2011-09-01
Abstract
Qakbot’s ability to propagate via network shares is enough to cripple an entire network. Add to that the ability to compromise websites and you have a recipe for a highly successful malware attack. Jessa Dela Torre discusses the different ways in which Qakbot variants arrive on and infect systems, how these affect users, and how the security industry can help mitigate Qakbot system infections.
Copyright © 2011 Virus Bulletin
The recent security breaches at the Massachusetts Departments of Unemployment Assistance and Career Services [1] revived public interest in Qakbot (aka Qbot or Pinkslipbot), the malware family that has been responsible for infiltrating thousands of systems worldwide during its four-year stint [2].
At Trend Micro we have received several escalations with regard to this particular malware family from various enterprise customers in the healthcare, financial, government, and other sectors.
We came across a new Qakbot variant in the latter part of February this year [3]. Like its predecessors, this variant propagates primarily via network shares. The malware has also undergone a structural revamp and added a new infection vector, so it came as no surprise when news of massive Qakbot network infections broke. Armed with more effective means of infection, the malware quickly spread worldwide, leaving an indelible mark on the threat landscape.
Qakbot’s ability to propagate via network shares is enough to cripple an entire network. Add to that the ability to compromise websites and you seemingly have a recipe for a highly successful malware attack.
This paper will discuss the different ways in which Qakbot variants arrive on and infect systems, how these affect users, and how the security industry can help mitigate Qakbot system infections.
First-generation Qakbot variants can be distinguished based on their file and folder names, which usually include the string ‘_qbot’. These store their components in password-protected .ZIP files that their main components download from certain sites.
To make system infections less obvious, next-generation Qakbot variants started using random file and folder names. Their package files also ditched password protection and started taking the social engineering route, using file names such as ‘resume.doc’.
As the security industry caught on and started being able to detect Qakbot successfully, the malware’s creators introduced another new breed of variants with a few significant changes.
First, they no longer made use of an archive file, instead packaging every component in a single .EXE file. Next, they added a new propagation vector: USB drives.
Early Qakbot variants exploited software vulnerabilities in order to infect systems. They particularly took advantage of the Collab.collectEmailInfo and Collab.getIcon vulnerabilities in certain versions of Adobe Acrobat and Adobe Reader via malicious PDF files. More recent variants have been found to arrive via three infection vectors: removable drives, default network shares and as drive-by downloads from compromised sites.
The USB port is perhaps any system’s weakest point in terms of network security since no firewall or network policies can be enforced to maintain the integrity of a removable drive. Typically, office employees use USB drives when performing their daily tasks. This is probably the reason why cybercriminals continue to use malware that spreads via removable drives. In fact, so-called USB malware such as the Palevo [4], Qakbot [5] and Vobfus [6] worms continues to reign on Trend Micro’s list of most notorious malware types.
Earlier Qakbot variants did not have the ability to spread via removable drives. The malware’s authors probably realized how successful other USB malware had been and decided to include the ability to spread via removable drives in more recent versions of Qakbot.
Unlike other USB malware, however, Qakbot variants do not use an autorun.inf file. Instead they rely on crafty social engineering techniques and on the tendency for users to unwittingly execute files.
Whenever a USB drive is plugged into an infected system, the Qakbot variant will select a file from the drive’s contents and drop a copy of itself onto the system using the chosen file’s name in the following format (Figure 4):
{malware’s file name}_{selected file’s name}.exe
If the USB drive is empty, the malware will just append ‘_Documents’ to its own file name (Figure 5):
{malware’s file name}_Documents.exe
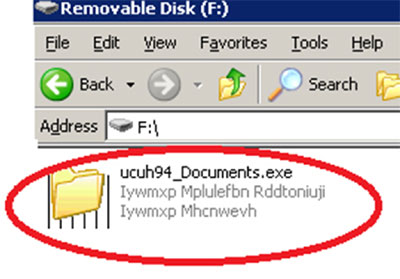
Figure 5. Copy of the malware that will be dropped from the infected USB drive onto the user’s system.
Once clicked, the copy of the Qakbot variant will then perform its malicious routines. If this happens to a system that is connected to a network, the Qakbot infection will spread to all of the systems on the network.
The default administrative network shares on Windows are created by each system. As such, deleted shares will reappear whenever a system reboots. Qakbot variants make use of these default shares to propagate across a network. To do so, they initially enumerate all of the available resources. They then attempt to establish connections based on the affected user’s rights.
Before dropping a copy of itself onto a system, the Qakbot variant will first check the following:
Whether the resource belongs to its current host
Whether the target host is already infected (by checking the nbl section of its configuration file).
If both are untrue, the malware will drop a copy of itself onto C$ or Admin$ – both of which are default shares – and start a remote service in order to execute the file it dropped. It uses SMB over TCP to access the target resource and to send a copy of itself to connected systems.
Click here for a larger version of Figure 6.
