2011-11-01
Abstract
Unauthorized online pharmacies that sell prescription drugs without requiring a prescription have been a fixture of the web for many years. By gathering the top web search results for 218 drug-related Internet queries daily over nine months, Tyler Moore and his colleagues have found evidence of substantial manipulation of web search results to promote unauthorized pharmacies.
Copyright © 2011 Virus Bulletin
Unauthorized online pharmacies that sell prescription drugs without requiring a prescription have been a fixture of the web for many years. Given the questionable legality of these shops’ business models, it is not surprising that most resort to illegal methods for promoting their wares. Most prominently, email spam has relentlessly advertised illicit pharmacies. Researchers have measured the conversion rate of such spam [1], finding it to be surprisingly low. Upon reflection, this makes sense, the unsolicited and untargeted nature of spam. A more successful approach for the pharmacies would be to target users who have expressed an interest in purchasing drugs, such as those searching the web for online pharmacies. The trouble is that dodgy pharmacy websites don’t always garner the highest PageRanks on their own merits, and so some form of black hat search engine optimization (SEO) [2] may be required in order for such sites to appear near the top of web search results.
Indeed, by gathering the top web search results for 218 drug-related queries daily over nine months in 2010–2011, Nektarios Leontiadis, Nicolas Christin and I have found evidence of substantial manipulation of web search results to promote unauthorized pharmacies. In particular, we have found that around one third of the collected search results represented 7,000 infected hosts triggered to redirect to a few hundred pharmacy websites. In the pervasive search-redirection attacks, miscreants compromise high-ranking websites and dynamically redirect traffic to different pharmacies based on the particular search terms issued by the consumer (the full details of the study can be found in [3]).
Figure 1 illustrates the search-redirection attack in action. In response to the query ‘cialis without prescription’, the top eight results include five .edu sites, one .com site with a seemingly unrelated domain name, and two online pharmacies. At first glance, the .edu and one of the .com sites have absolutely nothing to do with the sale of prescription drugs. However, clicking on some of these links, including the top search result framed in Figure 1, takes the visitor not to the requested site, but to an online pharmacy store.
Search-redirection attacks combine several well worn tactics from black hat SEO and web security. First, an attacker identifies high-visibility websites (e.g. at universities) that are vulnerable to code-injection attacks. The attacker injects code onto the server that intercepts all incoming HTTP requests to the compromised page and responds differently based on the type of request:
Requests from search engine crawlers return a mix of the original content, along with links to websites promoted by the attacker and text that makes the website appealing to drug-related queries.
Requests from users arriving from search engines are checked for drug terms in the original search query. If a drug name is found in the search term, then the compromised server redirects the user to a pharmacy site or another intermediary, which then redirects the user to a pharmacy site.
All other requests, including typing the link directly into a browser, return the infected website’s original content.
The net effect is that web users are seamlessly delivered to illicit pharmacies via infected web servers, and the compromise is kept hidden from the affected host’s webmaster in nearly all circumstances.
Upon inspecting search results, we identified 7,000 websites that had been compromised in this manner between April 2010 and February 2011. One quarter of the top ten search results were observed to actively redirect to pharmacies, and another 15% of the top results were for sites that no longer redirected but which had previously been compromised. We also found that legitimate health resources, including authorized pharmacies, were largely crowded out of the top results by search-redirection attacks as well as blog and forum spam promoting fake pharmacies.
One obvious question when measuring the dynamics of attack and defence is how long infections persist. We define the ‘lifetime’ of a source infection as the number of days between the first and last appearance of the domain in the search results while the domain is actively redirecting to pharmacies. We observed the median lifetime of infected websites to be 47 days, but that 16% of the websites remained infected at the end of our study.
We used survival analysis to examine the characteristics of infected websites that could affect the duration of infections. The survival function S(t) measures the probability that the infection’s lifetime is greater than time t. The left-hand graph in Figure 2 plots the survival function estimates for each of the four major TLDs (.com, .org, .edu and .net), plus all others. Survival functions to the right of the primary black survival graph (e.g. .edu) have consistently longer lifetimes, while plots to the left (e.g., other and .net) have consistently shorter lifetimes. The upshot is that websites on the .edu and .org TLDs are infected disproportionately more often and the infections persist far longer than websites on other domains. For example, the median lifetime of .edu infections was 113 days. In contrast, the less popular TLDs taken together have a median lifetime of just 28 days.
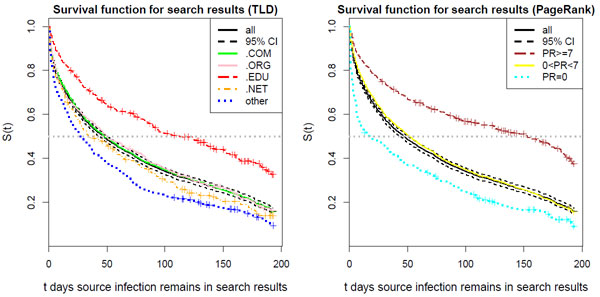
Figure 2. Survival analysis of search-redirection attacks shows that TLD and PageRank influence infection lifetimes.
