2010-01-01
Abstract
Version 4 of Alwil's hugely popular avast! has been around for more than six years, and the prospect of a major new release has brought growing levels of excitement and anticipation among the product’s huge legions of fans. The VB lab team got their hands on a late-stage beta of the brand new product - and were very impressed with what they found. John Hawes has the full details.
Copyright © 2010 Virus Bulletin
Alwil’s avast! product has a pretty enormous user base, as evidenced by the company’s recent 100 millionth user celebrations. Its renown and popularity are assisted no end by the free edition which seems to have taken up permanent residence in the top-ten lists of most freeware download sites. Version 4 has been with us for over six years now, and the prospect of a major new release has brought growing levels of excitement and anticipation among the product’s huge legions of fans.
When rumours of a new edition first reached the VB lab in the summer, it went straight to the top of our must-review list, but delays in issuing the final release have dragged on, and with a new release deadline extended to sometime in the new year, we just couldn’t wait any longer. Late beta versions of the product have been made publicly available, so we’ll be taking a quick look at both the free edition and the main Internet Security suite version, which features a number of interesting extras. As both versions are still in beta, we’ll be skimming briefly over any minor bugs observed, on the assumption that these wrinkles will be ironed out by the time the full release is finalized. We will mainly be focusing on the suite edition in this review, but where applicable will note any differences observed between the two.
Alwil is one of the veteran brands in anti-malware, and its products have been regular entrants in our VB100 comparative reviews since official records began in January 1998 (see VB, January 1998, p.10). The company’s first standalone review in these pages was in 1995, when the product included detection for a ‘massive’ 3,103 viruses (see VB, February 1995, p.21). Things have come a long way since then.
The Czech company has been in business since 1991, steadily building up a broad product range around its core desktop anti-malware offering. Solutions for multiple platforms including Mac, Linux and PDAs, consumer and business versions including management systems are all available. Details of the full product range are available on the company website (www.avast.com), and most are offered with a generous 60-day free trial period. One of the most interesting offerings is the BART (Bootable Antivirus and Recovery Tool) CD, which promises a complete bootable environment for comprehensive and secure cleaning and removal – something we’ve not had time to look into properly, but which possibly merits a review of its own. A full online purchasing system is available for most solutions and market segments, with easy access provided to a comprehensive network of local resellers and distributors for bulk corporate orders.
Best known of all the products, of course, is the free home-user version, the users of which must make up the bulk of the 100 million figure boasted of on the company’s website. The current official version of this is pretty similar to the professional editions we have seen in VB100 reviews for the past several years, with its distinctive Winamp-style simplified interface (a more advanced version is provided for those, like us, with more specialist needs), and it seems to have served its users pretty well.
One of the most useful features of the company’s web presence is a bustling support forum (forum.avast.com), where a huge and highly active community of enthusiasts swap tips, help out newbies, discuss new and desired features, and generally revel in their fondness for the product. Most questions, even on obscure and complex issues, seem to be met with a flurry of responses within moments. Company representatives also seem to be pretty active, moderating and providing expert assistance where required.
A more official knowledgebase of standard articles is also provided. This is kept pretty well stocked with answers to common issues, as well as a simple step-by-step troubleshooting process, but the forum is a much richer and more powerful support resource. For more specific or sensitive issues, registered users can also submit full support tickets using an online system.
Elsewhere on the website, a small section of malware information seems somewhat neglected and behind the times (the latest WildList displayed was from early 2008 when we checked), but does include an interesting and highly granular statistics page under the heading ‘Summary of Virus Reports’, which seems to be much more scrupulously maintained.
The final section of the website carries the standard information on the company, news items and awards, press releases on major company events, testimonials from customers around the world, information on partners and affiliates, and of course the now obligatory company blog. Alwil’s blog is perhaps more interesting than many, with the recently installed CEO Vince Steckler frequently posting strident and occasionally controversial opinions on a range of issues surrounding malware and security.
A recent blog post provided links to the beta versions of the new product range, which we keenly downloaded for this review. With ample information on the products within easy reach, it was time to install them and see what they had to offer.
Both products were made available as full downloads with recent updates rolled in. This made for a good start for us, having observed in our most recent comparative that many vendors seem intent on only allowing products to be installed directly from their websites, or in some cases providing product downloads with extremely aged data inside, requiring a lengthy update process once up and running. It seems to us that it is far better, for most purposes, to have a product which can be installed to a state that provides a decent level of protection before venturing online with a new machine – this is exactly what is provided here.