The Qakbot variant then binds the SVCCTL interface to start a remote service using the following command:
%path%\{file name}.exe /s
Since first-generation Qakbot variants reared their ugly heads, part of their distribution routine has been the ability to inject malicious scripts into files stored on web servers. To do this, they initially attempt to contact a command-and-control (C&C) server in order to get a command file that is saved as %User Temp%\~{random name}.tmp. This file contains the FTP credentials the malware needs in order to perform its script injection routine. Once connected, it downloads files with the following extension names:
.php
.htm
.asp
.pl
.cfm
The malware then inserts a malicious script before the </body> tag, which serves as a link to one of its download sites. It then re-uploads the infected files to the web servers. These then effectively infect the systems of users who visit compromised sites. The download link can lead to a copy of the main Qakbot executable file or to its JavaScript component.
Click here for a larger version of Figure 7.
Once inside a system, Qakbot monitors substrings related to financial institutions such as Bank of America, Fifth Third, Wells Fargo and Citibank, among others. The malware also gathers the following information:
System information
IP address
Domain Name System (DNS) name
Host name
User name
Domain
User privilege
OS version
Network interfaces (i.e. address, netmask and status)
Installed software
Protected storage
Account name
Connection type
POP3 (i.e. username, server and password)
SMTP (i.e. server and email addresses)
Internet Explorer (IE) and Flash Player cookies
Certificates
Web server credentials (i.e. usernames and passwords)
Keystrokes
All of the aforementioned information is sent to Qakbot-controlled FTP sites. Sometimes the data in these FTP sites remains for a few days and builds up to quite a sizeable amount.
Given the type of data Qakbot collects, an organization stands to lose a lot of business-critical information related both to the organization itself and its clients. Data exposure not only leads to bad publicity but can also plant a sense of distrust in an organization’s ability to protect its resources.
The bulk of responsibility falls into the hands of system administrators. Securing a network and enforcing strong policies are just some of the things they have to worry about. Cleaning up after system or network infections is another story. A Qakbot-infested network will require a lot of work and specialized tools to remove the malware.
The extent of Qakbot infections does not rely on state-of-the-art propagation routines. Security researchers may even argue that Qakbot’s method of spreading is not new and is certainly not that complex. The variants do not exploit zero-day or even run-of-the-mill vulnerabilities. Instead they bank on social engineering tactics and poor network security – both of which can be prevented if system administrators are more aware and better prepared for malicious attacks.
Qakbot variants were originally designed to infiltrate systems for the sole purpose of gathering as much information as possible. They currently utilize three of the most widely used infection vectors. Improved strains also ensure greater revenue for malware authors, which may eventually lead to a new batch of variants with even better functionality.
The most recently discovered Qakbot configuration files have an entry dubbed peer-to-peer (P2P) node list, which points to a URL. The URL is not currently accessible, but we can expect the link to be activated as soon as a new batch of Qakbot variants is rolled out.
The following safe computing practices can help system administrators protect their organizations’ networks against Qakbot-related attacks.
Qakbot’s ability to spread via default network shares allows it to instigate mass network infections. System administrators should keep in mind that the malware’s access to network resources is dependent on the affected users’ system privileges. As such, they should limit users’ administrative rights and should issue write permissions conservatively. Users should only be assigned the lowest level of privilege required to complete their tasks. Password protecting network shares is also a good idea to combat the threats Qakbot poses.
It is important to educate users about securing and utilizing company resources properly, particularly removable drives and Internet access.
We have seen several instances in which Qakbot variants have infected systems via removable drives. Security awareness is a critical element of safe computing.
Since Qakbot has the ability to easily compromise sites, the fact that a site is visited frequently or well known is no guarantee of its safety. In fact, popular sites may even present greater risk.
Users must be extra careful when clicking links. Some security solutions feature a web reputation service functionality which will block access to malicious sites and mitigate web-based attacks. Figure 8 shows Trend Micro’s web reputation service blocking the web browser from visiting a known malicious site.
Google’s Safe Browsing service [7] is another useful tool for safer web browsing. This and similar services provide information on a site’s integrity, including its involvement, if any, with malicious activities (Figure 9).
As malware authors continually improve their malicious wares to evade even the best scanners, so must security firms constantly update their anti-virus signatures to mitigate Qakbot infections.
System administrators are advised to download and install security patches as soon as they are made available. This will help defend systems and networks against vulnerability exploit attacks.
System administrators are strongly advised to install security appliances that will help them monitor network activities.
Several kinds of intrusion detection systems (IDS) and intrusion prevention systems (IPS) are available on the market. System administrators should ensure that the devices they install on their company networks are capable of identifying, blocking and reporting any and all kinds of suspicious activities.
Even though these practices may not make a system or a network Qakbot-proof, they will definitely lower the chances of infection. Given that Qakbot is after almost every kind of data in a system or in a network, following the aforementioned tips certainly would not hurt.
Qakbot variants are primarily known for two things – their huge appetite for confidential data and their ability to rapidly spread across networks – the combination of which can spell disaster for affected users.
Qakbot infections not only put the affected user’s personal information at risk, they also put corporate data on the affected user’s system or on the network in grave danger of being compromised. The recent enhancements to Qakbot’s distribution routines have immensely increased the malware’s notoriety.
Network security plays a pivotal role in containing Qakbot infections. Good heuristic or generic signatures can prevent the malware from running on systems and from spreading across networks. Note, however, that since Qakbot variants are known for changing their structure, file-based detection alone may prove ineffective. Using a combination of file- and behaviour-based detection ‘in the cloud’ [8] may, in the end, be the best solution to counter the ever-persistent Qakbot threat.