2012-04-01
Abstract
Phishing is a global problem, but there are some geographic variances. Sebastien Goutal presents a study of the phishing attacks typically seen in France.
Copyright © 2012 Virus Bulletin
Phishing is a major threat to email users. Not only do victims face financial loss, but phishing can also result in a loss of trust and confidence in the organizations targeted in the attacks (ISPs, banks, social networks etc.). In this article we present a study of the phishing attacks that we typically see in our home market of France.
In our experience, phishers tend to be aged between 15 and 25 years old. They operate alone or in small groups, have relatively limited skills [1] and work on a small scale, using several hacked servers and hosted services.
In contrast, a typical spammer is a professional criminal with significant technical skills [2] and access to many resources. Spammers maintain large networks and send email in very high volumes. While a phisher will send at most a few tens of thousands of emails per day, a botnet has the capacity to send hundreds of millions of emails, and even up to several billion on a daily basis (for instance, the Rustock botnet has the capacity to send 30 billion emails per day).
Phishing provides a quick return on investment, and it requires few resources. The main challenge for phishers is converting money from online accounts into hard cash.
There is a persistent phishing threat in France that requires daily vigilance. Phishers operate mainly from Morocco (Rabat, Casablanca), and occasionally from Tunisia and France. Why Morocco and Tunisia? First, because the French language is widely spoken there, and secondly, these countries are located outside the European Union – where the risk of prosecution for damages caused in the European Union (and France in particular) is extremely small.
Every day, we identify between 10 and 20 new phishing campaigns or variations of existing ones.
The size of campaigns varies from a few hundred emails to tens of thousands of emails. They last for anywhere between one hour and several days. The average duration of the phishing campaigns we see is about seven hours, with a low and constant intensity.
Globally, there is a low volume of phishing: phishers attempt to keep their activity below a certain threshold in order to remain undetected for as long as possible. This is consistent with the phishing business model which requires a low volume to be profitable.
The phishing process is rather simple. First, the phisher needs at least two servers: one is dedicated to the dispatch of emails, and another hosts the phishing sites. In most of the cases that we see, phishers use hacked servers [3], but it has also become common for phishers to use hosted services [4].
Templates for phishing sites are widely available on the Internet, however most phishers create their own pages, basing their design heavily on the official site of the targeted company. They always include a script that will send notifications of captured data to one or more mailboxes – typically free webmail addresses such as Yahoo! or Gmail. This is the safest and easiest way to retrieve stolen credentials; storing them locally on the servers is risky in case the servers are forced to shut down due to abuse reports.
Next, the phisher has to compose a phishing email and send it to selected recipients. Previously, phishers compiled emails that were designed to resemble the legitimate emails sent by the target companies – including the company’s logo and layout – and the From and Subject headers, as well as body content, were explicit: their primary objective was to convince the majority of end-users that this was a legitimate email. Nowadays, regular phishing is still explicit [5] but less close to the genuine emails sent by the targeted companies: the primary objective is now to bypass spam filters, whose efficiency against phishing has increased.
The phisher must make a choice: write a ‘genuine’-looking phishing email that will trap a lot of end-users but will quickly be detected by spam filters, or write an obfuscated email that will trap fewer end-users but will be more difficult to detect. There is a growing tendency towards extreme obfuscation. For example, some phishing emails contain nothing but a link to the fraudulent site, which make them very difficult to detect in a predictive way.

Figure 1. This phishing scam contains various misspellings. Notice the contrast between the logo that will draw the recipient’s attention, and the misspelled words ‘Caiise d’Epargne’.
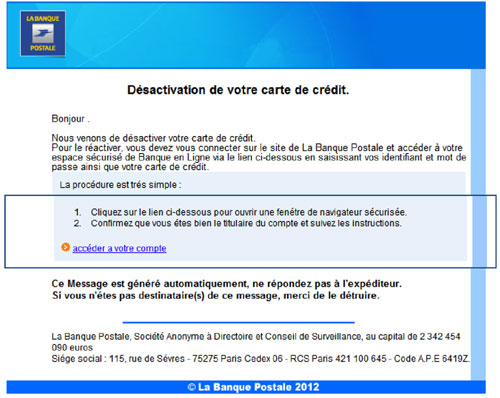
Figure 2. Phishing emails are often deliberately misspelled to bypass spam filters that may be triggered by certain keywords. However, this one is particularly well written: this is an image phishing scam, thus there is no need for misspellings.
We see the same arguments being used repeatedly in phishing campaigns to convince the end-user to take action:
suspicious connection attempts to your account
unusual transactions on your account
an unauthorized transaction on your account
a transaction error
account or credit card suspended
new message received
new invoice received.
It is also very common for phishing emails to request confirmation of customer credentials in order to enhance security: phishers use and abuse the fact that a lot of people are already aware of phishing scams.
