Posted by Virus Bulletin on Mar 20, 2020
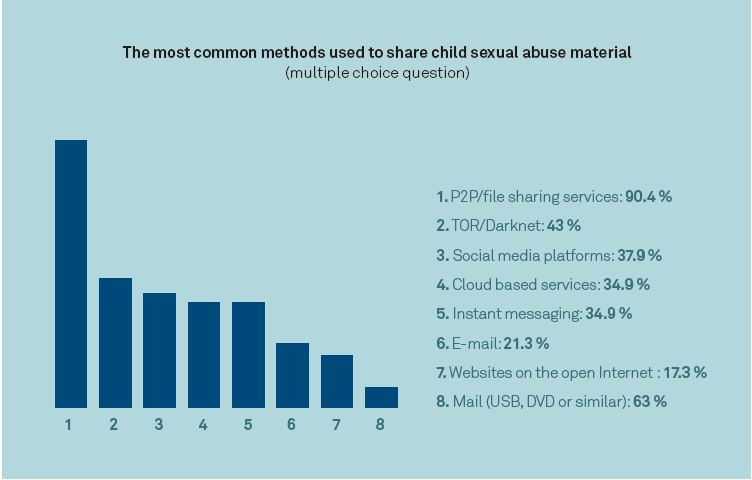 Often unbeknownst to network administrators, many company networks are used to download child sexual abuse material. In a paper presented at VB2019 in London, NetClean’s Richard Matti and Anna Creutz looked at this problem and what companies can do, ultimately, to help safeguard children. Today we publish their full paper.
Often unbeknownst to network administrators, many company networks are used to download child sexual abuse material. In a paper presented at VB2019 in London, NetClean’s Richard Matti and Anna Creutz looked at this problem and what companies can do, ultimately, to help safeguard children. Today we publish their full paper.
Posted by Virus Bulletin on Mar 16, 2020
 Here at VB we are keeping a close eye on the global situation regarding the COVID-19 outbreak and the various travel restrictions and health advice, but in the meantime planning and arrangements for VB2020 are going ahead as usual, including the selection of papers.
