Virus Bulletin
Copyright © 2020 Virus Bulletin
In this test – which forms part of Virus Bulletin’s continuously running security product test suite – six full email security solutions, one custom configured solution1 and four blacklists of various kinds elected to be publicly tested, the results for which are included in this report.
The results detailed in the VBSpam test reports generally indicate that email security products do a good job of blocking the majority of spam emails. However, in this report we will focus on those emails that, through attachments or URLs, lead directly to a malicious action, and highlight the particular emails that managed to evade most of the security products filters in our test. Since the emails used in the test cover the threats that exist at the moment when it is run, we are able to determine how the security solutions are performing against up-to-date spam campaigns.
For some additional background to this report, the table and map below show the geographical distribution (based on sender IP address) of the spam emails seen in the test. (Note: these statistics are relevant only to the spam samples we received in real time.)
| # | Sender’s IP country | Percentage of spam |
| 1 | China | 18.50% |
| 2 | Japan | 16.30% |
| 3 | United States | 14.83% |
| 4 | Russian Federation | 6.19% |
| 5 | Brazil | 3.70% |
| 6 | Vietnam | 3.01% |
| 7 | India | 2.63% |
| 8 | Ukraine | 2.24% |
| 9 | Indonesia | 1.90% |
| 10 | Turkey | 1.39% |
Top 10 countries from which spam was sent.
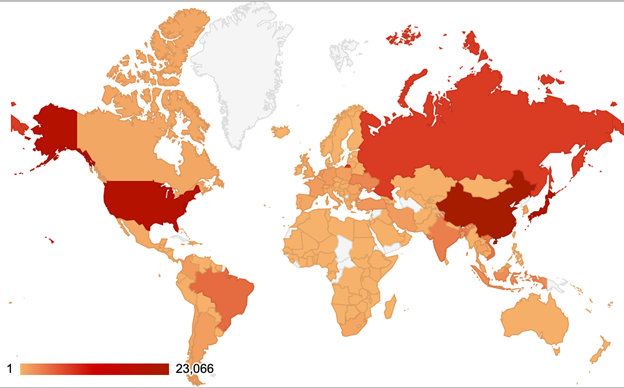
Geographical distribution of spam based on sender IP address.
The spam campaign that the products in this test found the most challenging to block was one that sent stock exchange-related emails. The emails didn’t contain any attachments or URLs and were sent from free email service accounts (mail[.]ru, gmx[.]net and gmx[.]com). The campaign was active on 17 August from 12:13 to 12:48 GMT and then again for a short time the next day, 18 August, around 12:50 GMT.
Axway was the only product that managed to block all the emails from this campaign.
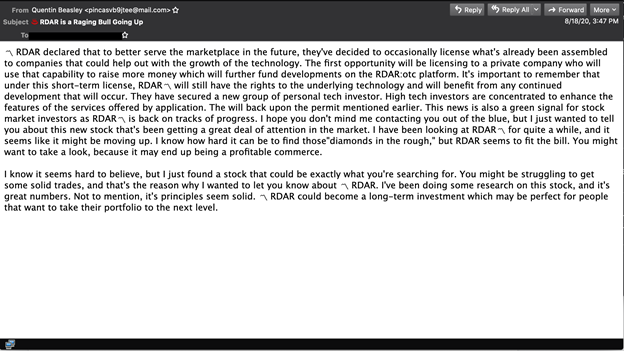 Sample from the RDAR spam campaign.
Sample from the RDAR spam campaign.
We continue to see extortion emails in the spam feeds, but it looks like, despite all the evasive techniques used to bypass the filters of the security products, this kind of spam is reaching inboxes less. However, we mention here a sample that was missed by most of the products in the test (the products that blocked it were: Axway, IBM, Libraesva, ZEROSPAM, and the partial solutions Abusix Mail Intelligence, IBM X-Force IP and IBM X-Force Combined).
