2007-09-01
Abstract
John Hawes takes an in-depth look at BitDefender's latest home-user offering, BitDefender Total Security 2008.
Copyright © 2007 Virus Bulletin
Despite being a fairly young company, BitDefender – set up in Bucharest, Romania by its parent Softwin as recently as 2001 – has already established itself as an important player in the security market. Taking over Softwin’s AntiVirus eXpert (AVX) technology, BitDefender has expanded its range of offerings to include home-user and corporate solutions, desktop, server and gateway products, and support for Linux and FreeBSD. These products have been promoted vigorously and effectively, pushing the technology and the brand into the public consciousness. The company has expanded from its Romanian base to set up branch offices in France, Spain and the USA. With strong brand recognition and a reputation for solid, dependable detection rates and impressive heuristics, the company has become one of the most trusted names amongst mid-sized security firms.
BitDefender’s products have been regular participants in VB’s comparative reviews since the AVX days, and after a slow start soon found their stride – first achieving VB100 certification in 2003 and failing only once since, when stability issues in a tricky Linux test got the better of the product in 2004. The product’s appearance in our tests has been less dependable of late, having skipped both Vista comparatives this year, but BitDefender’s record remains strong. Its products are also certified by the standard bodies ICSA Labs and West Coast Labs, and highly rated by test centres such as AV-Comparatives, where they regularly score ‘Advanced’ and ‘Advanced+’ ratings – particularly in retrospective tests looking at proactive detection of new threats – and AV-Test, where the BitDefender name is common among the top five ranked products.
BitDefender Total Security 2008 (TS2008) is the latest version of the company’s home-user product, released shortly before the publication of this review. It focuses strongly on the needs of the home user, and the interface – previously criticised for being a little technical and daunting – has been redesigned and simplified with the inexpert user in mind.
The full suite covers a wide range of security issues, with standard anti-malware, firewall and anti-spam functionalities augmented with backup facilities, system tune-up, phishing protection and more. A pared-down sister suite, BitDefender Internet Security 2008, is also available, offering everything apart from the backup and tune-up facilities, and a pure anti-malware product completes the range. The product supports Windows XP and Vista, 32-bit and 64-bit, and is available in English, French, German and Spanish, with more languages including Japanese due to be added by the end of the year.
The main home of BitDefender on the web, www.bitdefender.com, is a fairly slick and attractive place, with a fixed width design which leaves wide swathes of greyish-white space in the browser. The company’s trademark red, black and steely grey colour scheme looks glossy and elegant without the cutesy cartoonish look which has become popular on many security sites lately.
The first link on the navigation bar leads to information about the company itself, revealing that its slogan is ‘Securing your every bit’ and that it is justly proud of having won the PC World ‘#1 Best Buy’ title in March 2006. The company goal is to become one of the top six AV solutions by 2010, and a quick glance through its history shows steady progress in this direction. The company’s technological history is even more impressive, boasting firsts in web and messaging scanning, automated updating, behavioural technologies, and bundling firewalls with AV products. Further information on the technology provides detailed overviews of its capabilities and is aimed at potential partners – of whom there are already many, the BitDefender engine being one of the most popular for inclusion in multi-engine offerings.
Curiously, the VB logo is missing from the otherwise rather crowded awards page – an oversight which I’m sure will soon be corrected. Further information for would-be partners and information on the product range is also available, as is an online shop and a download area providing evaluation versions, removal tools and updates. A free version of the home-user AV product is available, and the Linux scanner is also free to download.
Of most interest to me on the site, however, were the sections labelled ‘Support’ and ‘Defense Center’. The latter area contains a malware encyclopaedia, which is not the most exhaustive I have seen, with entries numbering in the hundreds rather than the tens of thousands that would be needed to cover the ever-expanding range of nasties out there. The encyclopaedia also suffers from a rather defective search system – common terms such as ‘mytob’, ‘netsky’ and ‘bagle’ returned ‘no documents’, despite most of them being easy to find with a little browsing. However, when an individual item of malware is picked out of the encyclopaedia, the information provided goes into great depth, and is put across with admirable clarity.
A set of free-to-download removal tools is also provided, covering a lengthy list of common infections, along with an online scanner, which boasts of being a ‘fully functional antivirus product’, offering full system and registry scanning and disinfection. Like so many of these offerings, it requires Internet Explorer to work, using ActiveX controls to access the system.