Here at VB we are keeping a close eye on the global situation regarding the COVID-19 outbreak and the various travel restrictions and health advice, but in the meantime planning and arrangements for VB2020 are going ahead as usual, including the selection of papers.
Posted by Virus Bulletin on Mar 13, 2020
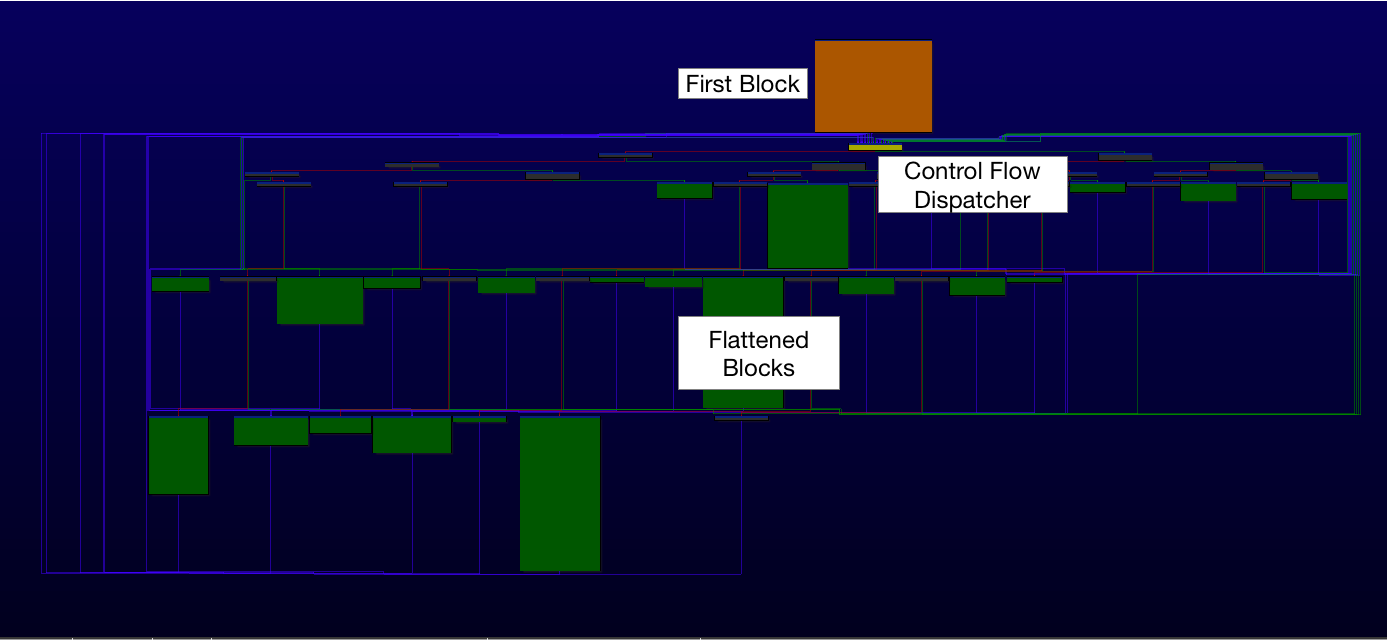 At VB2019 in London, Carbon Black researcher Takahiro Haruyama presented a paper on defeating compiler-level obfuscations used by the APT10 group. Today we publish both Takahiro's paper and the recording of his presentation.
At VB2019 in London, Carbon Black researcher Takahiro Haruyama presented a paper on defeating compiler-level obfuscations used by the APT10 group. Today we publish both Takahiro's paper and the recording of his presentation.
Posted by Virus Bulletin on Mar 12, 2020
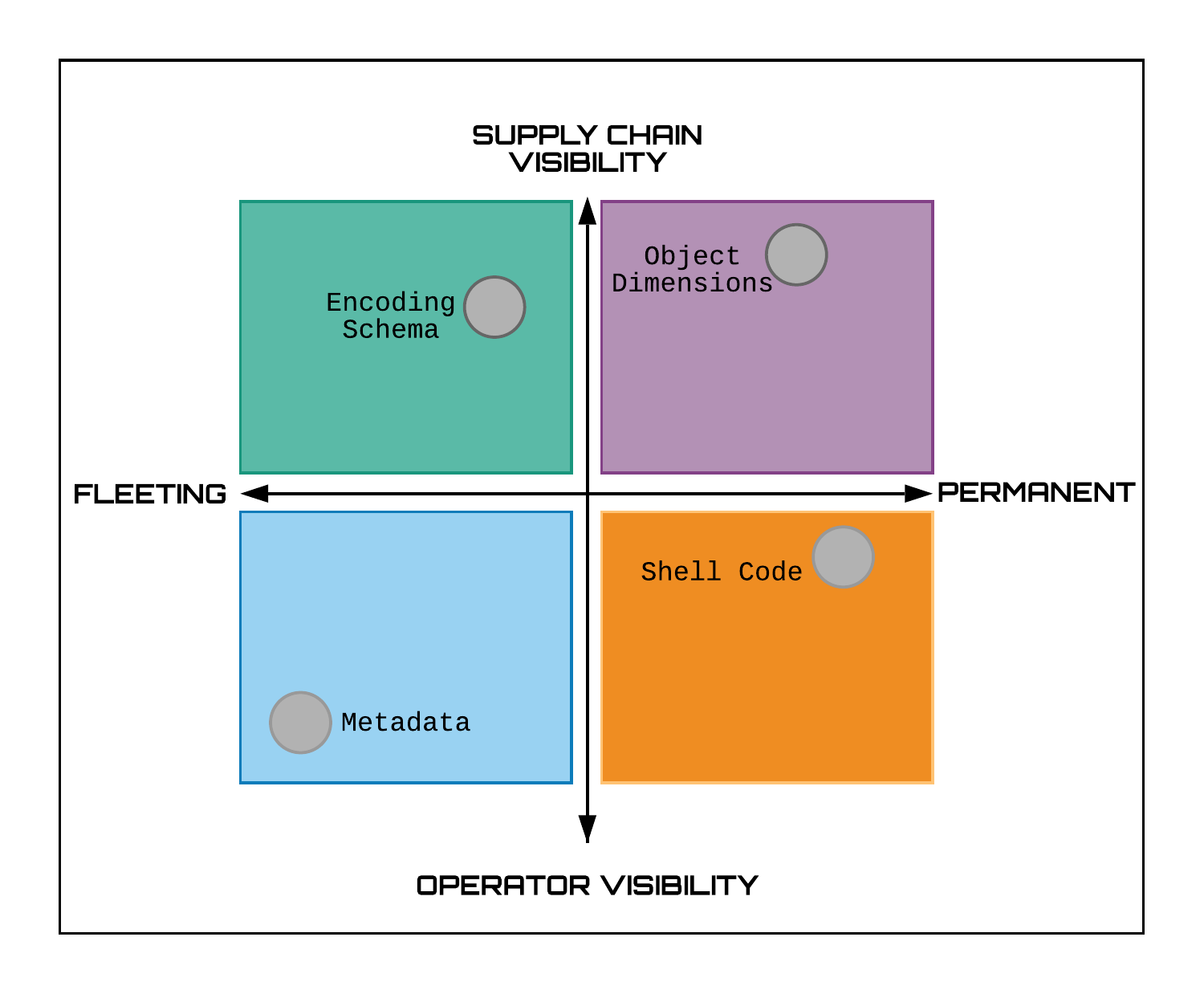 At VB2019 in London Michael Raggi (Proofpoint) and Ghareeb Saad (Anomali) presented a paper on the 'Royal Road' exploit builder (or weaponizer) and how the properties of RTF files can be used to track weaponizers and their users. Today we publish both their paper and the recording of their presentation.
