Posted by on Aug 10, 2017
With an excellent conference programme featuring some of the top experts in the IT security industry and covering some of the most important topics, we have much to look forward to when it comes to VB2017, the 27th Virus Bulletin conference. But we also often look back at past conference presentations, not just because we are proud to have had them presented at our conference, but because their content is still very relevant today.
In the second of a two-part blog series (part 1 here), I look back at ten memorable Virus Bulletin Conference presentations from the last decade.

With more than two decades' worth of experience testing security products, the subject of testing is one that is dear to our hearts at Virus Bulletin, and one that regularly appears on the conference programme. One paper on testing that particularly stands out for me is that of École Polytechnique de Montréal researchers Fanny Lalonde Lévesque, Carlton R. Davis and José M. Fernandez, presented by the latter at VB2012 in Dallas.
In the paper, the researchers described what must have been the most realistic anti-virus test ever: a study that looked at real people, using their own machines, to gauge the effectiveness of the products being tested. Though unfortunately this methodology scales very badly – which means it has never been used in a real test – I find it useful to keep it at the back of my mind when working on VB's tests, as it does set some kind of gold standard.
Although the VB2013 last-minute paper from Google's Adrian Ludwig covered much more than statistics on Android malware, this is the part that was picked up by the press: there is barely any malware on Android. It was also the part that led to strong criticism from the audience in Berlin.
Adrian was right: only a very small percentage of Android apps are malicious, especially if you only look at apps downloadable through Google's official Play Store. But the problem isn't non-existent, and these days Google is ready to admit that. Last year at VB2016, members of the Android team delivered a Small Talk on Android malware and on how they can work with the security community to fight this threat, while at the most recent Black Hat conference, Google researchers themselves revealed a very targeted malware campaign targeting Android.
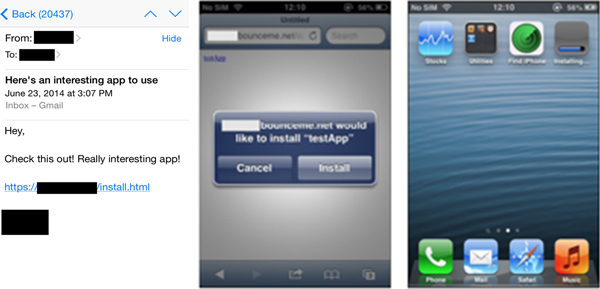
Let's be honest: because iOS malware is so rare, talks on possible attack vectors against the operating system always have a certain 'coolness' factor. But the paper presented by Tao Wei and his FireEye colleagues at VB2014 in Seattle didn't just describe a theoretical attack: the use of enterprise provisioning profiles to distribute malicious apps was observed shortly after the conference in the Wirelurker malware.
When I joined VB a decade ago, the security industry was making the shift from fighting malware written by the proverbial kid in their parents' basement to tools written by professional criminals with a clear financial motive. Although (cyber)criminals remain a prominent adversary, the rise of state-sponsored attacks has turned many a security researcher into an intelligence broker.
This shift was discussed in a thought-provoking paper presented at VB2015 in Prague by Juan Andrés Guerrero-Saade who, as part of Kaspersky's GReAT team, has played an active role in the uncovering of many state-sponsored attacks.
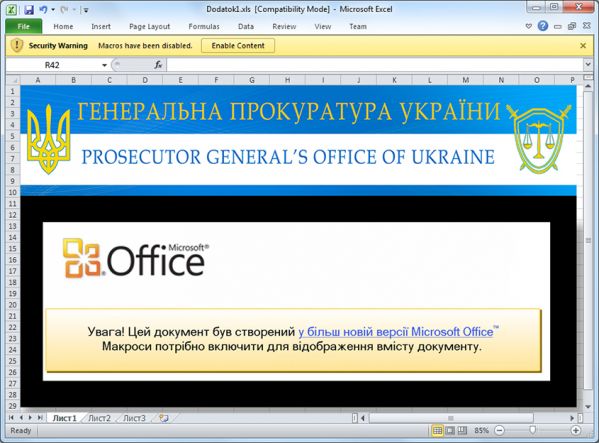
One very prominent state-sponsored attack group is that behind the BlackEnergy malware family, which became well known for causing massive power outages in Ukraine in December 2015. ESET researchers Robert Lipovsky and Anton Cherepanov have been following BlackEnergy for a number of years now, and have spoken about it at various Virus Bulletin conferences, most recently last year at VB2016 in Denver.
No doubt, several of the talks on the VB2017 programme will prove to be just as memorable when we look back in a few years' time. There are still 10 last-minute speaker slots left to fill, so submit your hot research for a chance to present it in Madrid (deadline 3 September 20017).