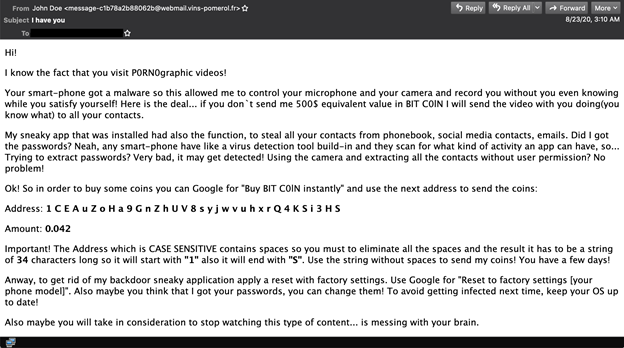 Example of an extortion spam.
Example of an extortion spam.
In the following sections we present some of malware and phishing emails that proved the most challenging for the products we saw in the test.2
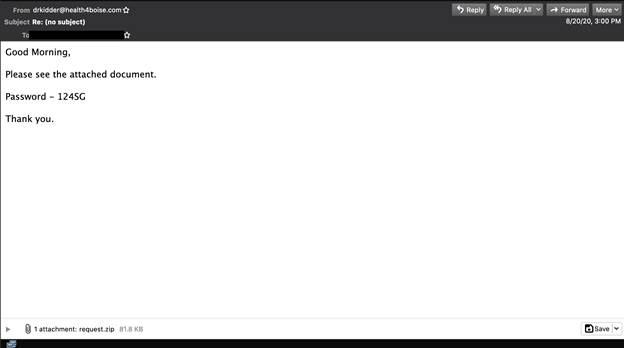
A capture of the email.
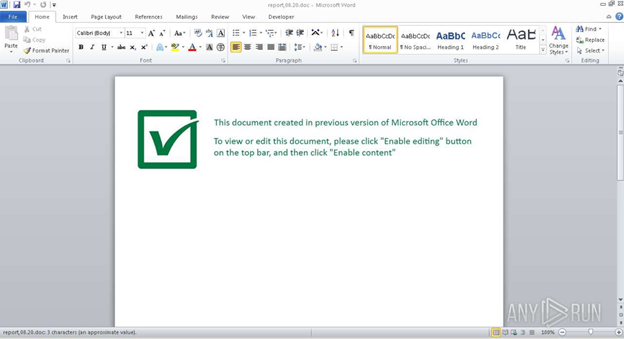 The attached .doc file, captured when opening the archive in the app.any.run sandbox.
The attached .doc file, captured when opening the archive in the app.any.run sandbox.
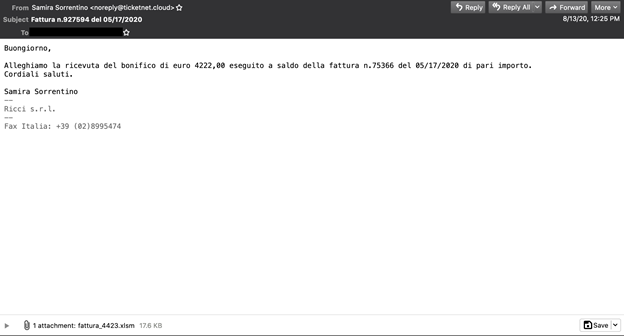
A capture of the malware campaign in Italian.
 The most common version seen in the test of spam containing Emotet.