At VB2019 in London Michael Raggi (Proofpoint) and Ghareeb Saad (Anomali) presented a paper on the 'Royal Road' exploit builder (or weaponizer) and how the properties of RTF files can be used to track weaponizers and their users. Today we publish both their paper and the recording of their presentation.
Posted by Virus Bulletin on Mar 11, 2020
 Operational technology, the mission critical IT in ICS, shares many similarities with traditional IT systems, but also some crucial differences. During the Threat Intelligence Practitioners’ Summit at VB2019, Dragos cyber threat intelligence analyst Selena Larson gave a keynote on these similarities and differences. Today we release the recording of her presentation.
Operational technology, the mission critical IT in ICS, shares many similarities with traditional IT systems, but also some crucial differences. During the Threat Intelligence Practitioners’ Summit at VB2019, Dragos cyber threat intelligence analyst Selena Larson gave a keynote on these similarities and differences. Today we release the recording of her presentation.
Posted by Virus Bulletin on Mar 10, 2020
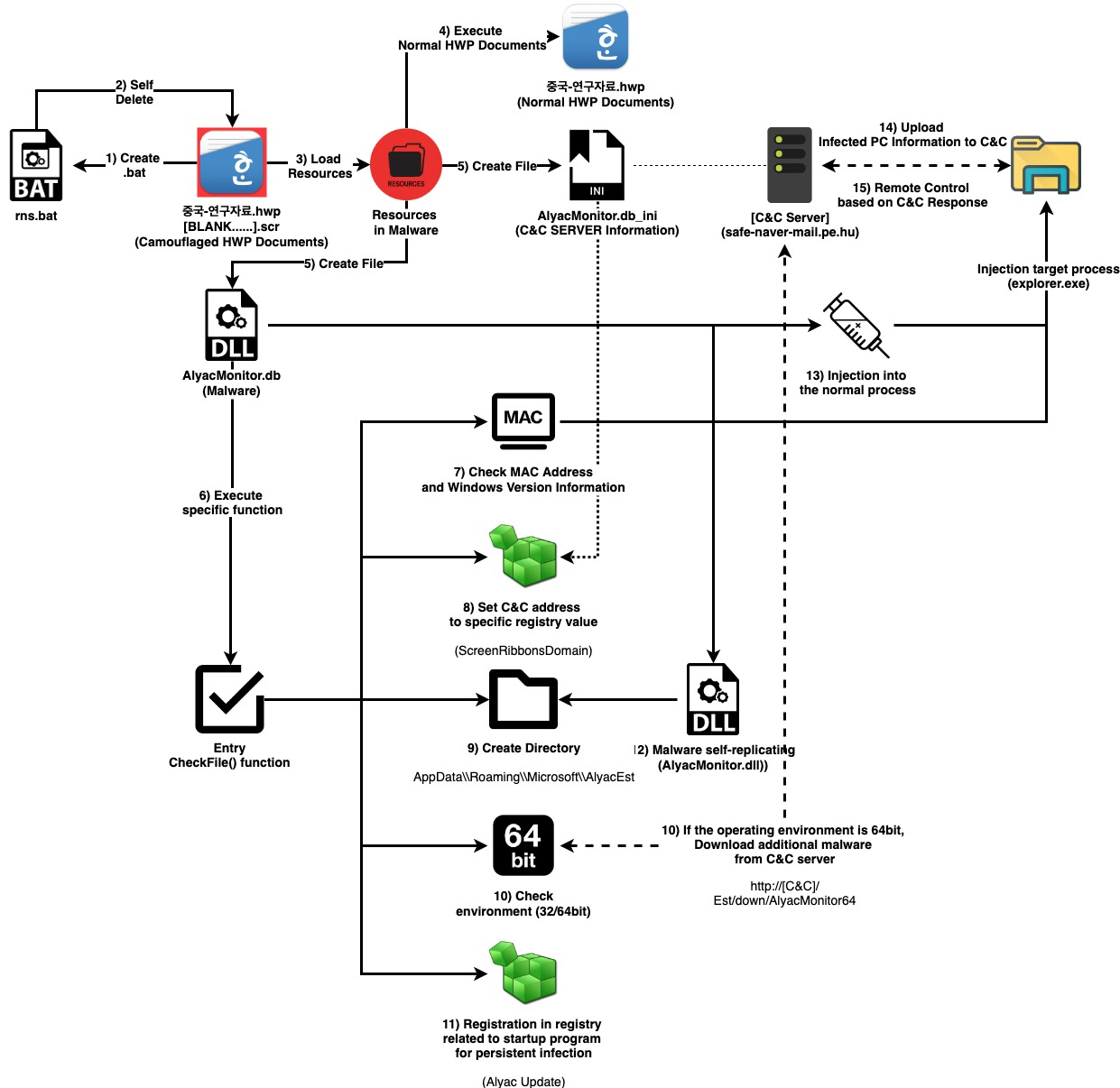 In a paper presented at VB2019 in London, researchers fron the Financial Security Institute detailed the tools and activities used by the APT group 'Kimsuky', some of which they were able to analyse through OpSec failures by the group. Today, we publish their paper.
In a paper presented at VB2019 in London, researchers fron the Financial Security Institute detailed the tools and activities used by the APT group 'Kimsuky', some of which they were able to analyse through OpSec failures by the group. Today, we publish their paper.
Posted by Virus Bulletin on Mar 9, 2020
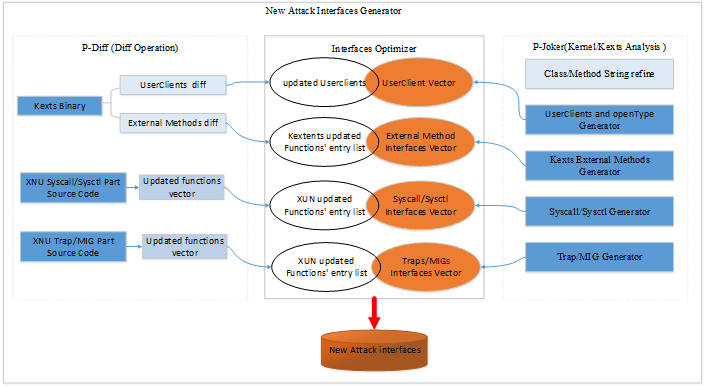 In a paper presented at VB2019 in London, Trend Micro researchers Lilang Wu and Moony Li explained how the hunt for vulnerabilities in MacOS and iOS operating systems can be made both smarter and more automatic. Today we publish both their paper and the recording of their presentation.
