2010-10-01
Abstract
New anti-malware companies and products seem to be springing up with increasing frequency at the moment, many reworking existing detection engines into new forms, adding new functions, as well as several that are working on their own detection technology, aiming to take on the entrenched big names at their own game. John Hawes take a quick look at a few of the up-and-coming products which he expects to see taking part in the VB100 comparatives in the near future.
Copyright © 2010 Virus Bulletin
In recent months we have seen a remarkable increase in the numbers of products taking part in our comparative tests – with the record set at 60 in the XP test in April (see VB, April 2010, p.23), and the recent Vista test not far behind with 54 entries (see VB, August 2010, p.21). Altogether our summary chart showing the results of the last five tests has 68 different product entries. Our readers may be forgiven for suffering a little product fatigue – something with which the lab team is all too familiar. It may also seem reasonable to assume that the limit has been reached, that the market for security products is saturated and can take no more. Yet somehow new companies and products continue to emerge, many reworking existing detection engines into new forms, adding new functions, but also several that are working on their own detection technology, aiming to take on the entrenched big names at their own game.
In this article, we’ll take a quick look at a few of the up-and-coming products which we expect to see taking part in our comparatives in the near future. I should point out that the selection criteria for this list are rather ad hoc, and it represents no judgement on those products not yet listed; we have simply picked a few of the likely candidates from a much longer list, all of which have been suggested by their developers, or in some cases by their users, as potential VB100 participants.
Hailing from China, Antiy is a well-established firm set up in 2000. The company’s main website is at www.antiy.com, with a secondary site in English at www.antiy.net, mainly promoting its detection engine for integration in other projects, but also covering a large honeypot system which the firm operates in collaboration with a number of universities.
The company’s main desktop product has the unusual but somehow apposite name of Ghostbusters. We have had a few chances to play with it in recent months, and have observed a steady improvement in solidity and performance. The latest version, which we tried in mid-August, installs simply and smoothly, although it seems to have some issues with the UAC features in Windows Vista. It also still has a few stability issues when faced with some of the extreme stress testing we put products through in the lab, and a blue screen event was triggered while scanning a very large set of malicious items. Detection seems to be growing steadily over time, but still needs a little work to reach the required standard for VB100 certification – however, given its rate of growth, we can expect to see Antiy entering and doing well in our comparatives in the next year or so.
BluePex is the first solution to come to our attention from the malware hotspot that is Brazil. Its developers have already expressed interest in taking part in our comparatives and we have begun working with them on fine-tuning some of the product’s features to enable us to test it fully – not least in the area of logging. The company’s website (www.bluepex.com.br) tells us it has been around for at least 12 years, and offers a range of solutions including a firewall, VPN client, IM filtering and a virtual appliance. We have mainly been looking at the desktop product, which is only available in Portuguese at the moment, although an English translation will apparently be available soon.
The set-up process is pretty simple, although updating takes rather a long time from where our labs are based. The main interface combines a simple, easy-to-navigate design with fairly attractive but unflashy styling. Even with our limited understanding of the language we had no problems operating the product, which includes a firewall as well as the anti-malware component, and also has a gaming mode for minimal interruption of gamers. It seems to run very stably and scanning is remarkably fast; on-access protection seems to be on-write only (although it is possible that we missed an option in the GUI), and detection seems fairly decent in most areas. A little more work may be needed to get it up to the required standard for VB100 certification, but not much, and we expect to see BluePex included in a comparative very soon.
Bsecure is a US-based company, whose website, www.bsecure.com, promises ‘ultimate online family protection’. The company’s main focus, as you may have guessed from the strapline, is the filtering of online content to protect young, impressionable surfers, but the company also bundles anti-malware protection – provided by the McAfee engine – with a version of its product.
Once the small 2.8MB set-up file for the CloudCare product is downloaded (which was no mean feat, as we had some trouble getting at it with several browsers under Windows, and in the end resorted to Linux to fetch it down), the product is set up and ready to go almost instantly, which came as something of a surprise. Most of the control system appears to be online, with desktop shortcuts to the product opening the login page of the company site in a browser. From here, detailed controls of Internet filtering are available, along with controls for the anti-malware component. On-access scanning, which installed and began operation almost unnoticed, is provided on-write only to prevent the writing of malicious files to disk, but a thorough set of on-demand scanning is also offered, including scheduled scans.
With the McAfee engine at the heart of the product the product has no difficulty in covering our test sets, but we may need to work further with the company to enable us to complete some of the required tests without using the online control system – either way, we expect to see Bsecure’s CloudCare achieving VB100 status pretty soon.
Poland’s MKS_vir is another name that has been around for some time without making an appearance in the VB100 tests, and another about which we receive frequent queries. Having been in on-and-off contact with the developers for a while, we now have high hopes of seeing them making their debut very soon.
We looked at version 9 of the product, but a brand new version 10 is due out very soon, and it seems likely that it will be this that will be MKS’s first VB100 comparative entry. As far as version 9 goes, it seems to be well designed, with a nice touch of humour in the cartoon worm that adorns the main interface. We had a little confusion during the installation process when, despite having chosen English at the start of the install, the interface opened up in Polish. This was easily remedied however, and with ample controls on offer we had no problems running through a basic set of tests. Detection rates seemed pretty decent, and stability seemed fine too, with an excellent showing in our expanded clean sets.
With no issues from our end, MKS_vir is another which we hope to see in one of the next few comparative reviews.
Based in the Russian town of Bryansk, NANO is one of the youngest firms on our list, set up only last year, although the team behind it have apparently been working on the core technology of the solution for considerably longer. We have been monitoring the product for some time, and have been very impressed with the rapid curve of improvements we have observed.
