2010-03-01
Abstract
The VB test team took a closer look at CA's latest product for the home market. John Hawes has the details.
Copyright © 2010 Virus Bulletin
When we first looked at CA’s new product for the home market (in the recent VB100 comparative on Windows 7 – see VB, December 2009, p.16), we were surprised and somewhat baffled by its radical new approach to providing its users with control and information. However, feeling that our first response – based as it was on the brief period spent using the few small areas of the interface required for the VB100 test – might have done the product little justice, it seemed appropriate to give it a second chance.
CA was kind enough to ship over a full boxed version of the product, which enabled us to evaluate the full user experience from store shelf onwards. Taking the funky-looking box into the lab, we put it in a prominent place until we had time to slip the glossy CD into a test machine and look at what was on offer.
Formerly known as Computer Associates, CA is one of the great survivors of the software industry, boasting a length of service and endurance matched by only a few fellow giants. The company went public almost 30 years ago, and existed for many years before that. Between then and now (with 13,000 employees and revenues of over $4.2 billion, according to 2009 figures) it has absorbed an impressive roster of more than 50 other firms; the acquisition of yet another – cloud services firm 3Tera – was announced while putting this review together.
The list of acquisitions includes several firms that have contributed significantly to CA’s security offerings. These include Pest Patrol, which formed the core of the company’s anti-spyware offering and was acquired in 2004. Looking further back we find Cheyenne, an early participant in VB100 comparative reviews, whose Inoculan product evolved into CA’s InoculateIT. The other major string to the company’s anti-malware bow, again appearing as an independent entity in early VB100 reviews, was the VET engine, purchased in 1999, which eventually came to supplant the InoculateIT line after operating alongside it.
More recently, the process of bringing technology and expertise in-house through the acquisition of established firms has been reversed somewhat, with much of the burden of developing CA’s anti-malware components now farmed out to mammoth outsourcing firm HCL. This move has sparked a series of changes in the product range, of which the facelift for the consumer line is the most recent and the most radical.
With such a sizeable company and such a diverse range of products and solutions available (the company’s website lists 10 other high-level product categories alongside its security offerings), www.ca.com is an enormous and multi-faceted place. Initial investigations led only to information on the corporate product range, but eventually a home-user area was turned up in the online shop section. The home-user product line includes simple anti-virus as well as the suite, plus some ‘PC Tune-up’ solutions. Information was provided on all of these, the various functions and modules offered, awards and certifications received, and so on. A link is also provided for potential affiliates, with website owners offered handsome rewards for leading new customers to the CA site. CA itself is affiliated with the Yahoo! web Goliath, its solutions are given away to some Yahoo! users and, by way of return, CA users are offered Yahoo! toolbars – more on which later.
Delving even further into the CA website, we eventually found a less product-oriented security area at http://www.ca.com/us/global-technology-security.aspx. This ‘Global Security Advisor’ section provides all the usual data found on most security company websites: lists of the latest and most prevalent threats, alert meters, malware databases, a sample submission system, a glossary, research papers, articles, news pieces, webcasts, and of course a blog. There is also a forum, which seems fairly well populated but the section titles may be rather obscure to the uninitiated and the bulk of the traffic is clearly focused on enterprise issues.
Full support sections are provided for all the products. For the Internet Security Suite this is accessed via the shop and is hosted at cainternetsecurity.net, which seems to have yet more resources related to the product, including knowledgebases, guides, how-tos and yet more blogging, as well as a system for submitting support tickets. Having found more than enough information and tools, it was time to break the seal on the box and have a look at what was inside.
Breaking into the packaging proved a less simple operation than one might expect; the funky design of the new box avoids the traditional simplicity of rectangles and square corners, instead including a feature corner at a rakish angle to the other parts and a frustratingly difficult process of getting at the CD and licence code inside.
With this achieved (and the box reduced to little more than shreds), installing the product was something of an anti-climax in its straightforwardness, running through all the standard steps, enlivened only by CA’s extremely thorough approach to EULAs. In this case the LGPL (Lesser General Public License) was included, as was an activation process involving both a lengthy product key and the set-up of an online user account. This allows the purchaser of the standard package to install the product on up to three systems simply by associating the installs with the same user account.
With the interactive stage over, the hands-off process of copying files etc. took a fair amount of time and included both a ‘quick scan’ of the target system and a reboot before it declared itself complete. With this done, we were surprised to find it still required an online update, having assumed this would have been part of the initial install and activation. There could have been a minor bug on a few of the test systems, as we noticed some went through several cycles of demanding updates even immediately after an update had completed; perhaps the product was simply being too thorough.