Another factor is also likely at play: the relative reputation of domains. Web domains with higher PageRank are naturally more likely to appear at the top of search results, and so are more likely to persist in the results. Indeed, we observe this in the graph on the right-hand side of Figure 2. Infected websites with PageRank 7 (out of a possible 9) or higher have a median lifetime of 153 days, compared to just 17 days for infections on websites with PageRank 0. We therefore conclude that high-ranking websites and those present on .edu domains are the most lucrative targets for miscreants.
Using estimates of the popularity of drug-related search terms and the payment processing websites used by the pharmacies, we are able to derive a ball park figure for the conversion rate of between 0.3% and 3.2%. In other words, for every 1,000 web searches for pharmaceuticals, between three and 32 purchases are made via websites infected by search-redirection attacks. Consequently, while email spam promoting pharmacies has attracted more attention, we conclude that the bulk of illegal pharmaceutical sales are likely dominated by referrals from web search. This is not surprising, given that most people find it more natural to turn to their search engine of choice than to their spam folder when shopping online.
For those whose aim is to reduce unauthorized pharmaceutical sales, the implication is clear: more emphasis on combating transactions facilitated by web search is warranted. The existing public-private partnership initiated by the White House [4] has so far focused on areas other than search-redirection attacks. Domain name registrars (led by GoDaddy) can shut down maliciously registered domains, while Google has focused on blocking advertisements (but not necessarily search results) from unauthorized pharmacies. Unfortunately, no single entity speaks for the many webmasters whose sites have unknowingly been recruited to drive traffic to illicit pharmacies.
Nonetheless, eradicating source infections at key websites could be disruptive, at least in the short term. 10% of source infections account for over 80% of total impact, in terms of appearing most often at the top of search results. If these infections were cleaned up, then attackers would likely struggle to adapt quickly, since placing websites at high-ranking search positions through search engine optimization can be a slow process.
Furthermore, search engines could take a more active role, and indeed Google has begun issuing notices of suspected compromised websites in its search results. However, this does not go nearly as far as interstitial warnings that actively block the user from visiting web servers that distribute malware. We encourage search engines to consider dropping such infected results altogether, given the illegal activity being facilitated.
Finally, by examining the redirection chains from infected hosts to pharmacies, we found a high degree of interconnection between seemingly disparate websites. Infected websites typically redirect to an intermediate website before redirecting once more to the destination pharmacy website. It turns out that over 92% of the pharmacies observed to be receiving traffic from search-redirection attacks are connected to 96% of the source infections. Additionally, we have found that a few intermediate redirectors connect most source infections to pharmacy websites. Consequently, we expect that taking down a few of these key redirectors could disrupt the affiliate network promoting pharmacies.
Given the enormous value of web search, it is no surprise that miscreants have taken aim at manipulating its results. We have gathered evidence of systematic compromise of high-ranking websites that have been reprogrammed to dynamically redirect to illicit online pharmacies. These search-redirection attacks are present in one third of the search results we collected. The infections persist for months, and 96% of the infected hosts are connected through redirections. We have also observed that legitimate health resources are nearly absent from the search results, having been completely pushed out of the search results by blog and forum spam and compromised websites.
However, we remain optimistic that the Internet’s defenders can disrupt this gloomy status quo. In order to successfully thwart search-redirection attacks, we believe that it is essential for any future countermeasures to involve important intermediaries such as web search engines, and to target malicious activity in the search results, not just their ads.
[1] Kanich, C.; Kreibich, C.; Levchenko, K.; Enright, B.; Voelker, G.; Paxson, V.; Savage, S. Spamalytics: An empirical analysis of spam marketing conversion. In Conference on Computer and Communications Security (CCS), Alexandria, VA, October 2008.
[2] Wang, Y.-M.; Ma, M.; Niu, Y.; Chen, H. Spam double-funnel: connecting web spammers with advertisers. 16th international conference on World Wide Web, WWW ‘07, pp.291-300, Ban, Alberta, Canada, 2007.
[3] Leontiadis, N.; Moore, T.; Christin, N. Measuring and analyzing search-redirection attacks in the illicit online prescription drug trade. Proceedings of USENIX Security 2011, San Francisco, CA, August 2011.
[4] Jackson Higgins, K. Google, GoDaddy help form group to fight fake online pharmacies. Dark Reading, December 2010. http://www.darkreading.com/security/privacy/228800671/google-godaddy-help-form-group-to-fight-fake-online-pharmacies.html.