The installer is slick and simple and brings up a very attractive, highly professional-looking interface. We found this very easy to navigate and a joy to work with, and it ran pretty stably through our basic tests. At one point we saw an error message claiming that some component had stopped working, but protection remained fully operational and scanning ran to completion, so it clearly managed to withstand the battering we put it through.
When we first looked at NANO some time ago there was clearly some work to do on detection rates, but the latest version put in a pretty impressive performance for such a young product; polymorphic viruses were particularly well covered, for which the developers deserve great credit. There will, of course, need to be further work, but at the rate at which it has been improving so far, we can expect a very creditable performance from NANO in a comparative review very soon indeed.
Optenet boasts headquarters in Florida, Spain and Australia (although the product’s EULA defines the company as Spanish), and according to the pages at www.optenet.com, it has been in business for more than a decade. The firm produces a range of mainly enterprise-level solutions, with mail and web filtering offered as both software and hardware solutions. The company’s desktop product is a pretty complete suite comprising all the standard firewall and anti-malware components, on top of a particularly well-designed and comprehensive-looking set of parental controls. An excellent granularity of filtering is offered here, by type, content and categories, as well as time slot controls, and a lockdown mode if multiple attempts are made to access banned resources.
The core of the malware protection is provided by the Kaspersky engine, and it seems to be well integrated into the product, providing the superb levels of detection we have come to expect from it. The serious and business-like interface provides excellent configuration in this area as well, and we found nothing to complain about in any of the basic tests we put it through. The developers have only to make the final decision to submit the product to be included in a VB100 comparative and doubtless it will do very well – we look forward to seeing an entry from Optenet very soon.
We have been aware of ParetoLogic for some time, and the company has previously been a sponsor of the annual VB conference, but we have had little opportunity to look closely at its solutions. Best known to us for its activities in the anti-spyware field, like many operating in that area the company also produces a full range of system optimization and recovery tools. The company is based on Vancouver Island in Canada, and has been in business for five years; its staff are very active in blogging and community work.
The company’s full anti-malware product is known as Anti-Virus PLUS, and although we only had time for the most cursory look over it, we observed a very slick and professional design ethos throughout. The installation process is simple and fast, and the GUI is attractive and glossy, with simple-to-access controls. Based on the filenames in the installed content and on some of the detection results we surmised that it includes a third-party engine, and from initial testing results we observed some pretty strong detection rates. More detail will have to wait until we see the product entered in a full comparative, which we hope to be able to persuade the developers to do in the very near future.
Founded in 2003 and operating from offices in the US and the Russian Federation, Security Stronghold is working on yet another all-new detection engine, and initial results look fairly promising. The company’s tagline is ‘security made easy’, and set-up and use is indeed fairly painless, with a simple, pastel-shaded interface which seems to provide all the required controls. Several runs through some basic detection tests have shown steady improvement in coverage, and in the main, stability seems fairly good, although we have had a few problems with the on-access component on some platforms.
The developers seem very keen for the product to be included in a VB100 comparative, and we hope to be able to add it to the line-up for one of the next few tests; given the steady rate of improvements, we can expect some good results pretty soon.
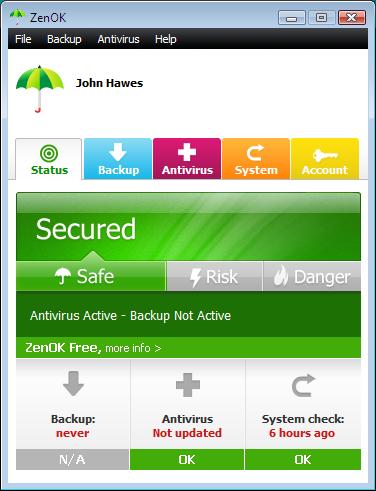
Last up in this little run-down of up-and-comers, ZenOK is one of the more unusual products we’ve seen in a while. Based on the BitDefender engine, the product aims for minimal system impact, and achieves this by offering on-write-only real-time protection, and by the possibly unique approach of running a continuous, low-priority on-demand scan covering the entire system. This can be disabled, or ‘snoozed’ as the GUI puts it, but otherwise it trundles away happily, slowly looking through the file system for nasties without making a serious dent on the processor or memory. Just how useful this is remains to be seen, but it is certainly an innovative approach.
The developers’ website at www.zenok.com gives away little about the firm, other than its charitable instincts – the product is given away free of charge, with the funding apparently coming from subscriptions to an online backup system controlled from the same, rather funky little interface. Initial tests showed up a few issues with testing – mainly with requirements specific to our tests such as detailed logging and the option to scan specific areas rather than whole file systems – but the developers have proven to be flexible and prompt in providing improvements, and look certain to enter a submission for a VB100 comparative very soon indeed. Given the engine underlying things, we expect to see a solid performance from this interesting product.
Of course, as they say, you ain’t seen nothing yet. This handful of products may only represent the tip of the iceberg, with more and more new players appearing on the scene almost daily. As I was writing this, yet another new name cropped up, based on a particular licensed engine which is threatening to dominate our comparatives with the number of offshoots it has given rise to, and there are many more that didn’t quite make this list (mainly thanks to developers being slow to provide their latest copies for us to play with and not offering trial downloads).
On top of that, there are a number of well-known and even major names which are not currently participating in VB100 testing, whether due to company marketing policies or due to problems handling the full gamut of WildList samples or both. All in all, we estimate that over 100 different anti-malware solutions are available, with a huge variation in approach and additional components. We can only hope they don’t all choose to take part in a comparative at once – while we are keen to provide our readers with a comprehensive insight into the quality of products out there, trying to cover them all in a single month might just be too much for us.