2012-03-01
Abstract
DroidDream is a fully fledged mobile bot once a mobile device is rooted, with the ability to install applications of choice, navigate to websites, add bookmarks to the browser, manipulate text and voice messages, and communicate with a remote command and control server. John Foremost takes a closer look.
Copyright © 2012 Virus Bulletin
In 2011 one of the most notable mobile malware threats emerged in the wild: DroidDream (also known as Pjapps, Myournet, Lotoor, DroidRooter, and by several other aliases). DroidDream is a fully fledged mobile bot once a mobile device is rooted, with the ability to install applications of choice, navigate to websites, add bookmarks to the browser, manipulate text and voice messages, and communicate with a remote command and control server.
The name DroidDream is derived from some of the author’s comments in the code: ‘If the droid isn’t dream, don’t do anything evil, cause nightmares later.’
DroidDream was distributed in conjunction with dozens of legitimate applications, including games, ring tones, and more. Three developers – we20090202, kingmail2010 and Myournet – had their Google accounts suspended for spreading DroidDream code via the Android Market. Over 100 applications were distributed before the threats were identified and removed from various locations on the Internet. For example, Bowling Time, with MD5 d4fa864eedcf47fb7119e6b5317a4ac8, contains DroidDream. Other infected applications included:
Advanced App to SD, Advanced Barcode Scanner, Advanced Compass Leveler, Advanced Currency Converter, Advanced File Manager, Advanced Sound Manager, App Uninstaller, Basketball Shot Now, Best password safe, Bubble Shoot, Chess, Color Blindness Test, Dice Roller, Falling Ball Dodge, Falling Down, Finger Race, Funny Face, Funny Paint, Hilton Sex Sound, Hot Sexy Videos, hot.goddchen.sexyvideos, Magic Hypnotic Spiral, Magic Strobe Light, Music Box, Omok Five in a Row, org.droiddream.yellow4, Photo Editor, Piano, power.nick.ypaint, power.power.rate, powerstudio.spiderman, proscio.app.nick.ypaint, Quick Delete Contacts, Quick Notes, Scientific Calculator, Screaming Sexy Japanese Girls, Sexy Girls: Japanese, Sexy Legs, Spider Man, Super Guitar Solo, Super History Eraser, Super Ringtone Maker, Super Sex Positions, Super Sexy Ringtones, Super Stopwatch & Timer, super.mobi.eraser, super.sancron.ringtones.sexysb, Supre Bluetooth Transfer, Task Killer Pro and Tie a Tie.
Hostile components added to such apps included:
com.advanced.scientific.calculator, com.advanced.soundmanager, com.app.aun, com.apps.tosd, com.beauty.leg, com.bubble, com.dice.power, com.dice.power.advanced, com.dodge.game.fallingball, com.droiddream.advancedtaskkiller1, com.droiddream.android.afdvancedfm, com.droiddream.barcodescanner, com.droiddream.basketball, com.droiddream.blueftp, com.droiddream.bowlingtime, com.droiddream.comparator, com.droiddream.compasslevel, com.droiddream.daltonismo, com.droiddream.fallingball, com.droiddream.game.omok, com.droiddream.glowhockey, com.droiddream.howtotie, com.droiddream.lovepositions, com.droiddream.musicbox, com.droiddream.passwordsafe, com.droiddream.pewpew, com.droiddream.sexringtones, com.droiddream.stopwatch, com.droiddream.system.app.remover, com.editor.photoenhance, com.fall.down, com.fall.soft.down, com.free.chess, com.free.game.finger, com.hg.panzerpanic1, com.hz.game.mrrunner1, com.magic.spiral, com.power.basketball, com.power.demo.note, com.power.magic.strobelight, com.power.supersolo, com.quick.delete, com.sex.japaneese.girls, com.sexsound.hilton, com.sexy.hotgirls, com.sexy.legs, com.spider.man and com.super.mp3ringtone.
Despite Google responding quickly to abuse reports, over 50,000 downloads of known infected applications had already taken place. DroidDream demonstrated how trivial it is to create an online identity and subvert the weakly authenticated and weakly protected Android application marketplace. Consumers are quick to download and install whatever looks great, and is free – but with thousands of malicious applications now having been authored for the platform, users often get more than they bargained for.