A news section, backed up by various email alert options, provides the latest stories on major malware outbreaks and developments, along with technological advances in BitDefender’s products. ‘Real-time’ malware statistics are also offered, drawing on feedback from products in use across the world – these can be divided into desktop and gateway figures, display numbers of files or systems infected, and can be tweaked to show smaller or larger time periods, providing some interesting insight into what is hitting users hardest at any given time. Finally, an advice page offers ‘Ten Commandments for Your Computer Sanity’, a nice simple set of rules setting out the basics of safe computing.
In the Support section, the visitor is first guided towards information for the relevant type of user (home, small business or corporate) and the relevant product. Links are then provided to downloads, a rather limited knowledgebase (the TS2008 section contained only an explanation for the ‘I/O errors’ entry in log files), a ‘documentations’ section, (which had I assumed would provide manuals but the linked PDFs were in fact rather simple datasheets), and support contact details. Unlimited 24/7 support is provided with the TS2008 licence, and advice can be sought by phone, via email or via an online chat system.
This part of the site, like several others, is adorned with customer recommendations, the most impressive of which is from a Mr David Perry, who apparently was so pleased with his BitDefender purchase that he threw his popular rival product ‘on the burn pile and watched it melt’.
Installation of the system follows a pretty standard path. After an initial, rather lengthy period of extracting files, there came the usual EULAs, warnings about removing other security products, and a message promising ‘expert protection’ and boasting of the product’s certification by VB and others, before the installation proper began. During this process, a licence key can be entered (although an evaluation period is also available, which seems not to limit the functionality of the product), a user login for the BitDefender site can be set up, and the product runs an update and a scan of the local system to ensure it is clean before installing. After the initial extraction period, the process is speedy and keeps the questions to a minimum, allowing novice users to run through it without anything tricky to worry about.
The interface is a pretty simple thing, modelled somewhat along the lines of the Windows Security Center – just four big, fat icons, representing the four main areas of the product, show the status of the parental controls, the security provision, the backup and the tune-up facilities. In my case all but the security icon started off with a big grey cross through them to indicate that they had yet to be configured. The security icon was marked with a red exclamation mark – a warning that the product had yet to update. A red button to one side of the icons offers the chance to ‘Fix all issues’, while along the bottom some tabs provide various tasks for each area.
Clicking this, or any of the chunky buttons for the individual areas, brings up a list of the various items considered to be vital to the security of the system. Those which have yet to be configured or run, or which have encountered some trouble, are marked with a red ‘Fix’ link. This brings up the appropriate scan, config page or wizard, while the ‘Fix all’ links bring these up in chains, moving on to the next as each one completes.
The bottom of the page lists some ‘quick tasks’, divided into tabs for the different modules. The security tab, displayed by default, offers updating and a series of scans. The scan options were ‘Documents’, which does a quick check of the registry, the 'My Documents' folder and files on the desktop; a ‘Full system scan’; and a ‘Deep system scan’. Both the 'Full system scan' and the 'Deep system scan' apparently scan all local drives, the difference being that the ‘Full’ scan doesn’t include archives, while the ‘Deep’ one does.
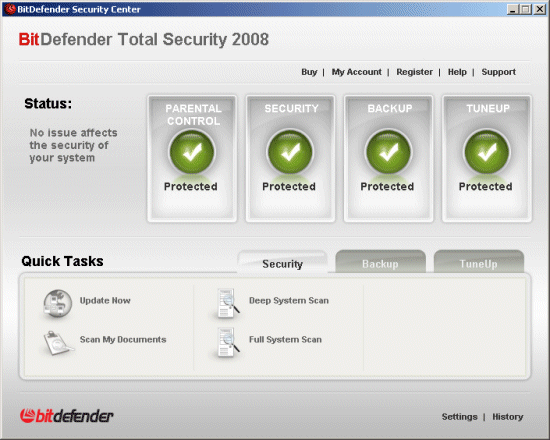
The ‘Backup’ tab within this area offers access to the backup and restore wizards, the first of which is activated by the ‘Fix’ buttons mentioned earlier – this presents lists of items that can be backed up, and a place to store them, while the restore system does the same in reverse. There is also a full backup utility linked from here, which opens a new window containing some in-depth controls for managing backups. The ‘Tuneup’ tab offers the same series of wizards provided earlier by the ‘Fix’ buttons, which can be run again as often as the user requires – disk defragmenting, removal of unwanted data and registry cleaning can all be run through via more, fairly straightforward wizards.
Leaving these for later, I ran through a couple of the malware scan jobs, which zipped along in quite good time even when scanning a whole system. My concerns that there would be no way of tuning or tweaking this side of the product were soon allayed when I spotted a small button in the bottom corner of the main GUI marked ‘Settings’. This opened a new window, less glossy than the main interface or the wizards, which proved to be an in-depth and fully featured configuration area, with options to set up, schedule and run scans, tweak the settings of the on-access monitor, and also to control the other aspects not covered by the simplistic main GUI – the firewall, spam-filtering, and parental and privacy controls.