The installation process itself is fairly standard, and in its plain and simple appearance differs little from the process of installing version 4.8 (a very familiar task in the VB lab thanks to its participation in numerous comparatives). The main item of note during the process is the community membership scheme. This is pretty standard in most products these days and allows companies to closely monitor just what is hitting the systems on which their products are installed. This not only allows for interesting statistics to be generated, such as those displayed on the website, but also helps focus the attention of analysts on the types and vectors of attack which really matter. The installation process completes fairly speedily, and for the suite product at least requires a reboot to finalize.
With installation completed, we finally got to feast our eyes on the new-look product. The previous version, as we have commented regularly in the past, had a rather distinctive look which was somewhat past its best. We have often found the layout, even in the advanced mode, somewhat unappealing, confusing and occasionally a little slow to respond, so we had been looking forward to seeing what changes had been wrought. We were not disappointed. A quick straw poll of the lab resulted in a unanimous victory for ‘wow – that looks fantastic’.
The GUI has a very slick, clean, stylish and modern look, with a nice, simple layout. A row of tabs is arranged down the side of the screen in the manner which is becoming something of a standard in quality security solutions. The tabs are split into a sensible selection: a main summary page, an on-demand scanner, settings for the real-time shields, controls for the firewall and anti-spam filter (these last two are absent from the free version), and product maintenance. The summary offers a nice, subtly green bar to indicate that everything is operating properly, the controls for the silent/gaming mode, and a space for additional messages such as warnings about reboots being required.
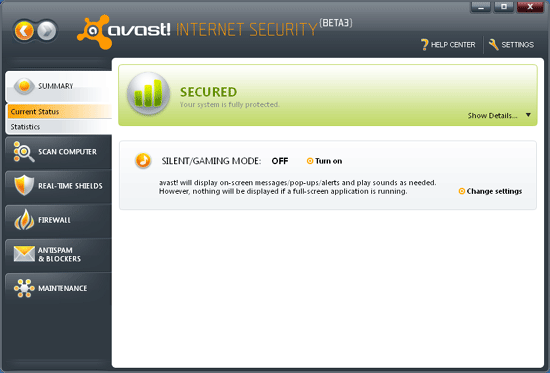
Each of the other sections has a main screen and a series of sub-tabs for controlling and configuring different aspects of the feature under consideration, with most offering a link to ‘expert settings’ for more detailed tuning. A general settings button in the top right leads to a wide selection of additional controls, while a ‘Help Center’ button next to it not only opens the help file, but in most cases picks out the appropriate page for the section the user is currently viewing. A few more such links might be useful in the expert control areas, but in general enough information is provided with each control for users to figure them out with minimal effort.
Overall, the layout is excellent, very simple to navigate, while providing splendid depth and breadth of configuration throughout. We will look a little more deeply at each separate area as we put them through their paces.
Protection against malware attack is, of course, the main function of the product, and avast! approaches this in a number of different ways. First off is the standard on-demand scan. The controls for this offer a selection of standard jobs. A ‘quick scan’, which checks the system memory and system drive and runs fairly speedily, completes in around 10 minutes on a fairly low-powered but well-used netbook. The ‘full scan’ is a little more thorough, while the ‘removable media’ option is designed to check items not usually connected to the system – USB thumb drives for example. There are a few other pre-set areas, such as configuration of scanning from the context menu within Internet Explorer, or scanning while the screensaver is active. The final option is to create a custom scan, which provides a nicely thought out set of stages to design and implement a scan.
Each of these can be adjusted in all manner of ways, including running on a schedule – although, somewhat unusually, no scan is set to run regularly by default. For most users – at least users of always-on desktop systems rather than laptops and netbooks – the on-demand scanner will mainly be used for a once-a-week check-up, probably run in the middle of the night. The fact that Alwil has chosen not to offer a suggested time for this is interesting – perhaps a sign of the growing use of mobile systems and sensible implementation of power saving – but users should probably try to run occasional thorough scans to check for nasties buried in their machines.