DroidDream is configured within AndroidManifest.xml to run along with an application’s legitimate code. Reviewing the AndroidManifest file of an infected application provides several clues immediately. The following is from what started out as a bowling game, but has been infected and become much more:
versionCode
versionNameinstallLocation
namelabel
iconscreenOrientation
configChangesprocessvalue
authorities
minSdkVersionandroid*http://schemas.android.com/apk/res/androidpackagemanifest 1.8com.droiddream.
bowlingtimeuses-permissionandroid.permission.INTERNET#android.permission.READ_PHONE_STATE$android.
permission.CHANGE_WIFI_STATE$android.permission.ACCESS_WIFI_STATEapplicationactivity&cn.bluesky.
fingerbowling.FingerBowlingcom.android.root.main
intent-filteractionandroid.intent.action.MAINcategoryandroid.intent.category.LAUNCHERservice:remotecom.
android.root.Setting:remote2-com.android.root.AlarmReceiver meta-datacom.mobclix.APPLICATION_ID$E7
98E833-54EB-427E-8289-8E67B27B41AA.com.mobclix.android.sdk.MobclixBrowserActivityprovidercom.phonegap.
LocalProvider(com.droiddream.bowlingtime.localprovideruses-sdk
DroidDream-infected applications commonly include com.android.root. This is visible when viewing data from an APK, extracted, converted into a JAR, and then viewed within JD-GUI, as shown in Figure 1.
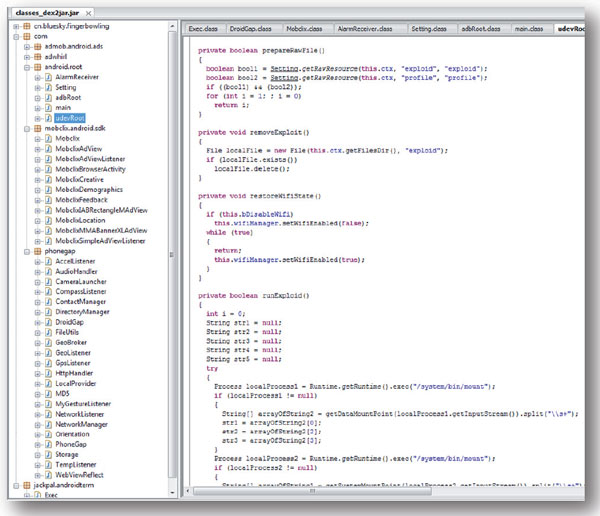
Figure 1. DroidDream-infected applications commonly include com.android.root. This is visible when viewing data from an APK, extracted, converted into a JAR, and then viewed within JD-GUI.
(Click here for a larger version of Figure 1.)
Notice the string ‘exploid’ shown in blue. When run, the code attempts to leverage exploits developed by Sebastian Krahmer. The exploits are referred to as ‘exploid’ and ‘rageagainstthecage’. If the exploits are leveraged successfully, the device is completely ‘owned’ and DroidDream is installed as a service called ‘com.android.root.Setting’.
After installation, the bot may attempt to communicate with a remote C&C server. The original C&C involved with DroidDream was hxxp://184.105.245.17:8080/GMServer/GMServlet. Once a connection is established the bot attempts to report to the remote C&C the device’s IMEI, Device ID, Line Number, and Subscriber ID. ‘/push/newandroidxml/’ may be used for remote commands sent to bots. An infected device may then be controlled remotely by an attacker.
XML formatting is used in data communications with a remote C&C. For example, a command may be issued to call a premium rate line, resulting in charges to the victim’s phone account. Com.android.root.adbRoot.crypto implements an XOR function to help obfuscate its communications.
DroidDream also includes an SQLite database management component. com.android.providers.downloadsmanager.DownloadCompleteReceiver runs in memory to look for an SQLite database sync. If a sync hasn’t taken place for at least five days it initiates one. To ensure regular updates a task is scheduled to run every two hours, with a delay of two minutes between executions, via com.android.providers.downloadsmanager.d.
A remote C&C server is also capable of manipulating phone numbers, including blacklisting. DroidDream uses the format ‘($blacklist_URL) + “/?tel=” + ###’, to blacklist numbers, where ### is a mobile number. Various commands may be used such as ‘push:sms’ for spimming, ‘soft’ for installing packages, ‘window’ for browser manipulation, ‘mark’ for adding a bookmark, and ‘xbox’ whose functionality is unknown. A prioritized list of browsers is included with the DroidDream installation, which includes com.android.browser, com.kolbysoft.steel, com.tencent.mtt, com.opera.mini.android, com.skyfire.browser, com.uc.browser and mobi.mgeek.TunnyBrowser.
With full functionality in such a bot, copycat attacks are likely to follow. One of the most dangerous parts of this code is the rooting component. Obviously all types of devices are vulnerable to various attacks that may allow for such rooting. Android is particularly vulnerable given the popularity of the operating system and the exploits that have emerged in recent months. Others are likely to be abused in a similar manner. Mobile malware attacks have matured from using the common social engineering tactic to more serious rooting attacks that can perform just about any function desired. From a vector standpoint, DroidDream reveals a small sliver of the widespread abuse that is ongoing even as this article is being authored, within a weakly authenticated and poorly controlled application market for Android and other operating systems.