Recently, many users worldwide have been complaining about receiving emails from senders like '[email protected]'. The emails claim that the user's computer has been hacked and that they have been caught them in some awkward situations that will be shared publicly unless they pay a ransom in Bitcoin. In fact, the users receiving these emails have not been infected and there is no RAT controlling their computer (at least not this one).
The only malware involved is that which sends these emails from other compromised devices: these devices are used both as proxies to send blackmail emails to the victims, and for Monero mining. The victims' email addresses and passwords – used to make the emails appear more credible – were found in a password dump file. The capabilities of the malware are as follows:
Infected devices were able to reach more than 110,000 users in a very short time thanks to the malware's spreading capability.
A quick Google search revealed many users complaining about the 'saveyourself' scam virus, as well as many sites offering their products for removal of the malware (although the users that received the email were not infected by the malware itself – their emails were just exposed in a dump), which in some cases could, ironically, lead to malware infections. It is very possible that the malware author has gathered and combined several viruses and modified them to suit their own needs.
Example sample details (the file that is downloaded): https://www.virustotal.com/gui/file/d0fcb364a1d37c93740edcb88695de72de8b53fcf29c6bb0fcbc792897fd9b8b/details
Example infected file: https://www.virustotal.com/gui/file/af75c754649de2eec5122c381b4ccff583a29d8ab3d53fdaaa7a42085fe6ef39/details
The malware is designed to remain under the user's radar: the user thinks they are executing a legitimate program because it is eventually executed, but only after the injected section has been downloaded and the malware has been executed. The malware then deletes the alternate data stream to hide the fact that a file has been downloaded from the Internet.
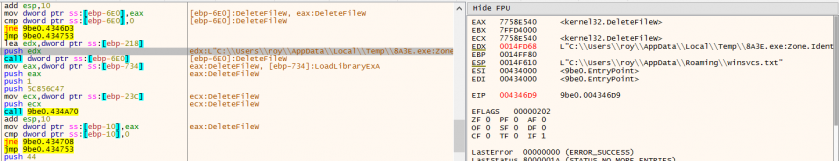 Figure 1: The downloaded file is deleted.
Figure 1: The downloaded file is deleted.
Then, it will apply persistence and spreading techniques, after which it will pause its activity for about 24 hours to avoid detection. Only then will the malware continue to download additional executables.
Next, the malware uses the computer as a proxy station to send blackmail emails to users, and uses the CPU for Monero mining. To maintain a low profile, the malware will use only 50% of the CPU's capability (most of the time). The specimen can also read clipboard data and replace Bitcoin wallet addresses with its own address.
9be07.exe C:\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\IQDX3EW0\e[1].exe
9be07.exe C:\Users\user\AppData\Local\Temp\409F.exe
9be07.exe C:\Users\user\AppData\Local\Temp\dd_9be07_decompression_log.txt
409F.exe C:\Windows\165630396\sysblks.exe
sysblks.exe C:\Users\user\AppData\Local\Temp\30131.exe
sysblks.exe C:\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\S8MMEKF7\1[1]
sysblks.exe C:\Users\user\AppData\Local\Temp\17926.exe
sysblks.exe C:\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\IQDX3EW0\5[1]
sysblks.exe C:\Users\user\AppData\Local\Temp\33947.exe
sysblks.exe C:\Users\user\AppData\Local\Temp\33947.exe
sysblks.exe C:\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\S8MMEKF7\6[1]