Much of this area is not merely less glossy, but perhaps inevitably less accessible to the non-technical user, presenting quite a lot of fairly serious data with little by way of explanation. However, the front page for each sub-section presents a slider with which the security settings can quickly and simply be changed from a default in the middle to the highest or laxest security levels, with some statistics on activities carried out (files or mails processed, web connection activity etc.) – in some cases in the form of nice little real-time graphs. The real nitty gritty of the configuration is then accessed via tabs, the setup thus providing the inexpert user with a way of adjusting the settings without the need for too much research, while the more skilled (or foolhardy) can delve into the depths of configuration as they please.
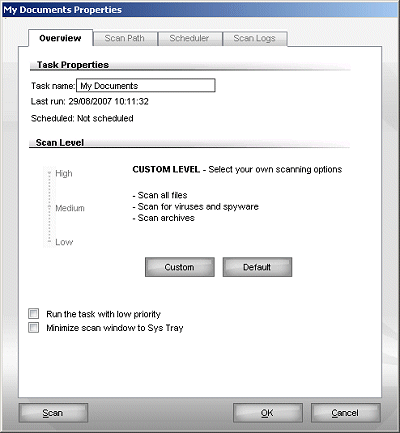
For novices who do need to make more involved changes to the configuration, and even those simply running through the wizards, something that is conspicuous by its absence is help. I mentioned earlier that the website offered little by way of documentation, and no full manual was provided (at least with the download version tested here). A help file is available, but can only be accessed from a link on the front page of the main interface. Further tips, advice, clarification and so on would make a handy addition to some of the more difficult or important areas, and at the very least links to the appropriate pages of the help system should be considered.
The help itself seems reasonably comprehensive, although in some places the language or layout is a little awkward. There are a lot of very long pages, with whole chapters stored in a single lot (although broken up for the links in the contents tab) and many very large screenshots, which necessitate some sideways scrolling, even at fairly high resolutions.
The help focuses mainly on running through the steps required by each task, but each section also has a brief explanation of the reason for the functionality and advice on how and when to use it. These are mostly just brief introductions to each section, but in the ‘advanced’ chapters a series of ‘insights’ give a nice broad overview of the problems solved by each individual component, presented in a pleasantly user-friendly manner.
With the interface thoroughly explored, I moved on to some basic tests of the product’s malware detection. Malware scanning can be achieved in numerous ways: using the big ‘deep’ and ‘full’ buttons on the main interface, using a context-menu option, dragging files to the little semi-transparent status box, or simply trying to open something and seeing if the monitor finds anything suspicious there. They all seem to run pretty smoothly, and with some good stability. Several attempts to overwhelm the program – by running several processes opening hundreds of infected samples in quick succession while a manual scan chugged along over some more samples, and still more piled in over the network – failed to bring the thing to its knees or let anything slip past it, although some slight slowdown in the system was inevitable.
Running scans over the standard VB test sets produced unsurprising results – BitDefender has always had excellent detection rates in VB100 tests, and the few samples usually missed are all rather obscure and elderly (and even these are, apparently, being worked on by diligent lab staff). Even the very latest batches of samples available failed to defeat the scanner, or its heuristics, which flagged just about everything thrown at it in some style. A couple of items not spotted by the scanner were quickly picked up as they tried to install themselves in the registry and drop things into system folders.
Cleanup was also pretty solid – the default settings on access are to disinfect or remove malicious files, and this was done without difficulty on the few items tested. Unfortunately the product was only on the VB test bench for a few days, and little time was available for in-depth testing of the behaviour-blocking, heuristics and removal prowess of the product, but we hope to be able to introduce more regular testing of these aspects of products in the future, and I expect to see BitDefender well up in the rankings.
Scanning speeds were pretty good throughout, perhaps making some slight improvement over times recorded in earlier VB100 testing, though as both the systems and the test sets have been altered several times in recent months no direct comparison can be made. On-access speeds seemed particularly impressive, and I rarely noticed any slowdown on more up-to-date systems – some older machines did suffer a little under the weight, especially when the interface was running, lagging for several seconds between screens and so on, but in this day and age few people will be using such tired old hardware.
Of course, the malware scanning provided under the ‘Security’ tab is far from everything the product has to offer. Also covered by general security, and configured from the advanced settings area, are a range of items including the firewall, anti-spam, and privacy and parental controls.