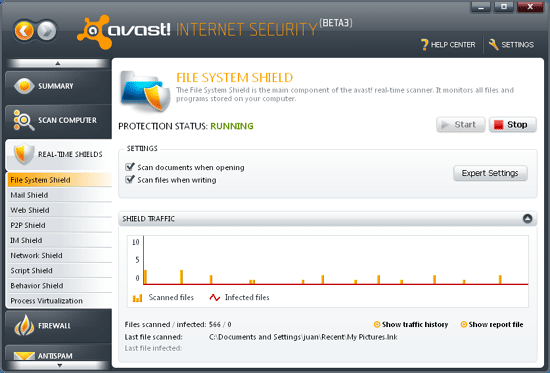
The real-time set-up is much more useful in terms of keeping one’s system safe from penetration in the first place of course, and avast! offers a pretty comprehensive selection of filters watching all conceivable points of access. The standard filesystem scan, usually the main point of contention for those users who find security products upsettingly intrusive, is fairly light on system resources thanks to its avoiding on-read scanning for most file types by default. A more comprehensive selection of file types are only checked when being written to the system in the first place, or when being executed (when the real danger is likely to arise). Most of the settings are fairly sensible, and a huge array of fine tuning is provided for every aspect of the monitoring; one of the more unusual sets of controls in here is the automatic checking of autorun files on removable media and boot sectors on floppy disks – again, a wise decision for ensuring safety.
We exercised both the filesystem shield and the on-demand scanner pretty thoroughly with the full set of tests from the most recent comparative (see VB, December 2009, p.16), and with the benefit of an extra month’s worth of updates a small improvement was shown, even over the already excellent scores achieved by the version 4.8 product. Across all the RAP sets, now several weeks old, very little was left undetected. We compiled a small set of more recent samples, including some gathered after the product had been downloaded, to emulate a RAP test in miniature (testing the product’s reactive and proactive detection abilities). We found similarly strong detection levels, declining somewhat in the most recent and retrospectively gathered items. Overall, detection seems as superb as we have come to expect from Alwil’s products; we look forward to seeing one or both of the products appearing in a full comparative review so that we can provide some more comprehensive detection scores.
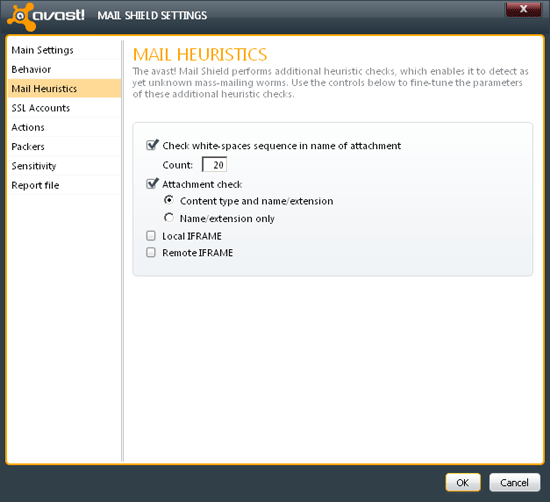
The next set of shields focuses on the main transport vectors through which malware is likely to enter a system: email, web browsing, peer-to-peer and instant messaging. Each is monitored for malcode making its way into or out of the system, with mail transport watched via SMTP, POP and IMAP, and even newsgroup traffic via NNTP. Suspect and infected mails can be marked with a warning (and a label denoting cleanliness can also be added to approved mails), while an interesting additional heuristic watches for large amounts of white space in attachment names – a technique often used to obscure file type identifiers.
The web scanner simply checks files being downloaded during web browsing, while the IM and P2P monitors do the same for various messaging and download tools – both come well stocked with a thorough list of common programs of both types.
Each of these last five shield types comes with an ‘expert settings’ button which provides tweaking options that are unique to the particular activities of the monitor, as well as some standard options. These include default actions when finding an infection (usually moving the item to the ‘chest’), whether or not to scan inside archived or packed files, the sensitivity of the heuristics, and how much data to log to report files.
The final set of shields includes the script, network and behaviour shields. No tuning is provided for these beyond the simple on and off buttons, and indeed very little information is available on what they are up to. They seem fairly self-explanatory though, the first watching for scripts being run (although exactly what constitutes a script is not entirely clear), the second monitoring network traffic for dangerous content, and the third keeping an eye out for suspicious behaviour on the local system – all useful for stopping items not spotted by the standard detection methods. With so little information available on their operation, little testing of these shields was possible, but we did observe that some activities of items not detected by the main shields were being blocked.