However, all these little niggles were barely noticeable once the new-look interface was up and running. An introductory walkthrough is offered, in the form of an animated, annotated guide, but anyone who’s anything like us will want to start by playing around with the home page. In our previous, rather flippant summary, we described it as resembling the improbable systems used by the character Horatio Caine and his associates in the TV show CSI: Miami, with lots of sliding around of tabs in 3D. Rather than the traditional file-browser-inspired layout with tabs arranged down the left-hand side or along the top, here we have four ‘panels’ covering four major sections of the product, which rotate around when clicked to bring the selected one to the front. Clicking on the panel title opens the full window for that panel, while some main controls can be accessed from the smaller version. The main detail windows for each panel are further subdivided into tabs in a more traditional manner, with simple buttons along the top.
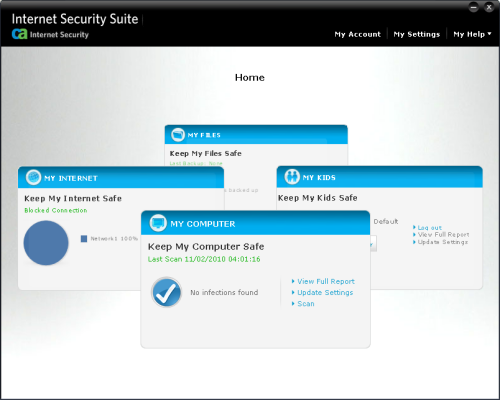
The ‘My Computer’ panel loosely covers the main malware detection functionality. Opening the panel brings up the usual configuration options, including scheduling, which all appear to be present and correct and simple to operate. There are also tabs for ‘reports’ and ‘history’, with history being detailed logging and information along the lines of summary statistics and graphs. The other main panels operate in a similar fashion, with some configuration and some reporting; while focused on a given panel, a row of buttons along the bottom provide access to the other panels and to the funky 3D home screen. Everything is in bright colours, with large buttons, ticks and crosses – presumably designed to be clear and unthreatening but, at least for us, and I suspect for many other experienced users of security software, a little confusing thanks to its considerable departure from the style we have become accustomed to. Perhaps this is a Luddite view however, and more flexible users will find themselves adapting with greater ease to a different way of thinking and working.
Regardless of the response of different user groups to the innovations in layout, it cannot be denied that the provision of the protective elements at the core of the security suite has been considerably simplified here. We have seen many products recently which seem to try to provide an impression of increased protection simply by dividing the components into a large and bewildering selection of separate areas – with malware scanning, real-time protection, anti-spyware, anti-spam, firewalling, HIPS, behavioural monitoring, web filtering and messaging monitoring all treated as standalone layers of protection within a single multifunction suite. Commendably, CA’s redesign has taken the opposite approach. All of these core protective functions are contained within two umbrella sections of the control interface.
The first section is familiarly entitled ‘My Computer’, and includes the functions generally covered by anti-malware products. One of the main links in the initial panel is entitled ‘update settings’, which is perhaps an unfortunate choice of terminology given the association of updating with traditional anti-malware. Most users reading this would assume that the link would lead to the settings for the updating process; however, this is covered in a separate section (reached from a ‘settings’ link displayed prominently at the top of the product, where various global options such as alerting, proxy usage and update scheduling can be managed). The link in the ‘My Computer’ panel is apparently intended to be read not as the settings for the update, but rather as an update to the settings. It leads to the standard set of options, such as enabling on-access and email scanning, scanning different types of files, default responses to detections and scheduling of on-demand scans. The content is fairly standard and the control system pleasantly laid out, with a good level of clarity and a decent degree of fine-tuning made available. The section also provides reporting, including statistical overviews and graphs, and more detailed history of scanning and detection activity.
Having performed numerous tests of CA’s products in our VB100 comparatives in recent years, there seemed to be little further to analyse here; the company has a pretty solid record of certification, generally showing excellent scores in our traditional test sets, but lagging somewhat behind the field since the introduction of the additional trojan and RAP (Reactive And Proactive) test sets, which include a broader range of content and greater degree of freshness. CA has shown keen interest in diagnosing whatever problems may be indicated by this, be they problems with its sample processing procedures or issues with our test methodology which may have introduced some unintended bias. We fully expect to see some solid improvement in CA’s scores in these areas in the near future, representing improvements both in the protection provided by the products and in the accuracy of our testing methods.
Moving along from this fairly standard area, the second top-level panel in the spinning 3D home page contains firewall, anti-spam and intrusion prevention. This is labelled ‘My Internet’, and as in the ‘My Computer’ section provides some top-level links in the mini panel on the home page, in this case leading to reporting, settings (again labelled ‘update settings’), and a simple option to disable the firewall component entirely.