svchost.exe C:\Windows\Prefetch\30131.EXE-D5E0685B.pf
17926.exe C:
17926.exe C:\Users\user\Desktop\chosen\procexp.exe
17926.exe C:\Users\user\Desktop\chosen\procexp.exe
17926.exe C:\Users\user\Desktop\chosen\strings.exe
17926.exe C:\Users\user\Downloads\7z1900-x64.exe
17926.exe C:\Users\user\Downloads\ChromeSetup.exe
17926.exe C:\Users\user\Downloads\Firefox Installer.exe
17926.exe C:\Users\user\Downloads\Firefox Installer.exe
sysblks.exe C:\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\IQDX3EW0\7[1]
sysblks.exe C:\Users\user\AppData\Local\Temp\16945.exe
16945.exe C:\ProgramData\IlKTmhStyg\cfg
16945.exe C:\ProgramData\IlKTmhStyg\cfgi
16945.exe C:\ProgramData\IlKTmhStyg\sysdrv32
16945.exe C:\ProgramData\IlKTmhStyg\r.vbs
wscript.exe C:\Users\user\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\KmJlZQXSMi.url
syshwbr.exe D:\__\chosen\Procmon.exe
syshwbr.exe D:\__\chosen\strings64.exe
10719.exe C:\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\SL0QQXSC\715[1].txt
10719.exe C:\Users\user\AppData\Local\Temp\8191564810642097.jpg
23923.exe C:\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\SL0QQXSC\n[1].txt
23923.exe C:\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\SL0QQXSC\1338[1].txt
23923.exe C:\Users\user\AppData\Local\Temp\5706894215163142.jpg
lsass.exe \\Dell_LAB2*\MAILSLOT\NET\NETLOGON
%HOMEPATH%\cookies\user@icanhazip[1].txt
%WINDIR%\1233324385\sysgkvm.exe
<REM_DRIVE>:\.lnk
<REM_DRIVE>:\__\drivemgr.exe
<REM_DRIVE>:\__\notepad.exe
<REM_DRIVE>:\autorun.inf
And every file found on the remote drive
<HKLM>\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List\%WINDIR%\1233324385\sysgkvm.exe
%WINDIR%\1233324385\sysgkvm.exe:*:Enabled:Microsoft Windows Driver
<HKLM>\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\\Microsoft Windows Driver%WINDIR%\1233324385\sysgkvm.exe
<HKCU>\Software\Microsoft\Windows\CurrentVersion\Run\\Microsoft Windows Driver%WINDIR%\1233324385\sysgkvm.exe
<HKLM>\SOFTWARE\Microsoft\Security Center\AntiVirusOverride 0x00000001
<HKLM>\SOFTWARE\Microsoft\Security Center\UpdatesOverride 0x00000001
<HKLM>\SOFTWARE\Microsoft\Security Center\FirewallOverride 0x00000001
<HKLM>\SOFTWARE\Microsoft\Security Center\AntiVirusDisableNotify 0x00000001
<HKLM>\SOFTWARE\Microsoft\Security Center\UpdatesDisableNotify 0x00000001
<HKLM>\SOFTWARE\Microsoft\Security Center\AutoUpdateDisableNotify 0x00000001
<HKLM>\SOFTWARE\Microsoft\Security Center\FirewallDisableNotify 0x00000001
%WINDIR%\1233324385\sysgkvm.exe
%TEMP%\19713.exe
%TEMP%\33418.exe
%TEMP%\25177.exe
%TEMP%\10744.exe
%TEMP%\21972.exe
%WINDIR%\1782026319\sysxqbm.exe
%WINDIR%\2481323766\sysdxun.exe
%WINDIR%\2432812312\syszpnq.exe
http://185.176.27.132/t.php?new=1
http://urusurofhsorhfuuhl.cc/t.php?new=1
http://193.32.161.73/t.php?new=1
http://185.176.27.132/1
http://185.176.27.132/2
http://185.176.27.132/3
http://185.176.27.132/4
http://185.176.27.132/5
http://185.176.27.132/6
http://185.176.27.132/7
http://185.176.27.132/8
http://icanhazip.com/
http://193.32.161.73/_1/n.txt
http://193.32.161.73/_1/1118.txt
http://193.32.161.73/_2/n.txt
http://193.32.161.73/_2/1315.txt
http://193.32.161.73/_3/n.txt
http://193.32.161.73/_3/895.txt
http://193.32.161.73/_5/n.txt
http://193.32.161.73/_5/145.txt
185.176.27.132:80
7.5.7.7:80
98.137.159.24:25 (TCP)
106.10.248.84:25 (TCP)
98.137.159.24:25
Many smtp communications
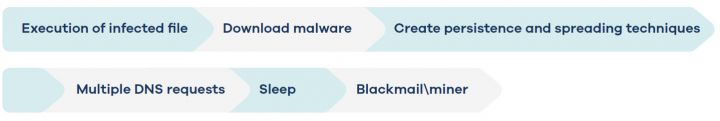 Figure 2: Full execution flow.