In a paper presented at VB2019 in London, Trend Micro researchers Lilang Wu and Moony Li explained how the hunt for vulnerabilities in MacOS and iOS operating systems can be made both smarter and more automatic. Today we publish both their paper and the recording of their presentation.
Posted by Virus Bulletin on Mar 6, 2020
 In a last-minute paper presented at VB2019 in London, Rintaro Koike (NTT Security) and Yosuke Chubachi (Active Defense Institute, Ltd) discussed the platform they have built to automatically detect and analyse exploit kits. Today we publish the recording of their presentation.
In a last-minute paper presented at VB2019 in London, Rintaro Koike (NTT Security) and Yosuke Chubachi (Active Defense Institute, Ltd) discussed the platform they have built to automatically detect and analyse exploit kits. Today we publish the recording of their presentation.
Posted by Virus Bulletin on Feb 28, 2020
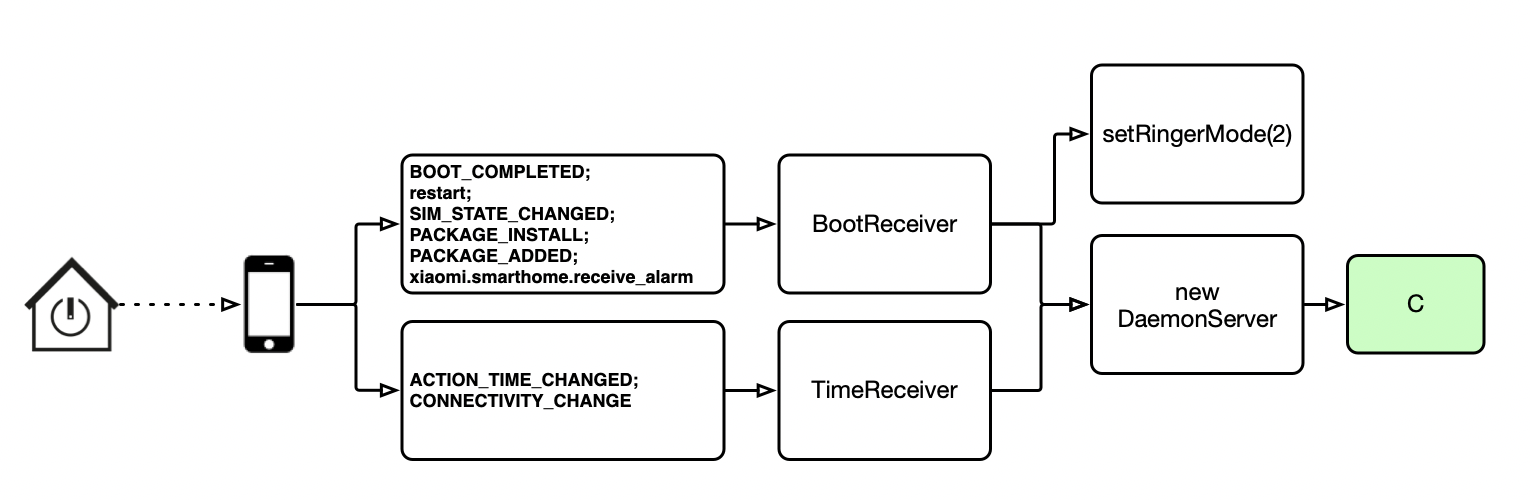 The activities of China-based threat actor PKPLUG were detailed in a VB2019 paper by Palo Alto Networks researcher Alex Hinchliffe, who described the playbook of this long-standing adversary. Today we publish both Alex's paper and the recording of his presentation.
The activities of China-based threat actor PKPLUG were detailed in a VB2019 paper by Palo Alto Networks researcher Alex Hinchliffe, who described the playbook of this long-standing adversary. Today we publish both Alex's paper and the recording of his presentation.
