trusted apps presented by some products with similar functionality – software installed to the system at any time is added to the list as appropriate.
The ‘access’ screen lists the trusted programs again, with some more information on each. Each is accompanied by details of the level of access afforded to the software in question, including the ability to write to disk, to change registry settings, and access to USB storage devices. Here also are the community-rating scores for each program, which seemed to vary wildly from 100% in favour of trusting to utterly against – somewhat surprising for a clean system carrying almost entirely software included as part of a Windows installation.
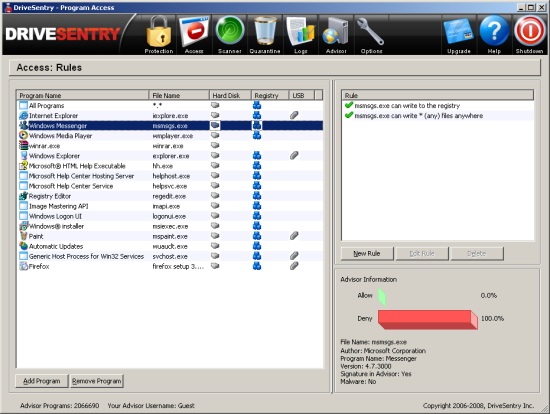
The next few tabs provide the on-demand scanner, along with the quarantine, from where files detected as malicious can easily be restored or deleted, and logging, which provides details of the product’s various monitoring and blocking activities. A tab labelled ‘advisor’ links in with the company’s herd-immunity scheme, and presents some lovely maps of the locations of the users’ connections to the system, along with the latest threats and newly trusted files identified around the world.
An ‘options’ button provides a good range of fine-tuning choices, from the detail level and even colours of the alert/prompt popups, to default behaviours such as automatically allowing whitelisted items. This ‘auto-allow’ function is available only for the first 30 days of use and to paying users (a single, one-off fee) thereafter, but also extends to the community scheme; automatic responses can be further fine-tuned to trust the opinions of the group, both in terms of the percentage trusting or blocking a given item and also the actual number of opinions registered, with a default of 90% of 20 users.
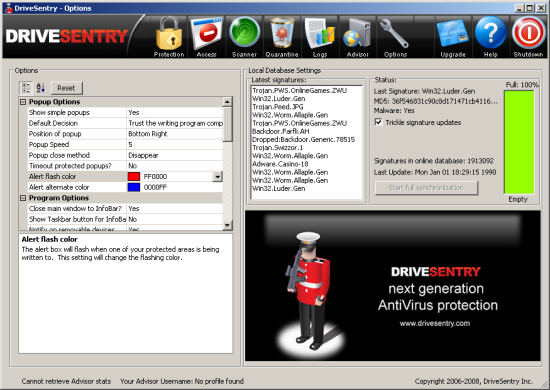
A final set of buttons provide access to the upgrade facility, allowing users to pay for ongoing access to the automated updating and responses to new items. A ‘Help’ button is also provided, which opens a reasonable HTML guide hosted on the company website. The guide covers most of the product’s functionality in simple, clear terms, focusing on a page-by-page run-through of the options available and their purpose. A large shutdown button allows users to minimize the interface, switch off all functionality while remaining active and ready for reactivation, or shut down the product completely.
DriveSentry seems to be in a constant cycle of bug fixing and new builds, and several versions I tried over a few weeks of testing had minor issues. Beyond the update problem mentioned earlier, one version decided it could not access the Internet for the Advisor data, despite having quite happily stocked up its databases just minutes earlier. This meant the machine ran at a snail’s pace as each attempt to perform any action was met with an attempt to retrieve inaccessible data before deeming it permissible. The active community and speedy release cycle means that most issues are fixed within days if not hours, but generally a reinstall seems to be required.
Having familiarized myself thoroughly with the layout of the interface, it was time to have a look at the protection capabilities of the product.
I started off with the simple on-demand scanner. This is fairly clearly laid out, with a list of options for scan types including the default full scan of all drives, a core scan of known sensitive areas, and various other settings including specific files or folders. This was run over a few sets of malicious items, and I was pleasantly surprised with the product’s coverage of the WildList and other sets of recent malware, with the static items, trojans, worms and so on obviously better covered than the more esoteric file-infecting viruses. From the test set used in the most recent VB100 certification review, around 85% of static samples were detected on demand, but less than 1% of file-infecting viruses were detected. On-access scanning was also in place, with the same known malcode detected even when being copied to unmonitored folders by trusted applications. This side of the detection system is clearly based on simple hashing rather than in-depth file analysis, and is thus only capable of detecting files seen by the company’s lab. However, it remains fairly speedy and shows that some sterling work is being done by the lab in both gathering and processing samples. For what is essentially an unexpected extra to what I had assumed would be a straight IDS/whitelisting product, it performed impressively well.
Moving on to some more exacting tests, the system was disconnected from the web for safety and some infectious samples were executed to see how they were handled. Again things were pretty impressive, with the vast majority of malicious items quickly bringing up an alert box asking if disk or registry access should be allowed to an unknown process. This method is not ideal though, automatic blocking of malicious activities always being preferable to putting the onus of decision on the user, but in many cases the mere hindrance to their running caused the more cautious malware to stop running, and most were easily deactivated after clicking the ‘block’ button. In the hands of less cautious or less experienced users, the system may present difficulties, particularly when the popup presents one of the more legitimate-sounding filenames used by some malware, which could easily convince the unwary that some normal everyday activity was going on.