Figure 2: Full execution flow.
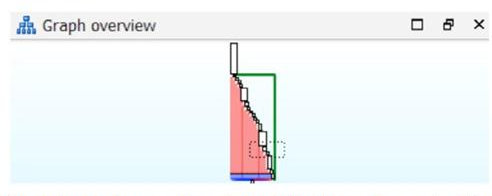 Figure 3: Execution flow of section .zero.
Figure 3: Execution flow of section .zero.
The malware changes the entry point to this section so that the malware code is the first code to be executed.
All infected samples contain an additional section header: '.zero'.
 Figure 4: The .zero section header visible in Process Monitor.
Figure 4: The .zero section header visible in Process Monitor.
The infected samples are downloaders: they are injected with the section that has the URL required to download the main malware.
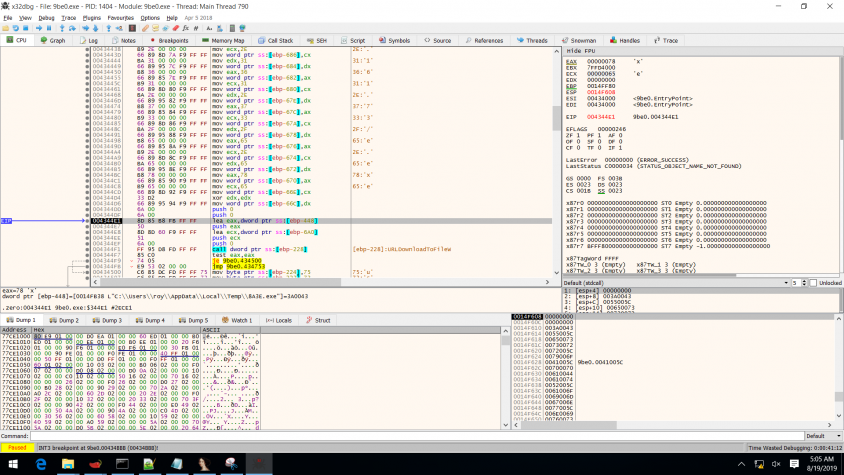
Looking at this section in IDA, we can see that the section's functionality is to download additional files, disguise that they were downloaded from the Internet, and execute the downloaded binary.
The section with the URL creates a text file in the user's appdata\roaming\winsvc.txt. The text file will either be empty, or its content will have been deleted, or it will be used as an infection marker.
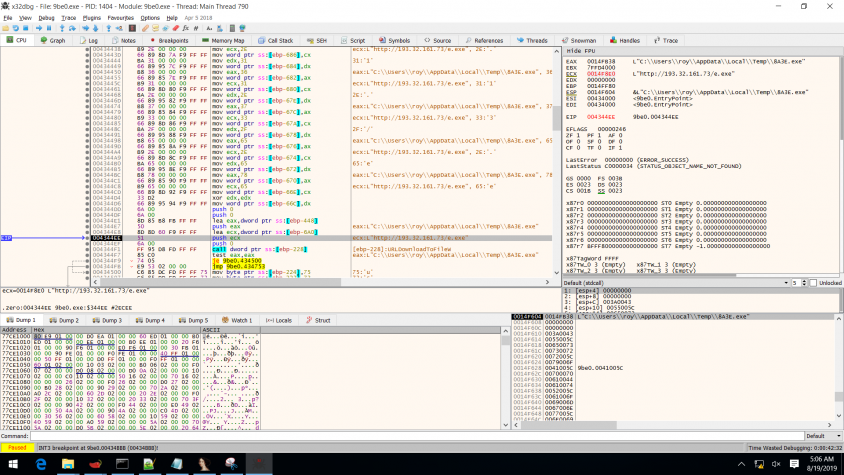
The URL section then dynamically calls the urlmon function, UrlDownloadToFile, with a predefined URL (http://193.32.161.73/e.exe) and downloads the function to the temp folder. Some samples turn into an e[1].exe or a.exe file. Next, the URL section loads user32.dll and deletes the alternate data stream 'zone.identifier' to hide the fact that it was downloaded from the Internet. After that, the downloaded file is executed. Finally, the section with the URL will also execute the original program that was infected (even if it didn't succeed in one of its steps).