Posted by Virus Bulletin on Feb 25, 2020
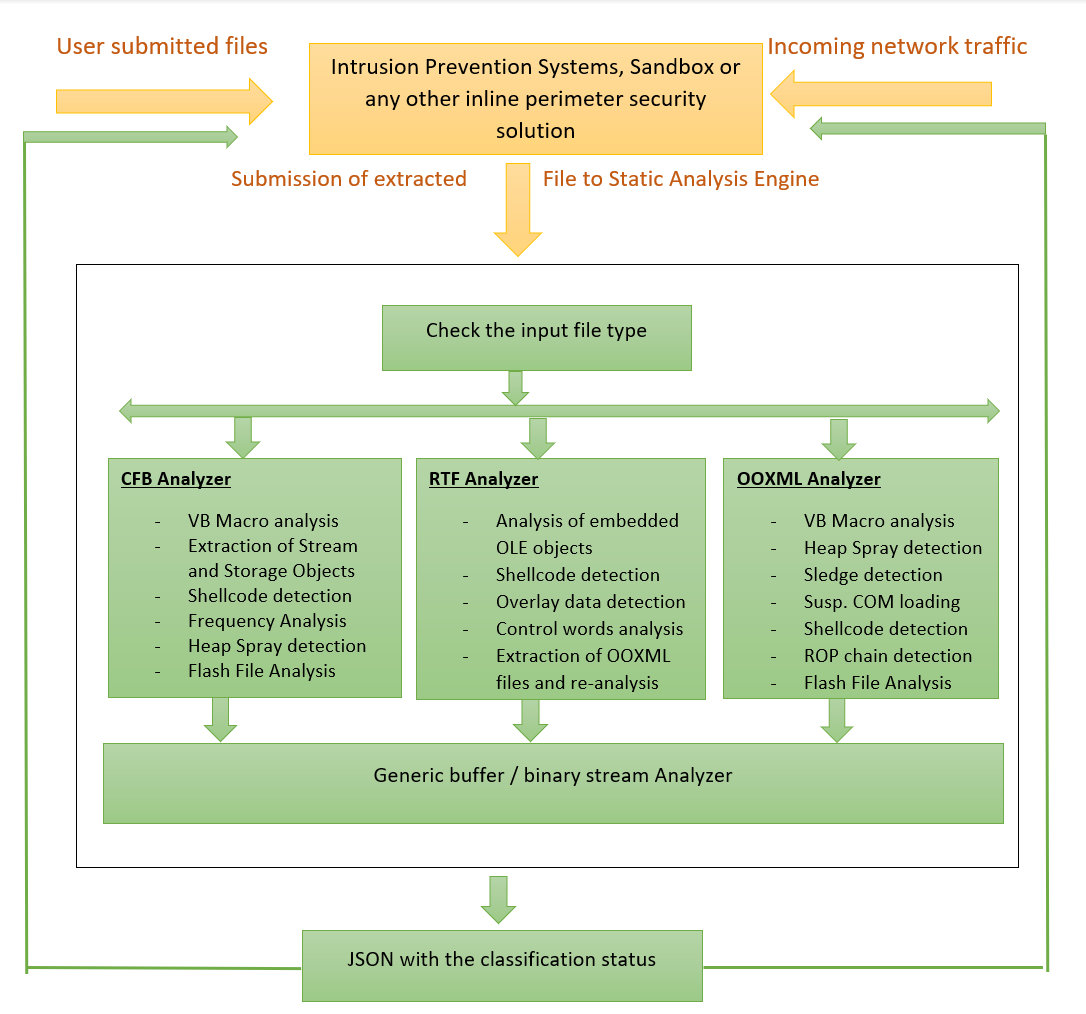 Today we publish the VB2019 paper and presentation by McAfee researcher Chintan Shah in which he described static analysis methods for the detection of Microsoft Office exploits.
Today we publish the VB2019 paper and presentation by McAfee researcher Chintan Shah in which he described static analysis methods for the detection of Microsoft Office exploits.