2010-07-01
Abstract
Virus Bulletin's lab team take a detailed look at the PC Tools Interenet Security suite and find a solid product, covering the necessary bases thoroughly.
Copyright © 2010 Virus Bulletin
PC Tools has been around in one form or another since 1998, originally operating as WinGuides and providing advice and guidance on various areas of computing, including security. The company adopted its current name in 2004, and picked up a considerable reputation for anti-spyware with its flagship Spyware Doctor product during the anti-spyware boom of the mid-noughties. As it became generally accepted that spyware formed a subset of the general malware threatscape and is best treated with an integrated approach, the company incorporated anti-virus into the Spyware Doctor line, released a standalone anti-virus product and later began offering the full Internet Security suite we’ll be looking at here.
Various versions and iterations of PC Tools’ anti-malware solutions have taken part in VB100 testing since the company’s first appearance in the summer of 2007, including the standalone anti-virus product, Spyware Doctor with integrated anti-virus, and full suite solutions. For several years the products used the ubiquitous VirusBuster engine, and for a while they maintained a decent level of success in our tests, but following the company’s acquisition by Symantec in mid-2008 some clear changes took effect. The product range switched to relying entirely on in-house technology and began to struggle somewhat in our demanding tests. In recent months, however, this period of transition seems to have settled down, with remarkable improvements noted across the board and the products are now outperforming those of their parent company in some areas.
Although broadly focused on security, the company’s product line has remained diverse, with a wide selection of tools including registry clean-up, privacy protection, file recovery and separate firewall and anti-spam solutions among the current stable. The firm also bought in a behavioural monitoring system, ThreatFire, which – like many of the company’s solutions including standalone anti-virus for both Windows and Mac users – is made available free of charge. The suite combines the standard selection of security modules, including ThreatFire, into a single premium package.
PC Tools’ main online presence at www.pctools.com has a clean and simple feel, heavily focused on the company’s impressive product range. Details of the main solutions take up the bulk of the home page, with download links provided for all, and online purchase available for those for which a fee is charged. Additional products are covered in brief further down the page. Awards earned by the company’s products also take pride of place on the main page, and rightly so – a link leads to a page stuffed to the gills with certifications and awards from numerous download sites, magazines and reviewers from around the world. Among this remarkable selection of accolades are, of course, some of the firm’s recent VB100 awards.
The bulk of the main menu on the website is taken up with the product range, providing detailed information, free evaluation copies for just about the entire range, and online purchasing where applicable. The ‘Company’ section provides some background information on the firm, which is based in Australia with offices in several other countries, employs over 250 people around the world and boasts registered users in over 180 countries.
Also included in this section are the standard contact details, news stories, details of partner companies and so on – but most interesting is the ‘Labs’ area, which covers more experimental, cutting-edge and specialist tools and services provided by the firm to support its main product range. These include the ‘Browser Defender’ safe-surfing toolbar, a start-up item scanner, a patch scanner to check for out-of-date applications, the company’s automated sample analysis service ‘Threat Expert’, and a bootable ‘Alternate Operating System Scanner’, to help with the removal of more deeply embedded infections which resist clean-up from within the running system, or which have rendered the system unresponsive.
All of these subsections link to a fairly busy forum area where fans and critics alike discuss the merits of the various offerings and troubleshoot each other’s problems, with much of the assistance on offer apparently provided by expert users rather than company employees.
These forums are just a part of the support available to users of course, and support matters form the remaining top-level section of the website. This provides the standard user guides, FAQs and a rather complicated knowledgebase system, which seems to be an extended FAQ with a troubleshooting flow-through system. For paid-up licence holders, premium support is available with online chat, email and phone-based support.
The ‘user guides’ area contains full HTML manuals for all of the company’s products – as we discovered later, the suite product has only a basic quick-start guide built in, and for more detailed information users are referred to these online manuals. The manual for the suite is pretty thorough and clear, with an approach leaning slightly towards the what-each-button-does style, but with some activity-oriented sections too.