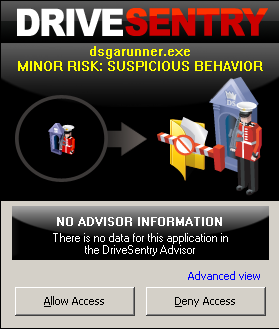
Of course, with such a simple method of protection a few items were bound to slip through – in many instances worms and data-stealers were allowed to perform pretty comprehensive trawls through the system looking for email addresses, passwords etc., performing all their misdeeds without writing to disk and thus without coming to the product’s attention. In a couple of instances more surprising behaviours were discovered, including at one point finding the desktop flipped to what appeared to be the login page of a Brazilian bank, while a nasty fake anti-malware product managed to present a spoof blue-screen, riddled with warnings of malware infection, followed by a mock-up of the XP boot process, advising that some no-name product should be purchased to clean up a dangerously infected system. However, in this case at least the malware was stopped in its tracks before its final stage, as disk writing became involved. Finally, an autorun worm was allowed not only to drop a copy of itself to a USB storage device attached to the system, but also to configure itself to autorun on insertion into a new system.
Moving on to clean items, no false positives were in evidence when the product was run over the VB clean test sets, and installation of a range of software generally presented informative and usable requests for permission to carry out various tasks, always with the option simply to add a new piece of software to the trusted list. However, in many cases there seemed to be a bit of a deficiency in the whitelisting side of things, with items which one would assume would have had pretty decent penetration in a range of user-bases apparently not covered by the central system. In such cases the user is left to rely on his own judgement and that of his fellow users as to whether it is safe to install and trust the applications.
Having learnt a fair amount about the desktop product, it was time to move on to its intriguing little sister, GoAnywhere. This promised complete and portable protection for USB and other types of storage device, along with tiny system impact. The download and setup process was fairly straightforward, with a much smaller file to download and the process of copying to a given device quick and easy. A quick inspection showed that the product is indeed simple in the extreme – essentially a pared-down version of the desktop product, with a small folder of files taking up only a few MB on the target device. The product uses autorun functionality to launch itself, contact the online databases of trust, and monitor for unwanted data attempting to write to the drive.
This immediately rang a few alarm bells, as this kind of autorun mechanism is a clear security risk and something we generally advise people to disable whenever possible, particularly on USB drives as so many worms now use it to spread from system to system. However, in this context it is perhaps a valid technique, as it means that drives can be inserted with a greater degree of security into unsecured machines such as cybercafé systems, which are likely both to have autorun enabled and to be carriers of malware.
Installation highlighted some of the shortcomings in the whitelisting side of the main product, which prompted for opinions on various parts of the GoAnywhere installer and file-copying process. Once up and running, the operation and configuration is fairly straightforward, offering some general system protection as well as that on the removable device. Quite a few popups prompted for choices on connecting to a new machine – no configuration is transferred across, so numerous prompts appear even for processes like Explorer doing its routine actions, and one clumsy mis-click led to it being shut down, which didn’t help the machine much. Lacking a web connection led to some unhappiness too, as the product slowed the system down to a crawl when unable to find its data.
A new set of features including ‘powerful’ (AES 256-bit) drag-and-drop encryption is promised in a forthcoming upgrade to the product. A quick look at a pre-release version of this showed it to be buggy, however, with numerous problems including a failure to launch at all on transferring encrypted data back to the original system, leaving the secured files inaccessible. The system is pleasantly designed though, and should be fairly usable once fully ready for action.
There is a little confusion about exactly what market DriveSentry is aimed at. During the installation process the standard messages about removing any conflicting security software are in evidence, but from personal communication with the company and various postings and discussions on forums it seems that the product is designed to be compatible with more traditional anti-malware solutions, intended as an extra layer of security in addition to, rather than in place of, these more standard products. For this purpose it seems like an ingenious, simple tool with some excellent protection capabilities. There are, as with every product, a few holes which doubtless could be exploited should the user be unlucky enough to be hit by exactly the wrong piece of malware, but this remains a danger with even the most sophisticated and complex security setup.
There are a few areas which could perhaps be beefed up a little, including the products’ whitelists of trusted files. Supporting this effort with a level of community involvement is an interesting concept, one which has been rolled into a variety of products of late, and which does seem to provide some benefits. However, for the more cynical the ‘ask the audience’ approach will inevitably bring to mind the legions of ‘instant security experts’ encountered in the security space, each with a unique and often bizarre slant on security issues and how best to resolve them. Just how far the opinions of the world at large can be trusted is difficult to judge, but the provision of fine-tuning controls does at least allow users to decide how much faith to put in the community’s opinions, and many will simply take account of the majority opinions when making decisions.
This, of course, opens up another can of worms: that of how far users should trust themselves to make decisions about what software to trust. Prompting for permission, where used in operating systems such as Vista’s UAC, has long been criticized as something of a weaselly way out of security obligations, passing the buck onto users who are not generally in the best position to decide what to trust. In software like this it does at least give users exposed to malware an extra chance, with the added backing of the consensus opinions. However, for many, such decisions will invariably be based on convenience and dispatch, and in many cases the default selection will be chosen without much thought or even a glance at the popup.
The best audience for these products doubtless constitutes those who make the effort to learn what they are at risk from, how it might present itself and how to protect against such attacks, and for them DriveSentry represents a great addition to their security arsenal, not a catch-all but certainly a handy extra layer of defence. If the less-in-the-know users could be persuaded to make the effort to learn how to use computers and networks safely, the world would be a much less dangerous place. Outside of Utopia though, this kind of hybrid multi-pronged approach, combining IDS, whitelisting and simple malcode blacklisting with global threat monitoring and self-regulation, may well be a vision of the future.