Digging deeper into the full control system for this section, the main screen shows a brief summary of blocked remote access attempts, a drop-down with standard tasks, including again the option to disable the firewall, a lockdown mode blocking all network activity, a purge of caches, and access to the full history log. The most important and detailed part is, of course, the full settings area, which provides access to the reporting system, which can provide fine-grained summaries of the various types of protection offered, and the history, with detailed logging, alongside the configuration controls.
The initial firewall set-up area is pleasantly clear and simple – something that has become ever more important in recent years as users become more aware of the necessity of firewalls but more likely to kick against any attempt to bewilder them with the traditional, port-number and protocol-heavy configuration systems of older types of firewall. Here, users are offered the choice of either a home network with file sharing and full permissions to all trusted applications, or a public network with more secure rules (the lockdown mode appears here too), with some advanced options offering the choice to apply rules to various protocols. Everything is presented in simple language where possible and an effort has clearly been made to make things as accessible as possible to users who lack a deep understanding of networking terminology.
The second tab provides an option for more experienced (or simply braver) users to create their own bespoke network rules, and this area is of necessity considerably more complex. It is laid out in a clear and logical manner however, with as much explanatory text as possible and useful links to more detail in the help system on each page.
Next up is a browser protection component, which by default only provides some basic cookie watching but can be configured to block various types of cookies, and also includes a pop-up blocker and a script blocker. These can be fine tuned to block various kinds of potential risks and can also be set up on a per-domain basis. A schedulable cache cleaner is also included here, once again in a simple and lucid manner, allowing non-expert users a good degree of control without demanding too much research and investigation to make sense of things.
After that comes an identity protection module, which can be filled with various sensitive pieces of information such as credit card numbers or the names of family members, and then prevents the protected data being transferred to websites or via email. Trusted sites can be specified to minimize unwanted interruptions of known-good transactions, and here too everything is nicely laid out with ample explanation provided. Some cursory investigation showed that it was pretty effective at preventing data leaking out.
The final area is labelled ‘Web protection’ and is split into two main components, each of which only has basic controls in the main interface. Most of the controls for these are provided in the browser or mail client, depending on what is appropriate to the specific module. The first part is a spam filter, which works only with Microsoft’s Outlook and Outlook Express; in the main GUI there are only options to enable or disable integration with these, but when one of the clients is opened for the first time after installing the product a brief set-up process points it to existing folders of ham and spam for training, and allows the creation of an address whitelist. A toolbar is then added to the client to allow future tweaking of settings and lists, and also includes a handy search facility. Our current anti-spam testing set-up is designed primarily to measure the efficacy of gateway-level filtering software, but we hope to adapt it to enable some analysis of client-level offerings in the near future; we will return to this product to investigate how well it performs when we can.
Phishing protection is the last part of the product, and again in the main GUI there are only options to enable or disable it and to select which clients it integrates with. The list of supported clients includes various browsers, mail clients and chat tools, the most popular of which are enabled by default with others needing explicit activation; Microsoft Word is a notable inclusion in the additional set, while Google Chrome and Opera are notable for their absence.
Other controls are provided within the protected client; the set-up provides clear information on the safety of links and sites through a system of coloured markings which indicate how much information is available on their legitimacy. The current page is marked in a toolbar, while links can be flagged when hovered over if desired. This second part seemed a little intrusive when set up to always show advice and keep it close to the mouse, but it can be relegated to any area of the screen and can also be set to only show when the control key is held down. It seemed to be fairly speedy in its responses and had a good level of accuracy, quickly identifying major legitimate sites and warning about many less reputable ones.
Of the four main components of the product, the remaining two may be seen as additional functions beyond the narrow scope of malware protection, although of course they remain under the general sphere of security. The first is the ‘My Files’ component – essentially a back-up system. This seems pretty straightforward: various folders and areas can be selected to be backed up and saved to a secure archive, which can either be on the local system or – the recommended option for proper security of back-ups – on an external removable drive. The default is to include the whole of ‘My Documents’, but the browse window to select additional areas is simplified to exclude symbolic areas such as My Documents, so selecting only a subset of the commonly used storage area is rendered a little tricky for most untutored users.
The back-up itself is actually considerably more complicated than a simple archive, creating an executable which includes its own interface for restoring or ‘migrating’ backed up items. One initial test, backing up a folder containing two files of 5KB or so each, took two minutes and created a back-up file of over 40MB. Trying to restore this to a different location had some rather bizarre side effects, including closing down a Windows Explorer instance and, strangest of all, reversing the order of all the task bar icons. Obviously this situation was not an intended application of the tool; the product help was less than plain on the subject of how it is meant to be used, listing the jobs which could be performed but not really explaining the purpose of the complexity introduced, and little time was available for a more thorough investigation. The panel also provides detailed history and reporting on back-ups made and restored.