Having exhausted the fairly straightforward offerings of the main website, a few other areas are worth mentioning. The ‘Guides’ section – which does not seem to be clearly linked to from any of the main sections but can be accessed via the company history page – provides an insight into the activities of WinGuides prior to its conversion to PC Tools some years ago. A wide range of tips, tricks and walkthroughs are provided for various areas of Windows adjustment and fine-tuning. These seem to have been left fallow for some time, but still provide some useful information. Also somewhat quiet of late is the ThreatFire team’s blog, which seems to have gone without updates for a few months.
Moving on to look at the product itself, we downloaded the 44MB installer package and ran it on a selection of systems. The set-up process follows a fairly standard path through EULAs, a selection of install locations and so on. A further 78MB of updates were downloaded and a reboot of the system was requested. On restart, a scan of the machine is initiated (more on which later), and once that is complete the interface can finally be accessed. In most cases, our first action on opening the GUI was to apply the licences provided for testing. This proved a somewhat confusing process: clicking the red-highlighted ‘Register’ button opened the company’s web page in a browser at the online purchasing page, leading us to search around the site for somewhere to enter our licence code; it was only after a few minutes’ confusion that we found that, back in the product interface, behind the browser window, the appropriate section had been opened and was ready and waiting for our details. From there on the process went quite smoothly, although it was rather confusing to see the product download a further 11MB of updates (presumably some additional functions available only to paid-up users), and then to demand a second reboot.
With everything fully installed and active, we took a closer look around the interface and control systems. The look and feel of the main GUI is very close to that of the Spyware Doctor, standalone anti-virus and other iterations of the suite which have taken part in numerous VB100 comparatives in the last few years. In our first few encounters with the GUI, we found its layout rather over complicated and lacking in clarity; over time, however, we have learned where the various controls are situated and fine-tuning the various settings has come to feel fairly intuitive – it is not clear to what extent this is due to familiarity as opposed to the minor adjustments and improvements that have been rolled in over the years.
The layout appears initially to conform fairly closely to the current standard layout for such interfaces, with a main home page providing an overview of the major components, their current status and some details of licensing and updating. There is also a handily placed button to initiate a general scan of the system. Such on-demand tasks can be configured more finely from the first of the main sections, also labelled ‘Start Scan’, which provides details of the multiple components of the product’s ‘Intelli-Scan’ system. In addition to the standard static file scanning, various other types of scanning are available, including the checking of registry entries, browser settings and cookies, running processes and those set to auto-start on boot-up, master boot records and much else besides. The standard, default scan covers a wide subset of the most important of these, and on a selection of test systems of varying levels of power and age it rarely took more than ten minutes or so to complete.
Within the scan area little further configuration is provided beyond the choice of which of these scans to include and which areas to check. Further down in the ‘settings’ section, however, some more detailed options are available, providing reasonably thorough coverage of the main fine-tuning controls required by the average user. This includes a community system which reports back on detections to help the developers measure the impact and spread of threats and to monitor the efficacy of detection routines, as well as allowing them to analyse suspicious items in more depth. The system is optional but seems to be enabled by default. A well-organized and simple scheduling system is also provided, allowing multiple jobs of varying configurations to be run as and when required.
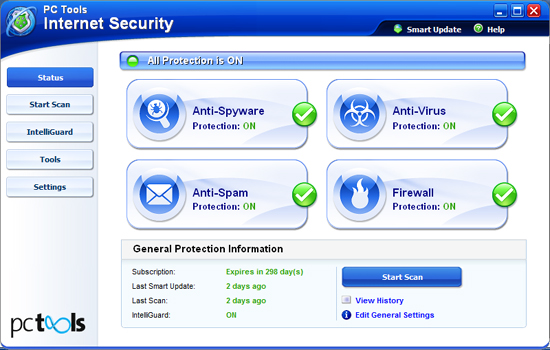
Complementing the Intelli-Scan system, and forming the second major sub-section of the interface, is ‘IntelliGuard’, the on-access component of the solution. Again, this is divided into numerous protection types, watching various areas for potentially dangerous activity. Most of these are fairly clear and self-explanatory, with the browser guard monitoring the browser settings for malicious adjustments, the network guard watching the networking settings, and so on, with the file guard, email guard and site guard similarly straightforward. Some others are less standard and a little less lucidly named – for example the ‘Immuniser Guard’, which actually monitors for ActiveX-based threats. At the top of the list is the most interesting and possibly the most powerful addition to the suite in its latest incarnation, the ‘Behavior Guard’ based on the company’s very highly regarded behavioural monitoring system, ThreatFire.