All of these features will be familiar to most experienced avast! users, but they have been souped up considerably in terms of the fineness of the controls and, of course, in the attractiveness of their appearance. All the controls are really very well laid out and come with lots of useful comments and explanations to make their functions clear to all but the most unthinking of minds. The final entry in this section, in the suite version at least, is a new one and is intriguingly labelled ‘Process virtualization’; we left this be, planning to look at it in more detail a little later on.
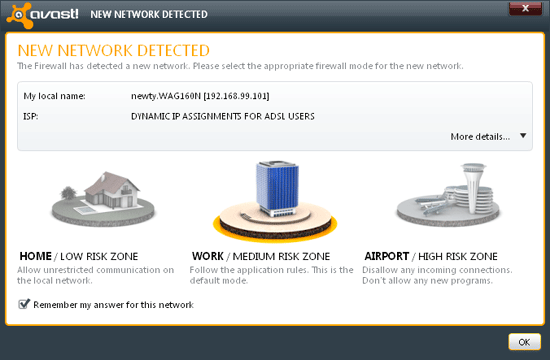
The third main part of the standard protective offerings, available only in the suite version, is a firewall. The initial settings for this are pretty basic: a colourful and attractive slider allows the user to choose from a selection of profiles depending on location. Even the ‘expert’ settings for this section are fairly limited, providing little more than a selection of choices on how to respond to new connections – the default is to decide automatically based on experience, but this can be adjusted to always block, always allow, or always ask the user; some additional options on notifications are also provided, defaulting to only inform the user if a new block rule is set up. This was something of a surprise given our past experience of enormously complicated firewall rule systems.
Looking deeper into the additional tabs, we found a great deal of information provided on network connections established and rules created for specific applications. Just about everything running on the systems we tested on was easily identified and treated appropriately, with Alwil’s massive user base doubtless playing a useful role in ensuring that most commonly used software is recognized and handled safely without interruptions. While the connections page seems to be informative only, the rules page allows the user to adjust the level of trust given to each product and individual executable, using a very nice, simple scale system on a by-profile basis. This rather non-standard approach is innovative and intriguing; it seems to offer a very respectable level of control without the complex and baffling tables and lists which are often relied on for firewall configuration; we thoroughly approved of it.
The final tab of the firewall section is labelled ‘network utilities’, and is another we shall look at in the next section.
Before looking at the selection of interesting and unusual extras, a quick glance over something a little more standard is called for. Anti-spam is pretty much a given these days in a suite product (it is not provided in the free edition). Once again, the configuration is pleasingly simple to use. The main part of the system uses standard spam detection rules, for which little configuration is provided beyond how often they are updated; messages can be tagged with a label if they are believed to be spam, and Outlook users can opt to have them moved to a dedicated junk folder. Addresses to which the user sends mails can be added automatically to a whitelist, which is simple to manage and to add to manually, with a blacklist similarly easy to operate. At some point we hope to be able to add such desktop products to our anti-spam testing set-up when running these reviews, as at the moment we can only provide measurements for server-grade solutions, and no details can be provided on how effective the filtering is.
The second tab of the ‘Antispam and blockers’ section provides a system for blocking access to URLs. Disabled by default, it offers a means of populating a list with web addresses which are then completely blocked. Operating the entry system seemed a little fiddly at first, but as soon as one entry had successfully been made the rest was easy; wildcards are permitted in entries. It proved fully effective in a number of browsers, with just blank pages being displayed when an attempt was made to access the sites in question. It is not entirely clear exactly what the purpose of this is, but presumably it is intended as a sort of rudimentary parental control system.
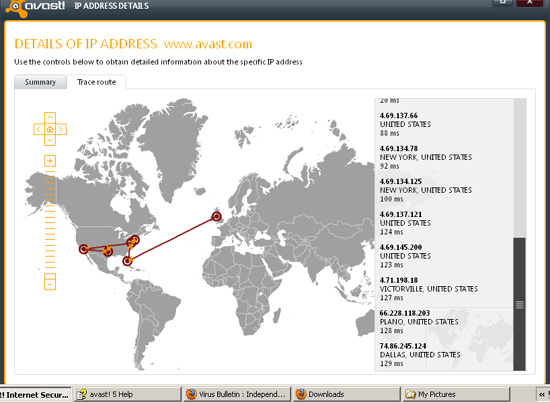
A few other items are worthy of mention, starting with the Network Utilities option found in the firewall section. This offers a system for providing whois and traceroute details, with a pleasing graphic map display looking up a given IP address or domain and providing information about it, including details of all the steps required to reach it. A search for the route between our lab and avast.com led us, via several steps on the US east coast, to Dallas. The same section also includes an option marked ‘fix network stack’, which offers to try to reset the Windows network stack should networking run into problems; the option is clearly marked as potentially dangerous and only to be used in extreme cases.