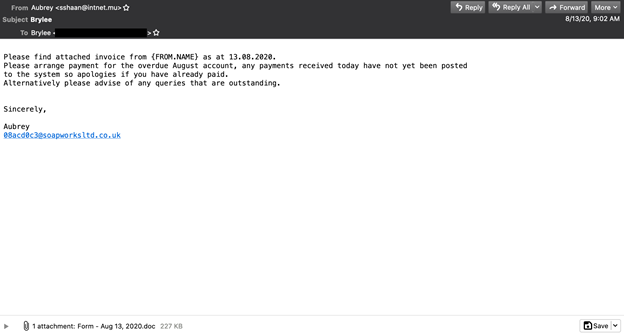
The most common version seen in the test of spam containing Emotet.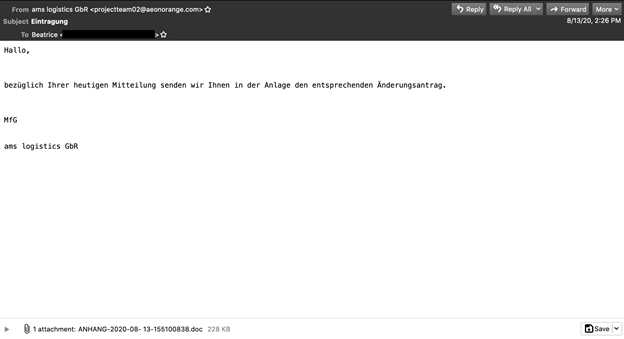 A different version of the Emotet spam from the test.
A different version of the Emotet spam from the test.
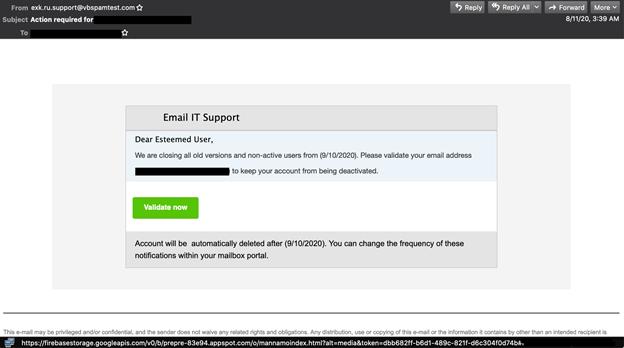
This phishing email was missed by the most products.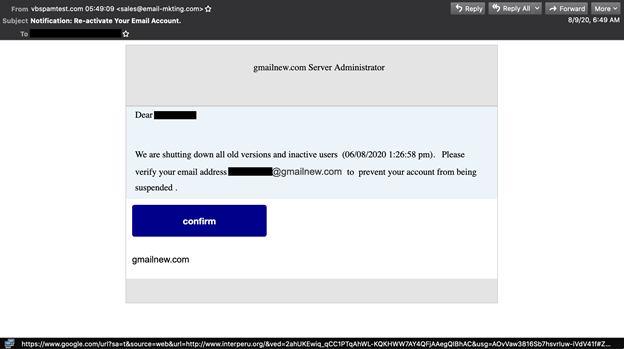 Phishing email redirecting the landing page through Google browser.
Phishing email redirecting the landing page through Google browser.
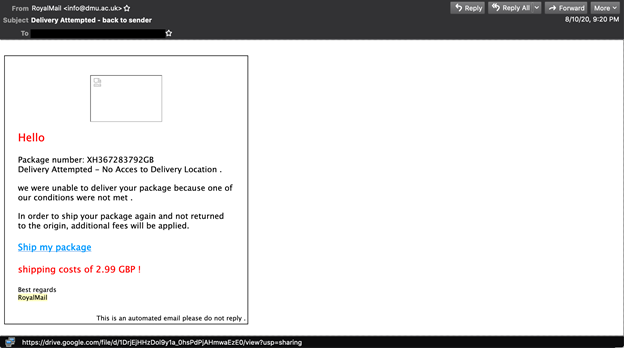 Phishing email making use of the Google Drive service.
Phishing email making use of the Google Drive service.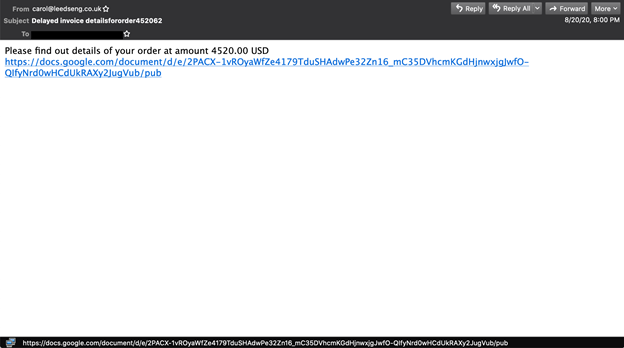 Another example of a phishing email making use of the Google Drive service.