The predefined URL is not written as one string; it is separated into ASCII characters that are 'moved' to the registry one by one (see Figure 5). Consequently, the sample looks legitimate while it's running (the company name and other characteristics remain the same, but the signature doesn't).
 Figure 5: The ASCII characters that form the URL.
Figure 5: The ASCII characters that form the URL.
After the file is downloaded, it executes as 'sys****.exe' (using four random characters on each execution).
The file is located in a hidden folder that it creates on C:\Windows\310926922 (the number is randomly generated on each execution). Note: The attacker has made it more difficult to view all of the hidden items. It's not enough simply to tick 'view hidden items' in the folder view options. The system files option in the settings must also be ticked.
The malware then tries to resolve multiple addresses and queries '/t.php?new=1' on each of them.
As shown in Figure 6, all the requests result in a 502 error except the one that the hacker tries to reach via IP address 185.176.27.132/t.php?new=1, which results in response code 200, with '0' as the answer server:nginx/1.10.3 (ubuntu).
The malware is then able to create files in the user's appdata temp folder: C:\Users\user~1\AppData\Local\Temp.
In Figure 7 we can see that the process reads the password dump file and then sends the emails.
 Figure 6: Most HTTP queries result in 502 errors.
Figure 6: Most HTTP queries result in 502 errors.
 Figure 7: The password dump file is read and the emails are sent.
Figure 7: The password dump file is read and the emails are sent.
The miner communicates with the pool URL at port 7777.
c:\windows\notepad.exe -c "c:\programdata\IlKTmhStvg\cfg" (the 'IlKTmhStvg' part is randomly generated in every execution).
The program 'notepad.exe' might actually be the miner and not Notepad.
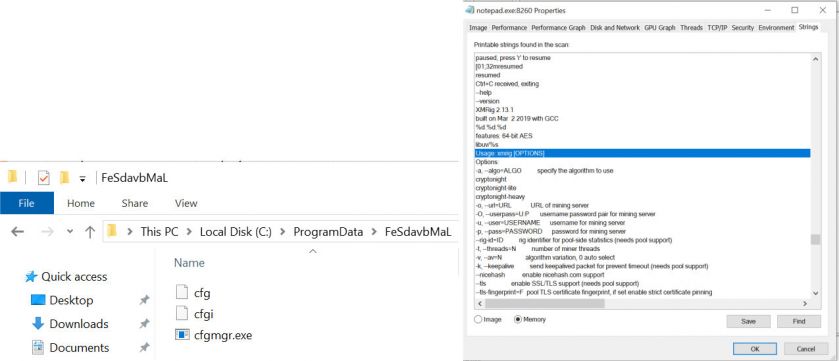 Figure 8: Strings in the memory of 'notepad.exe' that runs the miner.
Figure 8: Strings in the memory of 'notepad.exe' that runs the miner.
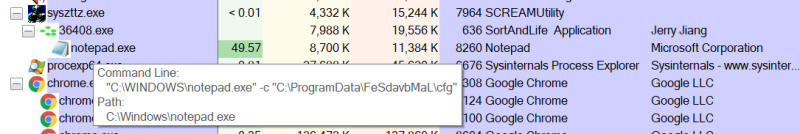 Figure 9: Process tree of syszttz.exe running the process that runs the miner with command line to the configuration file.
Figure 9: Process tree of syszttz.exe running the process that runs the miner with command line to the configuration file.
The malware writes itself to the run key (both HKLM and HKCU) as 'Microsoft Windows Driver' (HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run Microsoft Windows Driver), so it will run after restart.
The executable is the one in the Windows hidden folder.
It then disables Windows Defender anti-virus: HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Security Center AntiVirusOverride.