Each separate ‘guard’ has its own little section explaining its purpose, but there is little individual fine-tuning available for most of them, beyond the option to disable. Each section includes links to History and Exclusions, but these lead to general-purpose areas not specifically associated with the guard in question. Overall, however, the approach is clear and makes a lot of sense, with a lot less unnecessary overlap and self-promotion than in some products which try to make themselves seem thorough simply by splitting standard functions up into meaningless subdivisions.
In the ‘Tools’ section there is only a single entry, entitled ‘Malware Detective’. This appears to run a more thorough diagnostic scan of the system, providing a detailed report designed to be used to diagnose potential problems, particularly if the user suspects their machine is infected with an undetected threat. The scan itself takes only a few minutes with its default settings, and produces a detailed report summarizing the system status, which can then be uploaded automatically to the support department for further analysis.
The final portion of the interface is the main Settings area, which provides some finer controls for the areas already examined, as well as some more general controls. Updating behaviour, detection of ‘potentially unwanted’ items (disabled by default), scheduling, quarantine, excluded files, websites and so on, and event history can all be accessed and controlled from here. The last two subsections are by far the most detailed, providing controls for the anti-spam and firewall set-up, which we will look at in more detail later.
Given the company’s roots in the anti-spyware field, it is only to be expected that it would excel in less traditional malware detection and protection, and we noted early on that the product was picking up on things few others had alerted on. On several of the test systems, the initial post-install scan raised several alerts on what we assumed were clean systems. On reaching the end of the scans and analysing the results, it was clear that most of these alerts were for ‘tracking cookies’ or cookies from suspect websites, which can be considered less of a threat than actual malware; indeed, the company has been criticized in the past for taking a rather alarmist attitude to such things, but as it is part of such products’ raison d’être to pick up on the slightest risk to the privacy of its users, it doesn’t seem inappropriate to identify any suspect item spotted.
As noted in our introductory comments, PC Tools’ products have had something of a rollercoaster ride in our comparative tests in the few years they have been taking part. From a steady start, when the VirusBuster engine formed a major part of the products’ detection capability, detection scores dropped sharply in 2009, after the company was taken over by another major anti-malware specialist and presumably had to stop using third-party technology. After a couple of rather disastrous performances (during which the developers gamely continued to submit the product for testing), improvements came quickly, and detection rates rose rapidly to much more respectable levels. In the last few tests in which they have appeared, PC Tools’ suite and Spyware Doctor products have done very well – perhaps not challenging the very top of the leader board, but sitting respectably at the upper end of the middle of the pack in most of our sets. Their reactive scores in our RAP tests have been particularly impressive, while the proactive rates have been less remarkable.
Of course, the product has numerous additional features to supplement the basic detection measured in our standard comparatives, most notably the behavioural monitoring and other aspects of the IntelliGuard system. The ThreatFire system in particular is designed to prevent infection from items not previously seen by the developers, based on rules of behaviour, and has a very strong reputation in this field. Indeed, in previous experiments with the standalone variant of the system (which remains available as a free download from the developers), we noted some excellent results.