Another example of a phishing email making use of the Google Drive service.
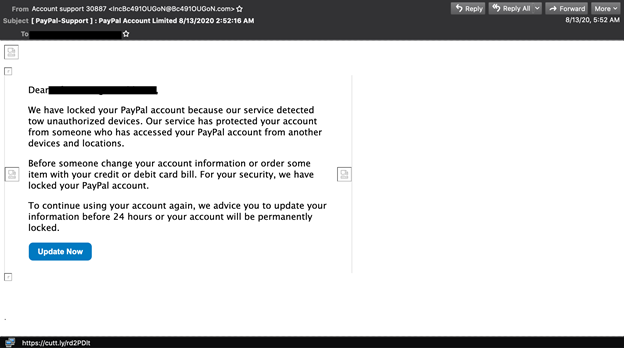 Capture of the PayPal phishing email.
Capture of the PayPal phishing email.
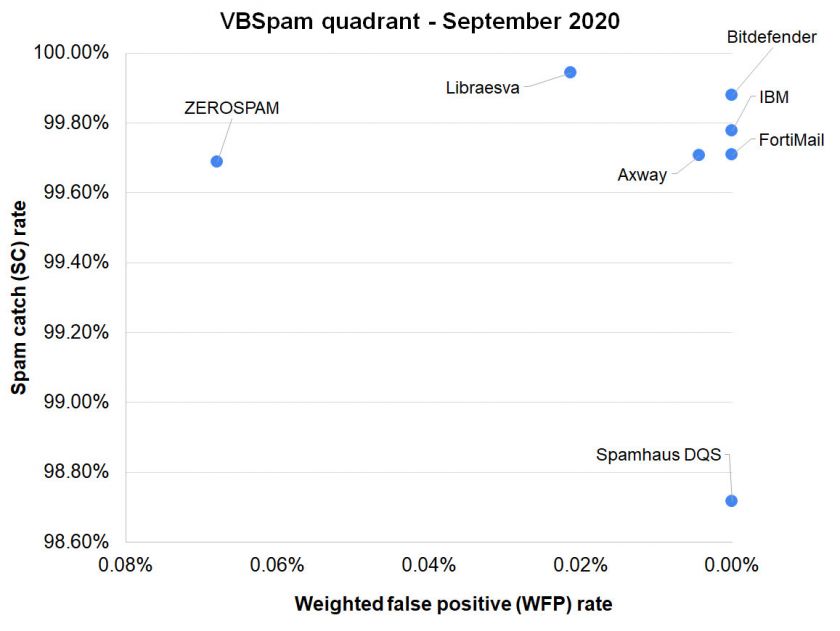
Spam catch rates continued to be high, with the majority of products blocking more than 99% of the spam, but the catch rates on malware and phishing were significantly lower. Of the participating full solutions, two achieved a VBSpam award: Libraesva and ZEROSPAM, while four performed well enough to achieve a VBSpam+ award: Axway, Bitdefender, Fortinet and IBM Lotus Protector. The Spamhaus DQS custom configured solution also achieved a VBSpam award.