The fourth top-level panel is entitled ‘My Kids’ and provides some parental controls. Once again, this starts off fairly simply, with the controls for setting up rulesets for individual children. Having entered a name, there is a fairly clear section gathering passwords and existing by-age-group default settings to the new profile. Some nice simple screens then appear for setting allowed or blocked times for Internet use and blocking of types of online content; an advanced section on top of this allows the parent to include specific sites. The final stage allows specific applications to be blocked, in both peer-to-peer and IM categories. These can either be banned outright or on a per-product basis, and for IM behaviour there is an advanced section which can be used to block keywords and even specific contacts.
So far so simple, but we had a little confusion with the implementation of the user system, which seems not to be tied to Windows users but instead is controlled entirely from within the product; the parent sets the rules, then logs the system into a chosen user in the GUI. Having a password set for each user allows an older child with broader privileges to log themselves in to override the stricter settings of younger children, but to control the overall rules the admin or parent user must log back in. A pop-up appears to indicate which user has been switched to.
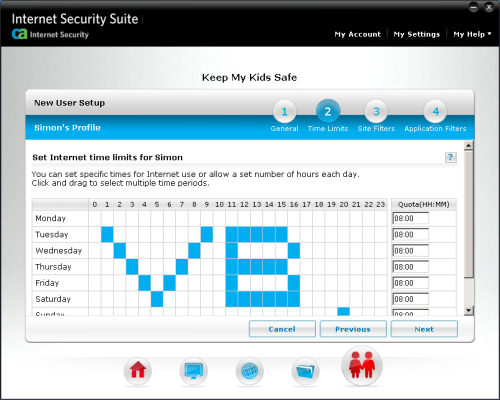
After a little playing around we soon figured out how it operated, and it does seem a sensible option for the average home user, who is unlikely to make proper use of the Windows User subsystem, instead simply leaving the default (usually admin) user logged in pretty much permanently. This is an interesting example of tailoring the user process to real-world usage rather than the ‘proper’ way of doing things. Again, detailed logging and reporting is included, and appears fairly clear and simple to use.
The last item to discuss is the help system, which comes in several forms, all hosted in a slick black interface blending nicely with the main GUI – a standard help file, a set of ‘top solutions’ and a series of instructional videos. The help file follows a by-button path, explaining what each section of the control system relates to, and offers some more detailed explanations than can be gleaned from reading the buttons and so on. However, it provides little by way of holistic explanations of the intent or purpose of a given component. These sections are all properly linked to from within the main interface, with each area providing a link to the matching explanation – something which far too many products fail to implement as thoroughly as is done here.
This more task-oriented approach is covered by the ‘top solutions’ section, which functions in the form of an FAQ and provides detailed steps to carry out a range of tasks and to solve some common problems. Oddly, these open not within the main help interface but in new instances of Internet Explorer (not the default browser of the system but specifically IE). The videos likewise pull up IE and some very slow video rendering from Adobe, which we gave up on after waiting for ten minutes of buffering; most of the clips offered by this 2010 product seemed to refer to IS2009. The help subsystem also includes links to the online community and forums. Overall, the system seems to provide a decent range and level of instructional matter, but suffers somewhat from a lack of joined-up design and logical implementation.
As we observe the ever-growing and ever-evolving range of security products available to computer users through our VB100 comparatives, interface design is something that has increasingly come to our attention as a significant differentiator between solutions. With more and more features included in modern suites, the user is required to spend more time interacting with products which have traditionally aimed for a ‘set and forget’ paradigm. The selection of these additional features can vary fairly widely between products, as each vendor combines different options from the pool of common choices, but most suites combine a core set of elements with possibly a few unusual and even unique extras. In the same way, interface design tends to conform to a basic standard format, with some quirks and oddities in each product; differences tend to be in quality of implementation rather than drastic departures from the accepted norm.
CA, along with its partner HCL, has taken a brave and unusual approach to its product design, and in its efforts to provide a more open and usable experience has had some success. While the set-up may be somewhat confusing at first to those users already well used to existing practices, it does feel that the new workflows presented here would be perfectly usable by those not so set in their ways. The modesty of the product is particularly notable, with the usual flooding of interfaces with separate sections to make a product appear more complete eschewed in favour of simplicity and elegance. The network protection component is a particularly clear example of this.
There is certainly room for improvement in a few areas, particularly as far as we are concerned in the RAP detection scores, but purely in terms of its design and implementation there is much to commend here. We have often noted in these reviews the importance of empowering users to take control of their own security by de-obfuscating the management of security solutions. This product takes an interesting and fairly successful step along the important path towards allowing normal people to understand what risks they take with their computers, and how to keep themselves safe from danger.