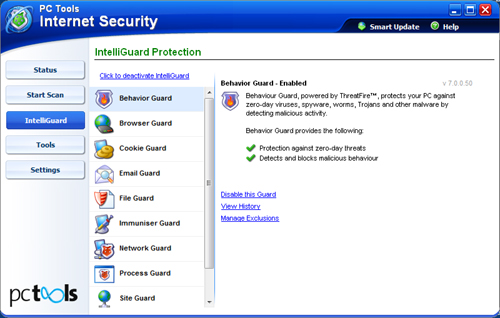
Running some more, fairly unscientific tests, we attempted to access known-malicious sites (mainly through clicking on links contained in spam emails), and found the vast majority were easily protected against even when the resulting executable samples were not detected by the standard scanner. Protection was provided mainly by the heuristics and the behaviour monitor, but on a few occasions by alerts on known-suspect URLs and other threat vector monitors. Each time a threat was detected, a pop-up alerted on the attack and provided options to allow or block the threat, and to automatically perform the same action in future. This appeared only to apply to the specific threat ID, and we would have liked to have seen some options provided to apply actions automatically on a per-type basis – for example blocking all high-level threats (the system marks each threat on a scale of importance), or according to which section of the IntelliGuard list spotted the threat.
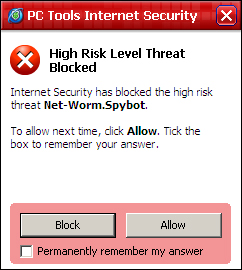
Of course, no product can guarantee 100% protection against all threats, and eventually we were able to find a few malicious links which were able to slip past the penetration-vector monitors, but in just about every case the behavioural system picked up on the activities of some portion of threat and stopped it carrying out its most serious activities. After trying several dozen attacks we didn’t manage to find anything which could completely overcome the multiple layers, and we were highly impressed with the product’s thoroughness.
Beyond these mainstream protective features, there are of course a few additional items required to make a product a full suite rather than just a very thorough anti-malware solution. In this case these are limited to the pretty much obligatory basics: firewalling and anti-spam.
We are not yet in a position to measure the efficacy of desktop-level anti-spam solutions – our anti-spam comparatives currently being geared exclusively toward server-based gateway products – but the configuration system appears fairly well designed and offers a decent level of control over its behaviour. It offers a selection of real-time blacklists, which can be implemented or ignored using a very simple slider system, which applies a more or less aggressive approach to filtering depending on the user’s requirements. Mails can also be blocked by source country in a pretty simple manner. Additional controls are provided for changing the alert threshold for the Bayesian content filtering, message tagging, filtering of attachments by file type, and tweaking the training system to adjust to specific requirements (such as removing preset suspect words and phrases). These are all presented in a very simple, logical and usable manner with some pleasantly clear descriptions and definitions of terminology for the inexpert user.
The firewall system, of course, presents an extra layer of complexity – as such things must – but again some effort has clearly been made to render the fine controls reasonably accessible. The layout is sensible and easy to navigate, and wherever possible some explanations and clarifications are provided. The standard settings consider any new network to be untrusted and implement a good ruleset without impeding normal activities. It is also simple to switch to a more relaxed set of rules for more trusted networks at any time. Overall, it is quite an approachable system, providing ample tweakability for the firewall fetishist without being too complicated for the novice to explore and tweak their set-up.
There are a couple of extra items worth mentioning here, although really they come under categories previously discussed. The anti-spam feature has a toolbar which integrates with the Outlook, Outlook Express and Thunderbird mail clients and provides handy buttons for marking mails as spam or ham, as well as access to some of the configuration options provided in the main interface.