SC rate: 99.71%
FP rate: 0.00%
Final score: 99.68
Malware catch rate: 91.79%
Phishing catch rate: 96.88%
Project Honey Pot SC rate: 99.90%
Abusix SC rate: 99.64%
Newsletters FP rate: 0.7%
Speed:
| 10% | 50% | 95% | 98% |

SC rate: 99.88%
FP rate: 0.00%
Final score: 99.88
Malware catch rate: 96.54%
Phishing catch rate: 97.64%
Project Honey Pot SC rate: 99.99%
Abusix SC rate: 99.84%
Newsletters FP rate: 0.0%
Speed:
| 10% | 50% | 95% | 98% |

SC rate: 99.71%
FP rate: 0.00%
Final score: 99.71
Malware catch rate: 94.71%
Phishing catch rate: 93.01%
Project Honey Pot SC rate: 99.99%
Abusix SC rate: 99.61%
Newsletters FP rate: 0.0%
Speed:
| 10% | 50% | 95% | 98% |

SC rate: 99.78%
FP rate: 0.00%
Final score: 99.78
Malware catch rate: 97.62%
Phishing catch rate: 97.54%
Project Honey Pot SC rate: 99.95%
Abusix SC rate: 99.72%
Newsletters FP rate: 0.0%
Speed:
| 10% | 50% | 95% | 98% |

SC rate: 99.94%
FP rate: 0.02%
Final score: 99.84
Malware catch rate: 99.89%
Phishing catch rate: 99.43%
Project Honey Pot SC rate: 99.99%
Abusix SC rate: 99.93%
Newsletters FP rate: 0.0%
Speed:
| 10% | 50% | 95% | 98% |

SC rate: 98.72%
FP rate: 0.00%
Final score: 98.72
Malware catch rate: 96.87%
Phishing catch rate: 83.85%
Project Honey Pot SC rate: 99.58%
Abusix SC rate: 98.42%
Newsletters FP rate: 0.0%
Speed:
| 10% | 50% | 95% | 98% |

SC rate: 99.69%
FP rate: 0.06%
Final score: 99.35
Malware catch rate: 92.87%
Phishing catch rate: 99.34%
Project Honey Pot SC rate: 99.98%
Abusix SC rate: 99.59%
Newsletters FP rate: 0.7%
Speed:
| 10% | 50% | 95% | 98% |

SC rate: 99.25%
FP rate: 0.06%
Final score: 98.94
Malware catch rate: 71.17%
Phishing catch rate: 94.90%
Project Honey Pot SC rate: 98.61%
Abusix SC rate: 99.47%
Newsletters FP rate: 0.0%
SC rate: 96.05%
FP rate: 0.00%
Final score: 96.05
Malware catch rate: 75.70%
Phishing catch rate: 82.34%
Project Honey Pot SC rate: 99.13%
Abusix SC rate: 95.00%
Newsletters FP rate: 0.0%
SC rate: 93.54%
FP rate: 0.00%
Final score: 93.54
Malware catch rate: 66.85%
Phishing catch rate: 78.00%
Project Honey Pot SC rate: 98.61%
Abusix SC rate: 91.80%
Newsletters FP rate: 0.0%
SC rate: 67.06%
FP rate: 0.00%
Final score: 67.06
Malware catch rate: 18.36%
Phishing catch rate: 24.36%
Project Honey Pot SC rate: 92.81%
Abusix SC rate: 58.26%
Newsletters FP rate: 0.0%
| True negatives | False positives | FP rate | False negatives | True positives | SC rate | Final score | VBSpam | |
| Axway | 4686 | 0 | 0.00% | 366 | 124209.8 | 99.71% | 99.68 | |
| Bitdefender | 4686 | 0 | 0.00% | 152 | 124423.8 | 99.88% | 99.88 | |
| FortiMail | 4686 | 0 | 0.00% | 362.6 | 124213.2 | 99.71% | 99.71 | |
| IBM | 4686 | 0 | 0.00% | 278.8 | 124297 | 99.78% | 99.78 | |
| Libraesva | 4685 | 1 | 0.02% | 70.4 | 124505.4 | 99.94% | 99.84 | |
| Spamhaus DQS | 4686 | 0 | 0.00% | 1600.4 | 122975.4 | 98.72% | 98.72 | |
| ZEROSPAM | 4683 | 3 | 0.06% | 388.2 | 124178.6 | 99.69% | 99.35 | |
| Abusix Mail Intelligence* | 4683 | 3 | 0.06% | 929.2 | 123646.6 | 99.25% | 99.84 | N/A |
| IBM X-Force Combined* | 4686 | 0 | 0.00% | 4922.2 | 119653.6 | 96.05% | 96.05 | N/A |
| IBM X-Force IP* | 4686 | 0 | 0.00% | 8051 | 116524.8 | 93.54% | 93.54 | N/A |
| IBM BL - URL* | 4686 | 0 | 0.00% | 41029.2 | 83546.6 | 67.06% | 67.06 | N/A |
*These products are partial solutions and their performance should not be compared with that of other products.