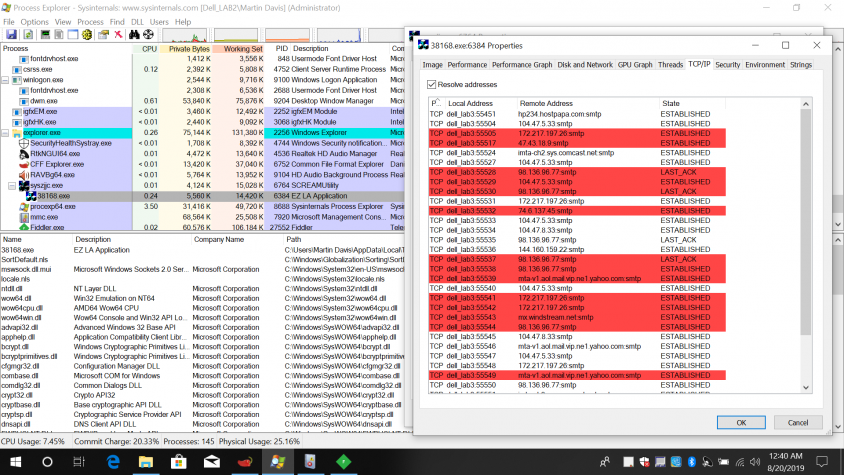
The infected files look innocent in procexp because all of their characteristics are preserved: description, company name, icon.
After about 24 hours, the malware will have downloaded dozens of executables onto the victim's system. We noticed two main activities running on the system:
As for the first activity, the CPU usage was kept at 50% to avoid user suspicion, and the strings extracted from that process indicated that it was a Monero miner. The miner had placed a Base64-encoded configuration file in the folder. It also had a watchdog that revived the process that had been shut down. In addition, the miner was also communicating with the pool address in port 8888.
The second activity was noticed while analysing the network logs: multiple requests sent to addresses in port SMTP 25. In addition, there were multiple '.jpg' files in the temp folder. The files were not real pictures, but text files containing email addresses and passwords. The attacker uses the victim's computer to brute force as many accounts as it can. It also might be downloading different executables based on different parameters. For example, if the parameter is a domain, the attacker might download ransomware or spread targeted RATs.
The malware spreads as much as it can: it infects connected USB devices and network shares. In both cases it creates a hidden folder named '_' (underscore) and copies all of the drive content there. It then places a link in the main view that leads to the folder as well as executing a file called 'drivemgr.exe' that it placed there. In addition, the malware writes an '.ini' file for autoplay.
 Figure 10: A hidden folder named '_' is created.
Figure 10: A hidden folder named '_' is created.
The .ini file is interesting because, in addition to the expected 'drivemgr.exe' execution, the malware also logs the first computer name and user name that opened the executable (and, in fact, infected the station).
 Figure 11: The .ini file.
Figure 11: The .ini file.
Another thing the malware does to make sure it will not disappear easily is to infect all executable files found on the machine. It infects the files by adding the '.zero' section that downloads the malware. So, besides copying a malicious executable that will surely be executed on the machine when clicking on the link or connecting it to a computer that will autoplay it, the malware also ensures that using any of the executables will infect the system as well.
The desired executable will then run as it should, so the user won't suspect that there's anything wrong. Nor will anything look suspicious when analysing the sample since, at first glance, it will look like known software (icon, signature, strings, functionality).
The malware also creates vbs c:\programdata\IlKTmhStvg\r.vbs and C:\users\martin\appdata\roaming\microsoft\windows\start menu\programs\startup\KmJIZQXSMi.url.
One way to identify an infected file is to look at the TimeDateStamp (found at Nt headers -> file header) where we'll see that its original value has been changed to '0000DEAD'.
 Figure 12: The original value of the TimeDateStamp field was changed to '0000DEAD'.
Figure 12: The original value of the TimeDateStamp field was changed to '0000DEAD'.
The malware also changes the 'AddressOfEntryPoint' field (found at Nt Headers → optional header) from .text to .zero.
 Figure 13: The AddressOfEntryPoint field is changed to .zero.
Figure 13: The AddressOfEntryPoint field is changed to .zero.
More changes can be found at Nt Headers → optional header → Data directories. For example, the original executable has the field 'Security Directory RVA' offset in the .rsrc section whilst the infected file changed it to .reloc at the other offset value.