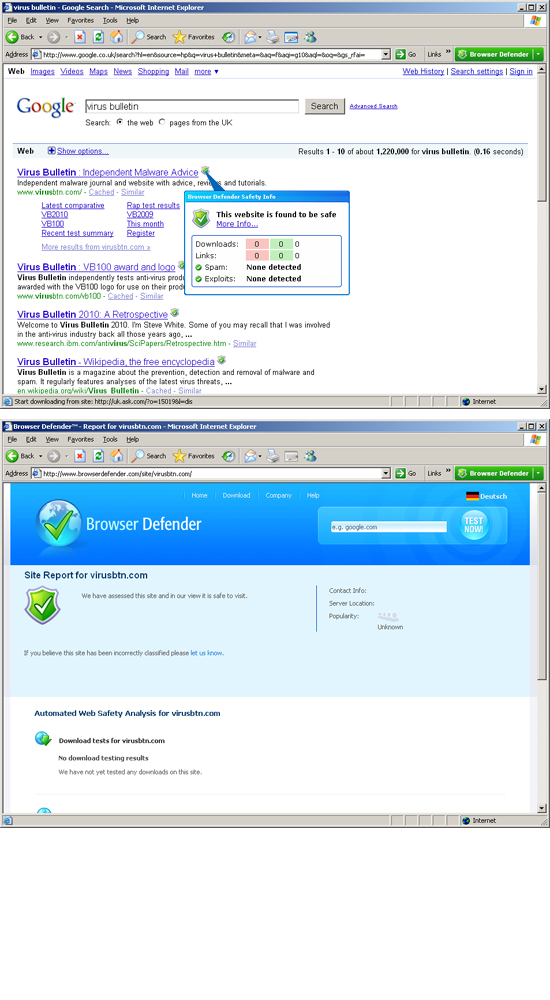
A similar toolbar is provided for Internet Explorer, as part of the Browser Defender system mentioned earlier. This is also available as a standalone product and provides part of the URL blacklisting system. As such, it acts as a supplement to such blacklisting features in some browsers, for example Firefox, and a control system for the manual white- and blacklisting of sites. It proved simple to use and fairly effective, blocking a number of sites as mentioned above, and while the toolbar itself is only available in IE, the blocking seemed just as effective in Firefox, picking up a number of sites not included on Mozilla’s own blacklists. It also provides link checking in search results, marking known-good and known-bad results and providing details of what is known about the site on hovering over an icon.
In the past, the attitude of the VB lab team towards PC Tools’ products has been somewhat ambivalent, thanks to some difficulties in pushing it through our rigorous comparatives in the early days, and some rather unpredictable results over the years. Of late, though, the company has clearly matured into a solid and reliable provider, achieving some thoroughly respectable results in several recent tests and showing no sign of slowing its inexorable improvement. The addition of the ThreatFire component to this solid base makes for a formidable barrier to attack.
Looking more closely at the product itself has answered many of our questions about where it stands in the complexity scale of solutions. Since the acquisition by Symantec, PC Tools has come to be seen by some as at the geekier end of the giant’s offerings, with Norton the mom-and-pop product aimed at the general, inexpert user while the PC Tools range has more appeal to those who are ready to invest some time and energy into their protection scheme. By this measure, the current suite clearly provides a greater degree of fine-tuning than many, but perhaps not quite as much as one would expect from a truly geek-oriented solution. In particular, areas such as the various layers of the IntelliGuard set-up might benefit from some more in-depth fine-tuning options. As they are, they provide a solid and reasonably unobtrusive defence against the vast majority of threats thrown at them, but more advanced users may find themselves digging around in vain for finer controls.
On the other hand, the depth of layering provided is fairly impressive, and in some components (notably the firewall and anti-spam areas) the deep control systems are impressively detailed while also being laid out with enough simplicity to make them accessible to all but the most computer-illiterate user. While we do always encourage users to make the effort to understand the dangers posed by the malware menace, and to educate themselves on how best to protect themselves, it is quite understandable that many would have neither the time nor the basic knowledge required for this, and PC Tools seems to have struck a good balance between providing advanced tools for the expert and set-and-forget simplicity for the novice.
From a company which offers such a wide range of solutions, we were somewhat surprised to find a suite offering little beyond the standard component set, with none of the rare and unusual extras we’ve seen creeping into some similar solutions in recent years – there is no parental control system here, no vulnerability monitoring, no encryption or sandboxing. However, by focusing on those essential basics, and providing solid coverage of every angle expected, PC Tools has put together an impressive suite which does not feel limited, but instead covers the necessary bases thoroughly, and does so simply and efficiently – a good job all round.
PC Tools Internet Security 2010 was variously tested on: AMD Phenom II x2 550, 4 GB RAM, running Microsoft Windows Vista Business Edition
AMD Athlon64 3800+ dual core, 2 GB RAM, running Microsoft Windows XP Professional SP3
Intel Atom N280 1.66 GHz Netbook, 2 GB RAM, running Microsoft Windows 7 Professional