(Please refer to the text for full product names and details.)
| Newsletters | Malware | Phishing | Project Honey Pot | Abusix | STDev† | ||||||
| False positives | FP rate | False negatives | SC rate | False negatives | SC rate | False negatives | SC rate | False negatives | SC rate | ||
| Axway | 1 | 0.72% | 76 | 91.79% | 33 | 96.88% | 32 | 99.90% | 334 | 99.64% | 1.16 |
| Bitdefender | 0 | 0.00% | 32 | 96.54% | 25 | 97.64% | 2 | 99.99% | 150 | 99.84% | 0.26 |
| FortiMail | 0 | 0.00% | 49 | 94.71% | 74 | 93.01% | 3.2 | 99.99% | 359.4 | 99.61% | 0.58 |
| IBM | 0 | 0.00% | 22 | 97.62% | 26 | 97.54% | 14.4 | 99.95% | 264.4 | 99.72% | 0.66 |
| Libraesva | 0 | 0.00% | 1 | 99.89% | 6 | 99.43% | 3 | 99.99% | 67.4 | 99.93% | 0.59 |
| Spamhaus DQS | 0 | 0.00% | 29 | 96.87% | 171 | 83.85% | 134 | 99.58% | 1466.4 | 98.42% | 1.96 |
| ZEROSPAM | 1 | 0.72% | 66 | 92.87% | 7 | 99.34% | 7 | 99.98% | 381.2 | 99.59% | 0.93 |
| Abusix Mail Intelligence* | 0 | 0.00% | 267 | 71.17% | 54 | 94.90% | 440.6 | 98.61% | 488.6 | 99.47% | 1.03 |
| IBM X-Force Combined* | 0 | 0.00% | 225 | 75.70% | 187 | 82.34% | 276.8 | 99.13% | 4645.4 | 95.00% | 3.68 |
| IBM X-Force IP* | 0 | 0.00% | 307 | 66.85% | 233 | 78.00% | 441.4 | 98.61% | 7609.6 | 91.80% | 4.26 |
| IBM BL - URL* | 0 | 0.00% | 756 | 18.36% | 801 | 24.36% | 2284.6 | 92.81% | 38744.6 | 58.26% | 11.06 |
*These products are partial solutions and their performance should not be compared with that of other products. None of the queries to the IP blacklists included any information on the attachments; hence their performance on the malware corpus is added purely for information.
† The standard deviation of a product is calculated using the set of its hourly spam catch rates.
(Please refer to the text for full product names and details.)
| Speed | ||||
| 10% | 50% | 95% | 98% | |
| Axway | ||||
| Bitdefender | ||||
| FortiMail | ||||
| IBM | ||||
| Libraesva | ||||
| Spamhaus DQS | ||||
| ZEROSPAM | ||||
(Please refer to the text for full product names and details.)
| 0-30 seconds | 30 seconds to two minutes | two minutes to 10 minutes | more than 10 minutes |
| Products ranked by final score | ||
| Bitdefender | 99.88 | |
| Libraesva | 99.84 | |
| IBM | 99.78 | |
| FortiMail | 99.71 | |
| Axway | 99.68 | |
| ZEROSPAM | 99.35 | |
| Spamhaus DQS | 98.72 | |
(Please refer to the text for full product names and details.)
| Hosted solutions | Anti-malware | IPv6 | DKIM | SPF | DMARC | Multiple MX-records | Multiple locations |
| ZEROSPAM | ClamAV | √ | √ | √ | √ | √ |
(Please refer to the text for full product names and details.)
| Local solutions | Anti-malware | IPv6 | DKIM | SPF | DMARC | Interface | |||
| CLI | GUI | Web GUI | API | ||||||
| Axway | Kaspersky, McAfee | √ | √ | √ | √ | ||||
| Bitdefender | Bitdefender | √ | √ | √ | √ | ||||
| FortiMail | Fortinet | √ | √ | √ | √ | √ | √ | √ | |
| IBM | Sophos; IBM Remote Malware Detection | √ | √ | √ | |||||
| Libraesva | ClamAV; others optional | √ | √ | √ | √ | ||||
| Spamhaus DQS | Optional | √ | √ | √ | √ | ||||
(Please refer to the text for full product names and details.)