The executable also moves 'TLS directory RVA' somewhere in .rdata and all the offset values change as a result.
Another change is that the infected file has a 'TLS directory' that didn't exist beforehand.
After analysing packets, we've seen that the malware sends emails to the previously mentioned addresses.
In the email, the hacker claims that he has full control of the recipient's computer, which is why he knows the user's password and has been able to record him in an awkward situation. The hacker also threatens to send the video recording to all of the user's contacts and social media accounts unless the user pays 1,600 in BTC, which is to be transferred to the hacker's Bitcoin wallet:
Wallet number: 194iizBy5K9AVDqTBvzDAWR6t9MrrqvseZ
While on the attacked machine, we tried to search for this wallet, so we copied the address from the threatening email. However, when we pasted the wallet's address, we found that it had changed because the attacker monitors clipboard data, and if he finds this address, he replaces it with a different one, making it harder to track him. (The attacker might also be listening for addresses and stealing passwords.)
Unfortunately for the attacker, the search for his address revealed that he hadn't received any money.
Also unfortunately for the attacker most, if not all, of his mails were blocked by companies' anti-spam engines (Google, Outlook, Yahoo!).
Of course, there are a lot of wallets and different messages, but the ones we checked were all empty with no transaction history.
Figure 14: Empty Bitcoin wallet with no transaction history.
Any anti-virus product should be able to remove this malware. In the case of Reason Antivirus, the instructions are as follows:
Example downloader hashes
https://analyze2.intezer.com/#/analyses/988aec6a-d2d0-40a2-8d0f-1056649d98da
https://ransomwaretracker.abuse.ch/ip/208.100.26.251/
https://www.threatminer.org/host.php?q=208.100.26.251
https://jbxcloud.joesecurity.org/analysis/936034/0/html
https://www.virustotal.com/gui/file/d0fcb364a1d37c93740edcb88695de72de8b53fcf29c6bb0fcbc-
792897fd9b8b/behavior/Dr.Web%20vxCube
https://www.virustotal.com/gui/file/b9b4511065cb56bd162e143c22cf2afe32e3ee6617ba5a4852182cb-
0781f18f1/behavior/Rising%20MOVES
https://www.virustotal.com/gui/ip-address/35.225.160.245/details
https://www.virustotal.com/gui/ip-address/208.100.26.251/details
https://www.virustotal.com/gui/ip-address/7.5.7.7/relations
https://www.virustotal.com/gui/ip-address/193.32.161.73/relations
https://nexusconsultancy.co.uk/blog/email-scam-ashamed-of-yourself/
The following are a selection of screenshots taken during the analysis.
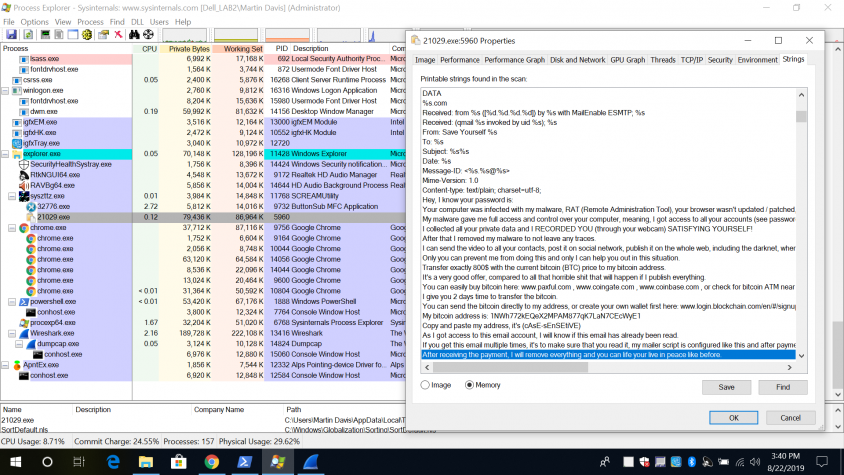
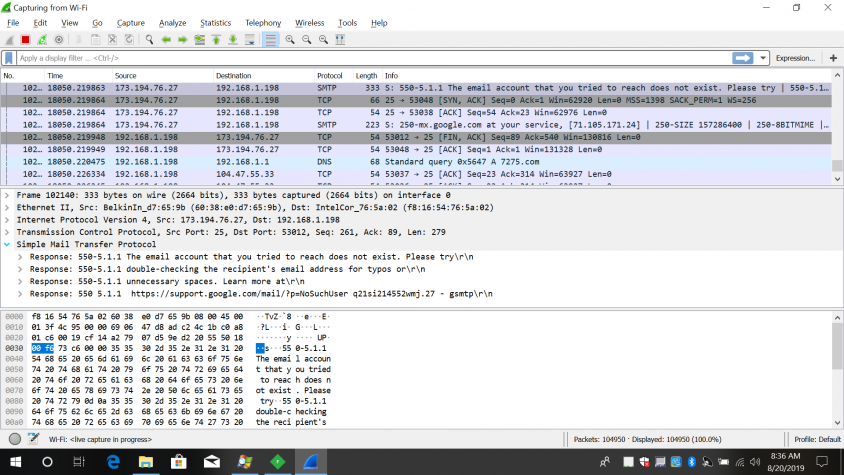 In the blackmail message extracted from the network pcap, we can see that the file is being blocked by anti-spam engines.