The firewall page starts off fairly simply, with a status indicator and a nice plain slider to tweak its strictness. In normal modes, the firewall seems to offer a sensible level of protection from the off, automatically including a well populated whitelist of trusted software which seems to include most standard items without pestering the user too much. Adding new rules for connections is a straightforward task, again with further configuration available on an ‘advanced’ tab. The whitelist can also be bypassed easily, using the slider to set security to a higher level, and a handy button allows instant blocking of all traffic.
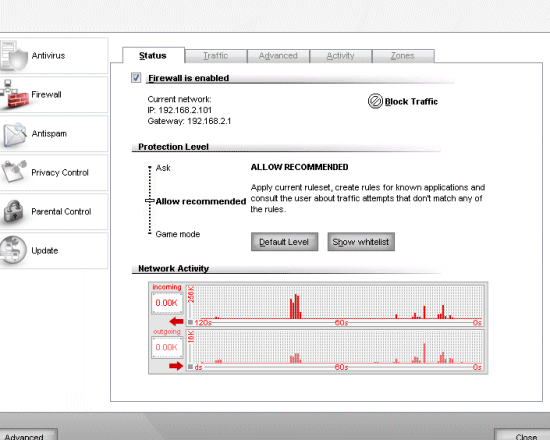
A graph of traffic on the main page is supplemented by a nice table of activity on a separate tab, showing all connected processes, the ports they are using and the traffic passing through them. Another sensible idea is to class unsecured wireless connections automatically as untrusted – a warning pops up when trying to connect to an unsecured router, informing the user that such connections can be used by adding a rule, but suggesting that securing the connection point would be a smarter move.
The firewall also offers ‘Game mode’, which shuts off messaging and updating to minimize impact on the system or user during game sessions, and relaxes the connection rules to block only those actions which have specific rules defining them. This is ‘strongly discouraged’, according to the manual, though there is little such discouragement in the product itself. It does at least allow gamers – especially experienced firewall tweakers – to implement some level of protection without impacting too much on their fun.
The anti-spam module integrates with a range of mail readers, providing a nice little toolbar with which to manage messages and contacts, with mails easily marked as coming from friends or annoyances, and other addresses likewise. Addresses are imported via a simple wizard, and a little training system can be pointed at existing folders of good or spam mail to get an idea of what kind of a mail user you are (I was confused for a moment when it asked me to ‘select witch folder’ – I thought maybe this was an unusual term for a list of known bad folk, but later decided it must be a typo). The system can also be set to drop messages in Asian or Cyrillic character sets automatically, and to use heuristic filtering techniques to improve performance.
The next section, labelled ‘Privacy control’, is a bit of a mixed bag. The first part lets the user store a selection of important data – addresses, telephone, bank account and credit card numbers etc. – which are then watched for and, if the information is spotted leaving via the web or email, the action is blocked. This kind of system always makes me feel a little uncomfortable, but the data is apparently kept well encrypted and the blocking seems effective. A whitelist of sites that are allowed to receive such data can be created. There is also a phishing filter provided, with its own little toolbar added to IE, which watches for suspicious sites and again allows the creation of a user-defined whitelist.
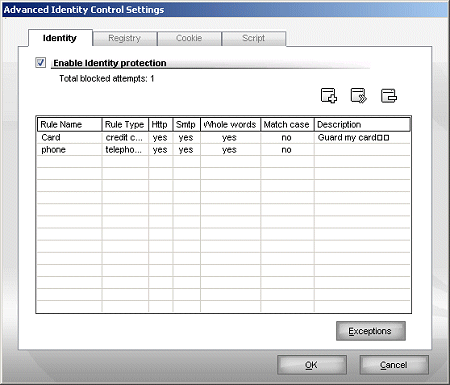
A registry monitor blocks unauthorised changes to the system’s startup list and other settings, while cookie and script blockers control which sites can and cannot drop cookies and run active content, again using sets of allow/deny rules. Finally, there is a system info tab providing lots of information about the local system, including startup items, browser components and helper objects, active processes and their imports, and much more besides. Only minimal explanation is provided here, and this would only be of much use to users with considerable insight into their systems.
Parental controls are a more straightforward area – unlike many such things, there is no long list of areas which should be filtered, just per-user settings for children, teenagers and adults (the teens are allowed access to drugs and hacking-related content, but not gaming, according to the on-screen summary). Additional filtering is available for URLs and keywords, and a time-control mechanism completes the set of parental controls.