 (Please refer to the text for full product names and details.)
(Please refer to the text for full product names and details.)
The full VBSpam test methodology can be found at https://www.virusbulletin.com/testing/vbspam/vbspam-methodology/vbspam-methodology-ver20.
The test ran for 16 days, from 12am on 8 August to 12am on 24 August 2020.
The test corpus consisted of 129,515 emails. 124,691 of these were spam, 31,775 of which were provided by Project Honey Pot, with the remaining 92,916 spam emails provided by Abusix. There were 4,686 legitimate emails (‘ham’) and 138 newsletters, a category that includes various kinds of commercial and non-commercial opt-in mailings.
144 emails in the spam corpus were considered ‘unwanted’ (see the June 2018 report4) and were included with a weight of 0.2; this explains the non-integer numbers in some of the tables.
Moreover, 926 emails from the spam corpus were found to contain a malicious attachment while 1,059 contained a link to a phishing or malware site; though we report separate performance metrics on these corpora, it should be noted that these emails were also counted as part of the spam corpus.
Emails were sent to the products in real time and in parallel. Though products received the email from a fixed IP address, all products had been set up to read the original sender’s IP address as well as the EHLO/HELO domain sent during the SMTP transaction, either from the email headers or through an optional XCLIENT SMTP command5.
For those products running in our lab, we all ran them as virtual machines on a VMware ESXi cluster. As different products have different hardware requirements – not to mention those running on their own hardware, or those running in the cloud – there is little point comparing the memory, processing power or hardware the products were provided with; we followed the developers’ requirements and note that the amount of email we receive is representative of that received by a small organization.
Although we stress that different customers have different needs and priorities, and thus different preferences when it comes to the ideal ratio of false positives to false negatives, we created a one-dimensional 'final score' to compare products. This is defined as the spam catch (SC) rate minus five times the weighted false positive (WFP) rate. The WFP rate is defined as the false positive rate of the ham and newsletter corpora taken together, with emails from the latter corpus having a weight of 0.2:
WFP rate = (#false positives + 0.2 * min(#newsletter false positives , 0.2 * #newsletters)) / (#ham + 0.2 * #newsletters)
while in the spam catch rate (SC), emails considered ‘unwanted’ (see above) are included with a weight of 0.2.
The final score is then defined as:
Final score = SC - (5 x WFP)
In addition, for each product, we measure how long it takes to deliver emails from the ham corpus (excluding false positives) and, after ordering these emails by this time, we colour-code the emails at the 10th, 50th, 95th and 98th percentiles:
| (green) = up to 30 seconds | |
| (yellow) = 30 seconds to two minutes | |
| (orange) = two to ten minutes | |
| (red) = more than ten minutes |
Products earn VBSpam certification if the value of the final score is at least 98 and the ‘delivery speed colours’ at 10 and 50 per cent are green or yellow and that at 95 per cent is green, yellow or orange.
Meanwhile, products that combine a spam catch rate of 99.5% or higher with a lack of false positives, no more than 2.5% false positives among the newsletters and ‘delivery speed colours’ of green at 10 and 50 per cent and green or yellow at 95 and 98 per cent earn a VBSpam+ award.
1 Spamhaus DQS is a custom solution built on top of the SpamAssassin open-source anti-spam platform.
2 This analysis is not intended to be exhaustive research on these samples but rather a short review of the most commonly missed malware and phishing emails in the test.
3 https://twitter.com/malware_traffic/status/1296480451301912577.
4 https://www.virusbulletin.com/virusbulletin/2018/06/vbspam-comparative-review.