In the blackmail message extracted from the network pcap, we can see that the file is being blocked by anti-spam engines.
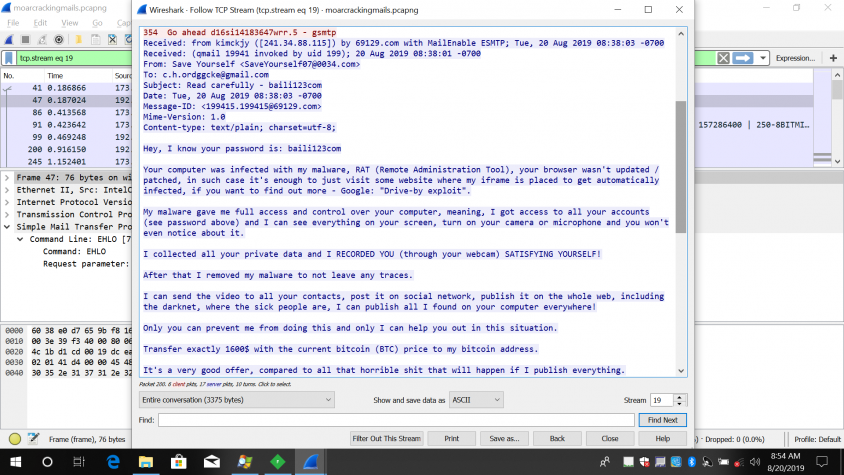
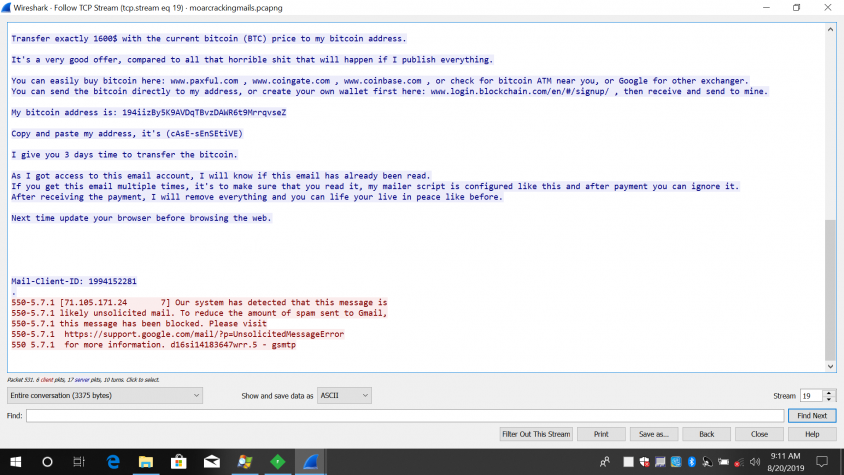 We can see that the file is being blocked by anti-spam engines.
We can see that the file is being blocked by anti-spam engines.
This is the address that is replaced by the copy-paste.