The product ensures it lives up to the ‘Total’ part of its name with yet more functionality – the backup and system maintenance features. Such items are becoming increasingly common in security suites, with several major products rolling in some level of backup or cleaning alongside more traditional security measures. Here, they are kept somewhat separate from the security area, being assigned two of the four fat buttons on the main console.
The backup feature provides a simple wizard with which incremental or full backups of ranges of files and data can be run to local drives, across networks or to removable devices. This seemed fairly straightforward, and another fat button in the ‘quick tasks’ tray also allows for speedy restoration of the backed-up data. Another link leads to a much more in-depth interface, where these backups can be configured in more detail, including compressing and encrypting the backup targets and a vast range of other options. There are facilities for viewing logs of progress and errors monitored, and even a CD-burning system to create permanent backups.
The final part of the product is the ‘Tuneup’ section. This again provides a range of options, although this time they appear only to be manipulable from the main interface and are somewhat less mature than the rest of the offerings. ‘Defragmentation’ has a very basic wizard, just offering a list of available drives, and it seems to check drives to see if defragging would be of any benefit, but then has a go at tidying up even when it has informed the user that it is unnecessary. It certainly spends quite some time processing all drives, even when the same process has been run just moments earlier. An Internet file removal tool is next – this is pretty straightforward too, with no options at all: you start it, and it removes temporary files and cookies. Both tools seem a little pointless, as such functionality is already readily available, but I suppose having it all in one place is handy for some.
Less common is the file shredder, which trashes deleted files securely using the US Department of Defense method – which is generally considered fairly solid, although is not quite as fanatically thorough as methods offered by another product reviewed here recently (see VB, March 2007, p.13). It’s simple to use – just point it at a file or folder and click ‘go’ – and pretty speedy.
Another deletion tool, the ‘Duplicate files remover’, is a little more worrying. Pointing the thing at my C: drive, it produced a list of ‘duplicates’ in groups, with the default action being to remove all but the newest. Unfortunately this included lots of important place-markers and other useful parts of the Windows system, the removal of which would have trashed various (admittedly mostly minor) functionalities. There was a warning that there were system files and folders included in the scanned area, but it would perhaps have been safer and more sensible to have excluded these automatically, or at least to have set the default to do nothing in sensitive areas and force the user to check them through. The tool seems useful for checking over large stashes of media, music files or pictures where duplicate copies of large files can easily start cluttering up disk space, but perhaps some more guidance would be useful.
Finally, there is a registry cleaner, which attempts to identify unneeded or ‘orphan’ registry entries and remove them. Again this sort of technology is notoriously tricky and prone to false positives, but can be useful; thoughtfully BitDefender also provides a ‘Registry restore’ tool, positioned just as prominently as the cleaner, to undo any catastrophic cleaning efforts.
Overall, BitDefender’s latest product leaves a pretty positive impression. It is hard to do justice in such a small amount of space and such a short time to the huge range of functions included here – several months would probably be needed to put all this through its many paces.
The redesigned interface is pretty successful – its simplicity is impressive, offering peace of mind for the inexperienced home user without the need for a degree course to operate it. In some places a little more clarity would be useful, particularly where the links to the help pages are concerned, but for the most part the basic console leaves little room for confusion. The duplicate remover could perhaps do with a little tweaking to eradicate any danger of causing damage, but the other tools require little more than clicking ‘fix’ and occasionally ‘next’. Despite my initial fears, there is a vast wealth of in-depth configuration available beneath the simple interface – enough to satisfy even the most hardened techie. The only thing I missed was the option to peruse logs of on-access monitoring, which is perhaps unlikely to be needed by anyone but a tester.
The main purpose of a security suite is to provide security, and this BitDefender does in spades, effortlessly spotting and blocking malware, controlling access to and from the network, flagging suspect websites and keeping an eye on emails. The cleaning angles may need a little more work to achieve perfection, but the backup tool is a splendid offering, particularly the grown-up version with the vast wealth of extra options. Hopefully, as this sort of thing becomes more and more common in security products, users will realise the importance of keeping secure copies of their important data. And once this message sinks in, with the gentle encouragement of products like this, backed up by powerful detection and protection, users’ data and systems will be more thoroughly secured.
Technical details: BitDefender Total Security 2008 was tested on: AMD K7, 500Mhz, with 512MB RAM and dual 10GB hard disks, running Microsoft Windows XP Professional SP2. Intel Pentium 4, 1.6Ghz, 512MB RAM, dual 20GB hard drives, 10/100 LAN connection, running Windows XP Professional SP2. AMD Athlon64, 3800+ dual core, 1GB RAM, 40GB and 200GB hard drives, 10/100 LAN connection, running Windows XP Professional SP2 (32-bit).