The final tab on both the suite and free product is a set of maintenance tools, including the usual updater, product information and also giving access to the quarantine system, known to avast! users as the ‘Virus Chest’. In the updater we spotted one of the few bugs still evident in these beta products where, on occasionally demanding an update when it is not required (i.e. shortly after successfully updating), the product acknowledges that no further update is required but then insists that a reboot is required to complete the update. Doubtless this will be fixed by the time the final version is released.
Another area which we were rather disappointed to find unfinished was the intriguing sandboxing system. This offers the ability to run any program in a secure environment, preventing it from making dangerous changes to the system – along similar lines to the popular SandboxIE utility. It is provided as a context menu option, either simply running a given item in a sandbox or setting it up to always run sandboxed in future – all very simple and easy. Unfortunately, one of the main items which one might wish to run in a secure setting, the usual desktop link to Internet Explorer, seemed immune to these menu options, even when an additional shortcut to it was added. Going via the expert settings and browsing all the way to the IE executable proved more effective, and IE could be opened inside the sandbox, indicated by a nice reassuring red border. It seemed pretty thoroughly blocked from making changes to the filesystem. Indeed, it seemed impossible to keep any files created or downloaded during a sandboxed session, which some may see as a little too secure; other similar utilities allow the user to browse the contents of the sandbox and fish out useful and trusted items before flushing it clean. Such functionality seemed absent, but with the documentation (and indeed the product itself) not quite finished, it was difficult to tell.
Other browsers were easier to associate with the sandbox, but were more difficult to persuade to run properly; Firefox simply presented an error message saying it was already running, unless an instance was indeed already running, in which case it would simply open a new, unsandboxed window. Opera, on the other hand, opened in a sandbox, but had much of its content blacked out and was barely usable. This could, of course, be an issue with the specific set-up of the test system, which had some other sandboxing software in place too; a few other systems we looked at had fewer problems, but also fewer browsers. Even during the course of this write-up new beta builds have been released, with many of the issues fixed being in the sandbox area, so I expect that all these little troubles will be removed when the product is deemed ready for full release.
Once again we find ourselves thoroughly impressed with the latest generation of solutions. Alwil’s products have been on something of a wave recently, with a clean sweep of passes in the VB100 testing throughout 2009 and some reliably impressive detection rates. With this new version Alwil finally has an interface and a set of additional features to match its splendid detection. While some rival solutions have offered over-complicated and unfriendly systems, and others have gone for the trust-mother approach and not offered the user any control over their destiny, avast! 5 strikes an excellent balance between simplicity and control, with a very good depth of configuration made available without compromising ease of use. Information is vital here, and the interface designers have done a great job of providing lots of detail on what each section does, and how and why, couched in simple layman’s language to enable all users to get the most out of the product without requiring a computing degree or hours of research.
Of course, being a beta, there are still a few minor hiccups which need fixing, but even with them in place the product outperforms a number of competitor products we’ve struggled with in our tests in recent years. That it manages to look pretty fabulous too is pure gravy; the suite version has some fun and useful extras, and the free version being available to all without charge is nothing short of a miracle. We look forward to seeing the various members of the version 5 range taking part in official VB100 tests in future, as on the evidence of this month’s trials they are very worthy of the VB stamp of approval.
Alwil avast! Internet Security Beta 3 5.0.259 and avast! free edition Beta 3 5.0.259 were variously tested on:
Intel Pentium 4 1.6GHz, 512MB RAM, running Microsoft Windows XP Professional SP2.
AMD Athlon64 3800+ dual core, 1GB RAM, running Microsoft Windows 7 Professional.
Intel Atom 1.6GHz netbook, 256MB RAM, running Microsoft Windows XP Professional SP3.