Finally, before launching the phishing campaign, the phisher sends one or several phishing emails to the targeted ISP, using an email address hosted by the ISP. By doing this, he can make sure that the phishing campaign will not be blocked from the very beginning. He can then launch the campaign, and start to harvest the stolen data.
We often see stolen credit card credentials being used to fund online credit accounts, such as PayPal and Ogone. The credit is used for various operations:
Purchase of high-value consumer goods (laptop computers, tablet computers, consoles etc.), which are then resold via classified ad websites [6].
Purchase of plane tickets, which are then resold at lower prices.
Purchase of hosting services to perpetuate the phishing business.
As money laundering is a complex process and requires close acquaintance with criminal organizations, some phishers also sell credential databases on the black market. These may be used for other activities such as identity theft.
The obvious limitation to the business model is the difficulty of converting money from online accounts into hard cash.
Typically, we see the following targets of phishing campaigns:
Internet service providers
Banks (La Banque Postale, BNP Paribas, Crédit Agricole, Crédit Mutuel, Caisse d’Epargne, Société Générale) and companies providing financial services (Visa, MasterCard, PayPal, Western Union)
Public services (income taxes, Caisse Primaire d’Assurance Maladie, Caisse d’Allocation Familiale, Electricité De France, Gaz De France)
Social networks (Facebook, Twitter)
Online games (battle.net, RuneScape)
Online auction services (eBay).
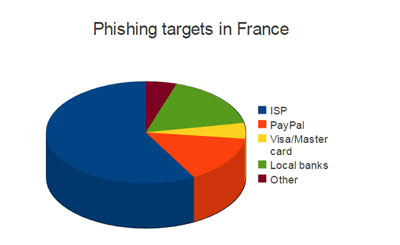
In France, phishers focus heavily on ISPs, because they can easily determine the victim’s ISP by extracting the domain name of their email address. PayPal [7] and Visa/MasterCard are also very highly targeted.
Local banks are also targeted. The phisher does not know the identity of the victim’s bank, and there are around ten major banks in France – the probability that the victim is a customer of any of these banks is around 10%. Despite this, phishers still focus on local banks as customers tend to trust them, and are thus more likely to be trapped.
We rarely see phishers targeting foreign banks (e.g. Bank Of America, Chase, Wells Fargo, Santander, Halifax, Barclays, HSBC etc.), instead focusing their activities on French banks to maximize their return on investment.
Nowadays, phishing is one of the most problematic threats in mail security: in contrast to spam, phishing campaigns are low-volume, targeted, transient, and thus both very difficult to detect in a feedback loop and almost non-existent in honeypots. Moreover, phishing is very profitable for the attackers and can be extremely damaging for the victims.
Two layers of security are generally set up to limit the damage caused by phishing. First, ISPs and ESPs implement message filtering to detect and reject phishing emails. Secondly, most popular Internet browsers provide anti-phishing features [8], the majority of which are based on live phishing URL database queries, to prevent access to forged websites. However, in both cases, the phishing attack first has to be detected and reported, and the delay in this process means that the initial victims go unprotected [9].
It is inevitable that, whatever the sophistication of the implemented protection technologies, phishers will manage to steal valid credentials and will try to use them. We must therefore limit damages by strengthening controls at the point at which these credentials will be used.
E-commerce websites should detect suspicious behaviour – such as multiple payment attempts with different credit card details – and should reject, log and report such attempts.
In addition, banks and online financial services should implement two-factor authentication. Two-factor authentication is an approach to authentication which requires the presentation of two or more of the three authentication ‘factors’ (something the user knows, something the user has, and something the user is). A classic approach is to send a confirmation code to a mobile phone (something the user has), and thus validate authentication. Widespread use of two-factor authentication should limit the damages caused by phishing.
Last but not least, it is essential that there is effective cooperation between authorities in different countries: phishing is an international threat, and we know that phishers take advantage of weaknesses in international cooperation and often carry out their actions with a sense of impunity [10].
[1] Knowledge of a scripting language and a basic knowledge of Apache, HTTP and SMTP protocols is more than sufficient to conduct phishing campaigns.
[2] A spammer has to conduct vast malware campaigns to build spambot networks, handle complex peer-to-peer interaction between botnet elements, and monitor an infrastructure of significant size.
[3] For instance, a lot of servers hosting misconfigured or vulnerable versions of WordPress are used by phishers to host phishing sites. They can easily be identified by the ‘ wp-’ prefix in the phishing link.
[4] However, the rental of hosted services requires prior theft of credit card credentials in order to anonymize the financial source.
[5] Although this does not prevent phishers from using classic spam techniques to bypass spam filters, such as misspellings or character substitutions.
[6] Leboncoin.fr is the most popular classified ad website in France, and as such it is widely used for the resale of goods that have been obtained illegally. For this reason the site is under constant surveillance by law enforcement. eBay is also widely used for this purpose.
[7] The number of PayPal accounts is estimated to be over 230 million. It is therefore very likely that the recipient of a phishing email has a PayPal account.